下载文件并解压,发现压缩包里有三段密文以及一个公钥
看到public.key以后用kali linux里的openssl查看
查看一下openssl 中rsa的相关命令
root@kali:~/Desktop# openssl rsa -help
Usage: rsa [options]
Valid options are:
-help Display this summary
-inform format Input format, one of DER NET PEM
-outform format Output format, one of DER NET PEM PVK
-in val Input file
-out outfile Output file
-pubin Expect a public key in input file
-pubout Output a public key
-passout val Output file pass phrase source
-passin val Input file pass phrase source
-RSAPublicKey_in Input is an RSAPublicKey
-RSAPublicKey_out Output is an RSAPublicKey
-noout Don‘t print key out
-text Print the key in text
-modulus Print the RSA key modulus
-check Verify key consistency
-* Any supported cipher
-pvk-strong Enable ‘Strong‘ PVK encoding level (default)
-pvk-weak Enable ‘Weak‘ PVK encoding level
-pvk-none Don‘t enforce PVK encoding
-engine val Use engine, possibly a hardware device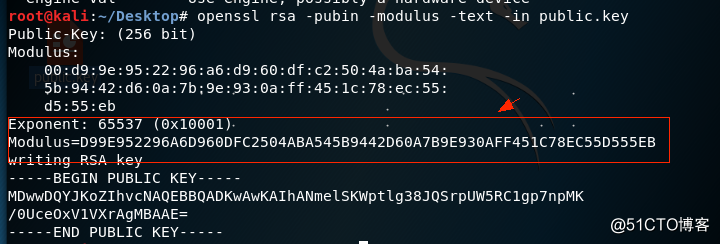
因为N是十六进制数 所以得把N转换成十进制才能用在线分解网站将其分解
root@kali:~/Desktop# python
Python 2.7.15 (default, Jul 28 2018, 11:29:29)
[GCC 8.1.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> Modulus=0xD99E952296A6D960DFC2504ABA545B9442D60A7B9E930AFF451C78EC55D555EB
>>> Modulus
98432079271513130981267919056149161631892822707167177858831841699521774310891L
将n进行因式分解来得到我们的p和q (推荐使用http://factordb.com/)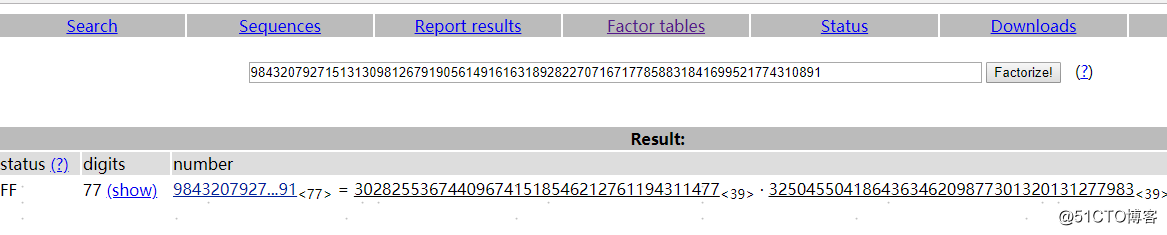
import gmpy2
import rsa
p = 302825536744096741518546212761194311477
q = 325045504186436346209877301320131277983
n = p * q
e = 65537
d = int(gmpy2.invert(e , (p-1) * (q-1)))
privatekey = rsa.PrivateKey(n , e , d , p , q)
with open("encrypted.message1" , "rb") as f:
print(rsa.decrypt(f.read(), privatekey).decode())
with open("encrypted.message2" , "rb") as f:
print(rsa.decrypt(f.read(), privatekey).decode())
with open("encrypted.message3" , "rb") as f:
print(rsa.decrypt(f.read(), privatekey).decode())原文:http://blog.51cto.com/11834557/2324960