1.ida打开得到main():
1 __int64 __fastcall main(__int64 a1, char **a2, char **a3) 2 { 3 __useconds_t *v3; // rbp 4 unsigned int v4; // eax 5 int *v5; // rcx 6 int v6; // edx 7 unsigned int v7; // eax 8 bool v8; // zf 9 signed __int64 v9; // rcx 10 __int64 v10; // rax 11 char v11; // bl 12 char v12; // dl 13 void (**v13)(void *); // rbp 14 char *v14; // r12 15 pthread_t *v15; // r13 16 void (*v16)(void *); // rdi 17 unsigned __int64 i; // rcx 18 char v18; // al 19 int *v19; // rdx 20 int v20; // esi 21 unsigned int v21; // eax 22 unsigned __int64 v22; // rdx 23 char *v23; // rax 24 signed __int64 v24; // rdx 25 char v25; // di 26 27 v3 = useconds; 28 v4 = time(0LL); 29 srand(v4); 30 do 31 { 32 ++v3; 33 *(v3 - 1) = 100 * (rand() % 1000); 34 } 35 while ( v3 != &unk_602208 ); 36 __isoc99_scanf("%63s", dword_602180); 37 v5 = dword_602180; 38 do 39 { 40 v6 = *v5; 41 ++v5; 42 v7 = ~v6 & (v6 - 16843009) & 0x80808080; 43 } 44 while ( !v7 ); 45 v8 = (v7 & 0x8080) == 0; 46 if ( !(v7 & 0x8080) ) 47 LOBYTE(v7) = BYTE2(v7); 48 if ( v8 ) 49 v5 = (v5 + 2); 50 v9 = v5 - (dword_602180 + __CFADD__(v7, v7) + 3); 51 v10 = 0LL; 52 v11 = 0; 53 while ( v9 != v10 ) 54 { 55 v12 = *(dword_602180 + v10) + v10; 56 ++v10; 57 v11 ^= v12; 58 } 59 v13 = &newthread; 60 v14 = 0LL; 61 v15 = &newthread; 62 do 63 { 64 if ( pthread_create(v15, 0LL, start_routine, v14) ) 65 { 66 perror("pthread_create"); 67 exit(-1); 68 } 69 ++v14; 70 ++v15; 71 } 72 while ( v14 != 6 ); 73 do 74 { 75 v16 = *v13; 76 ++v13; 77 pthread_join(v16, 0LL); 78 } 79 while ( &free != v13 ); 80 for ( i = 0LL; ; byte_60221F[i] = v11 ^ byte_6020DF[i] ^ v18 ) 81 { 82 v19 = dword_602180; 83 do 84 { 85 v20 = *v19; 86 ++v19; 87 v21 = ~v20 & (v20 - 16843009) & 0x80808080; 88 } 89 while ( !v21 ); 90 if ( !(~v20 & (v20 - 257) & 0x8080) ) 91 LOBYTE(v21) = (~v20 & (v20 - 16843009) & 0x80808080) >> 16; 92 if ( !(~v20 & (v20 - 257) & 0x8080) ) 93 v19 = (v19 + 2); 94 v22 = v19 - (dword_602180 + __CFADD__(v21, v21) + 3); 95 if ( v22 <= i ) 96 break; 97 v18 = *(dword_602220 + i++); 98 } 99 if ( v22 ) 100 { 101 if ( (LOBYTE(dword_602220[0]) - 48) > 74u ) 102 { 103 LABEL_32: 104 puts("Badluck! There is no flag"); 105 return 0LL; 106 } 107 v23 = dword_602220 + 1; 108 v24 = v22 + 6300192; 109 while ( v23 != v24 ) 110 { 111 v25 = *v23++; 112 if ( (v25 - 48) > 0x4Au ) 113 goto LABEL_32; 114 } 115 } 116 __printf_chk(1LL, "Here is the flag:%s\n", dword_602220); 117 return 0LL; 118 }
可以从代码得到:
1 do 2 { 3 if ( pthread_create(v15, 0LL, start_routine, v14) ) 4 { 5 perror("pthread_create"); 6 exit(-1); 7 } 8 ++v14; 9 ++v15; 10 } 11 while ( v14 != 6 );
在此处创建了6个新的线程。
2.通过gdb的动态调试可以得知,程序把输入的字符串每4个分为一组。加上创建了6个线程,猜测输入字符串长度为24。
线程代码:
1 unsigned __int64 __fastcall start_routine(void *a1) 2 { 3 __int64 v1; // rbp 4 int v2; // ebx 5 __useconds_t v3; // edi 6 __int64 v4; // rbx 7 int v5; // eax 8 __int64 v6; // rdx 9 __int64 v8; // [rsp+0h] [rbp-38h] 10 unsigned __int64 v9; // [rsp+18h] [rbp-20h] 11 12 v1 = a1; 13 v2 = a1; 14 v3 = useconds[a1]; 15 v9 = __readfsqword(0x28u); 16 v4 = v2; 17 usleep(v3); 18 pthread_mutex_lock(&mutex); 19 sub_400E10(&dword_602180[v4], 4uLL, &v8); 20 v5 = dword_6021E8; 21 22 v6 = dword_6021E8; 23 if ( v8 == qword_602120[v1] ) 24 dword_602220[v6] = dword_602180[v4]; 25 else 26 dword_602220[v6] = 0; 27 dword_6021E8 = v5 + 1; 28 pthread_mutex_unlock(&mutex); 29 return __readfsqword(0x28u) ^ v9; 30 }
通过gdb调试知道,函数sub_400E10()为md5加密函数,传入参数为被分组的字符串的一组。所以线程的功能是把字符串md5加密后再与qword_602120[]数组进行对比。如果正确就把字符串赋值给一个全局数组变量,此变量在后面的flag的计算中需要使用。另外qword_602120[]数组为小端序储存,而且第一个线程的对比是qword_602120[0],如此类推。通过py脚本爆破出字符串。
1 import hashlib 2 import multiprocessing 3 answer=[‘4746bbbd02bb590f‘, ‘beac2821ece8fc5c‘, ‘ad749265ca7503ef‘, ‘4386b38fc12c4227‘, ‘b03ecc45a7ec2da7‘, ‘bE3c5ffe121734e8‘] 4 5 def cal_1(): 6 for i in range(32, 50): 7 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 8 flag[0] = chr(i) 9 for j in range(32, 50): 10 flag[1] = chr(j) 11 for k in range(32, 127): 12 flag[2] = chr(k) 13 for l in range(32, 127): 14 flag[3] = chr(l) 15 result = ‘‘.join(flag) 16 flag_md5 = hashlib.md5() 17 flag_md5.update(result.encode(encoding=‘utf-8‘)) 18 if flag_md5.hexdigest()[0:16] == answer[0]: 19 print(result) 20 21 def cal_2(): 22 for i in range(50, 75): 23 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 24 flag[0] = chr(i) 25 for j in range(32, 50): 26 flag[1] = chr(j) 27 for k in range(32, 127): 28 flag[2] = chr(k) 29 for l in range(32, 127): 30 flag[3] = chr(l) 31 result = ‘‘.join(flag) 32 flag_md5 = hashlib.md5() 33 flag_md5.update(result.encode(encoding=‘utf-8‘)) 34 if flag_md5.hexdigest()[0:16] == answer[0]: 35 print(result) 36 37 def cal_3(): 38 for i in range(75, 100): 39 flag = [‘0‘,‘0‘,‘0‘,‘0‘] 40 flag[0] = chr(i) 41 for j in range(32, 50): 42 flag[1] = chr(j) 43 for k in range(32, 127): 44 flag[2] = chr(k) 45 for l in range(32, 127): 46 flag[3] = chr(l) 47 result=‘‘.join(flag) 48 flag_md5 = hashlib.md5() 49 flag_md5.update(result.encode(encoding=‘utf-8‘)) 50 if flag_md5.hexdigest()[0:16] == answer[0]: 51 print(result) 52 53 def cal_4(): 54 for i in range(100, 127): 55 flag = [‘0‘,‘0‘,‘0‘,‘0‘] 56 flag[0] = chr(i) 57 for j in range(32, 50): 58 flag[1] = chr(j) 59 for k in range(32, 127): 60 flag[2] = chr(k) 61 for l in range(32, 127): 62 flag[3] = chr(l) 63 result=‘‘.join(flag) 64 flag_md5 = hashlib.md5() 65 flag_md5.update(result.encode(encoding=‘utf-8‘)) 66 if flag_md5.hexdigest()[0:16] == answer[0]: 67 print(result) 68 69 def cal_5(): 70 for i in range(32, 50): 71 flag = [‘0‘,‘0‘,‘0‘,‘0‘] 72 flag[0] = chr(i) 73 for j in range(50, 75): 74 flag[1] = chr(j) 75 for k in range(32, 127): 76 flag[2] = chr(k) 77 for l in range(32, 127): 78 flag[3] = chr(l) 79 result=‘‘.join(flag) 80 flag_md5 = hashlib.md5() 81 flag_md5.update(result.encode(encoding=‘utf-8‘)) 82 if flag_md5.hexdigest()[0:16] == answer[0]: 83 print(result) 84 85 def cal_6(): 86 for i in range(50, 75): 87 flag = [‘0‘,‘0‘,‘0‘,‘0‘] 88 flag[0] = chr(i) 89 for j in range(50, 75): 90 flag[1] = chr(j) 91 for k in range(32, 127): 92 flag[2] = chr(k) 93 for l in range(32, 127): 94 flag[3] = chr(l) 95 result=‘‘.join(flag) 96 flag_md5 = hashlib.md5() 97 flag_md5.update(result.encode(encoding=‘utf-8‘)) 98 if flag_md5.hexdigest()[0:16] == answer[0]: 99 print(result) 100 101 102 def cal_7(): 103 for i in range(75, 100): 104 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 105 flag[0] = chr(i) 106 for j in range(50, 75): 107 flag[1] = chr(j) 108 for k in range(32, 127): 109 flag[2] = chr(k) 110 for l in range(32, 127): 111 flag[3] = chr(l) 112 result = ‘‘.join(flag) 113 flag_md5 = hashlib.md5() 114 flag_md5.update(result.encode(encoding=‘utf-8‘)) 115 if flag_md5.hexdigest()[0:16] == answer[0]: 116 print(result) 117 118 119 def cal_8(): 120 for i in range(100, 127): 121 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 122 flag[0] = chr(i) 123 for j in range(50, 75): 124 flag[1] = chr(j) 125 for k in range(32, 127): 126 flag[2] = chr(k) 127 for l in range(32, 127): 128 flag[3] = chr(l) 129 result = ‘‘.join(flag) 130 flag_md5 = hashlib.md5() 131 flag_md5.update(result.encode(encoding=‘utf-8‘)) 132 if flag_md5.hexdigest()[0:16] == answer[0]: 133 print(result) 134 135 136 def cal_9(): 137 for i in range(32, 50): 138 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 139 flag[0] = chr(i) 140 for j in range(75, 100): 141 flag[1] = chr(j) 142 for k in range(32, 127): 143 flag[2] = chr(k) 144 for l in range(32, 127): 145 flag[3] = chr(l) 146 result = ‘‘.join(flag) 147 flag_md5 = hashlib.md5() 148 flag_md5.update(result.encode(encoding=‘utf-8‘)) 149 if flag_md5.hexdigest()[0:16] == answer[0]: 150 print(result) 151 152 153 def cal_10(): 154 for i in range(50, 75): 155 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 156 flag[0] = chr(i) 157 for j in range(75, 100): 158 flag[1] = chr(j) 159 for k in range(32, 127): 160 flag[2] = chr(k) 161 for l in range(32, 127): 162 flag[3] = chr(l) 163 result = ‘‘.join(flag) 164 flag_md5 = hashlib.md5() 165 flag_md5.update(result.encode(encoding=‘utf-8‘)) 166 if flag_md5.hexdigest()[0:16] == answer[0]: 167 print(result) 168 169 170 def cal_11(): 171 for i in range(75, 100): 172 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 173 flag[0] = chr(i) 174 for j in range(75, 100): 175 flag[1] = chr(j) 176 for k in range(32, 127): 177 flag[2] = chr(k) 178 for l in range(32, 127): 179 flag[3] = chr(l) 180 result = ‘‘.join(flag) 181 flag_md5 = hashlib.md5() 182 flag_md5.update(result.encode(encoding=‘utf-8‘)) 183 if flag_md5.hexdigest()[0:16] == answer[0]: 184 print(result) 185 186 187 def cal_12(): 188 for i in range(100, 127): 189 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 190 flag[0] = chr(i) 191 for j in range(75, 100): 192 flag[1] = chr(j) 193 for k in range(32, 127): 194 flag[2] = chr(k) 195 for l in range(32, 127): 196 flag[3] = chr(l) 197 result = ‘‘.join(flag) 198 flag_md5 = hashlib.md5() 199 flag_md5.update(result.encode(encoding=‘utf-8‘)) 200 if flag_md5.hexdigest()[0:16] == answer[0]: 201 print(result) 202 203 204 def cal_13(): 205 for i in range(32, 50): 206 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 207 flag[0] = chr(i) 208 for j in range(100, 127): 209 flag[1] = chr(j) 210 for k in range(32, 127): 211 flag[2] = chr(k) 212 for l in range(32, 127): 213 flag[3] = chr(l) 214 result = ‘‘.join(flag) 215 flag_md5 = hashlib.md5() 216 flag_md5.update(result.encode(encoding=‘utf-8‘)) 217 if flag_md5.hexdigest()[0:16] == answer[0]: 218 print(result) 219 220 221 def cal_14(): 222 for i in range(50, 75): 223 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 224 flag[0] = chr(i) 225 for j in range(100, 127): 226 flag[1] = chr(j) 227 for k in range(32, 127): 228 flag[2] = chr(k) 229 for l in range(32, 127): 230 flag[3] = chr(l) 231 result = ‘‘.join(flag) 232 flag_md5 = hashlib.md5() 233 flag_md5.update(result.encode(encoding=‘utf-8‘)) 234 if flag_md5.hexdigest()[0:16] == answer[0]: 235 print(result) 236 237 238 def cal_15(): 239 for i in range(75, 100): 240 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 241 flag[0] = chr(i) 242 for j in range(100, 127): 243 flag[1] = chr(j) 244 for k in range(32, 127): 245 flag[2] = chr(k) 246 for l in range(32, 127): 247 flag[3] = chr(l) 248 result = ‘‘.join(flag) 249 flag_md5 = hashlib.md5() 250 flag_md5.update(result.encode(encoding=‘utf-8‘)) 251 if flag_md5.hexdigest()[0:16] == answer[0]: 252 print(result) 253 254 255 def cal_16(): 256 for i in range(100, 127): 257 flag = [‘0‘, ‘0‘, ‘0‘, ‘0‘] 258 flag[0] = chr(i) 259 for j in range(100, 127): 260 flag[1] = chr(j) 261 for k in range(32, 127): 262 flag[2] = chr(k) 263 for l in range(32, 127): 264 flag[3] = chr(l) 265 result = ‘‘.join(flag) 266 flag_md5 = hashlib.md5() 267 flag_md5.update(result.encode(encoding=‘utf-8‘)) 268 if flag_md5.hexdigest()[0:16] == answer[0]: 269 print(result) 270 271 272 if __name__ =="__main__": 273 p1=multiprocessing.Process(target=cal_1(),args=(2,)) 274 p2=multiprocessing.Process(target=cal_2(),args=(3,)) 275 p3=multiprocessing.Process(target=cal_3(),args=(4,)) 276 p4=multiprocessing.Process(target=cal_4(),args=(5,)) 277 p5=multiprocessing.Process(target=cal_5(),args=(6,)) 278 p6=multiprocessing.Process(target=cal_6(),args=(7,)) 279 p7=multiprocessing.Process(target=cal_7(),args=(8,)) 280 p8=multiprocessing.Process(target=cal_8(),args=(9,)) 281 p9=multiprocessing.Process(target=cal_9(),args=(10,)) 282 p10= multiprocessing.Process(target=cal_10(), args=(11,)) 283 p11= multiprocessing.Process(target=cal_11(), args=(12,)) 284 p12= multiprocessing.Process(target=cal_12(), args=(13,)) 285 p13= multiprocessing.Process(target=cal_13(), args=(14,)) 286 p14= multiprocessing.Process(target=cal_14(), args=(15,)) 287 p15= multiprocessing.Process(target=cal_15(), args=(16,)) 288 p16= multiprocessing.Process(target=cal_16(), args=(17,)) 289 p1.start() 290 p2.start() 291 p3.start() 292 p4.start() 293 p5.start() 294 p6.start() 295 p7.start() 296 p8.start() 297 p9.start() 298 p10.start() 299 p11.start() 300 p12.start() 301 p13.start() 302 p14.start() 303 p15.start() 304 p16.start()
这个脚本只能一个组爆破,需要在爆破完一个后手动修改answer[i]数组的i来爆破出6个组。最后得到输入字符串"juhuhfenlapsiuerhjifdunu"
3.因为此题有多解,需要在linux上用shell。
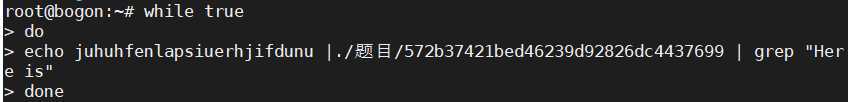
运行后得到一堆解,最后根据语义得到flag:goodjobyougetthisflag233
原文:https://www.cnblogs.com/mio-yy/p/12503124.html