攻防世界题目:
题目描述:菜鸡学逆向学得头皮发麻,终于它拿到了一段源代码
源代码如下
#include <stdio.h> #include <string.h> int main(int argc, char *argv[]) { if (argc != 4) { printf("what?\n"); exit(1); } unsigned int first = atoi(argv[1]); if (first != 0xcafe) { printf("you are wrong, sorry.\n"); exit(2); } unsigned int second = atoi(argv[2]); if (second % 5 == 3 || second % 17 != 8) { printf("ha, you won‘t get it!\n"); exit(3); } if (strcmp("h4cky0u", argv[3])) { printf("so close, dude!\n"); exit(4); } printf("Brr wrrr grr\n"); unsigned int hash = first * 31337 + (second % 17) * 11 + strlen(argv[3]) - 1615810207; printf("Get your key: "); printf("%x\n", hash); return 0; }
分析代码可以知道,要求输入四个参数,即文件名.exe 参数1 参数2 参数3
if (argc != 4) { printf("what?\n"); exit(1); }
第二个参数要求为0xcafe 即为51966
unsigned int first = atoi(argv[1]); if (first != 0xcafe) { printf("you are wrong, sorry.\n"); exit(2); }
第三个参数对5取余不能为3,且对17取余等于8,则25即可
unsigned int second = atoi(argv[2]); if (second % 5 == 3 || second % 17 != 8) //对5取余等于3,且对17取余不等于8 { printf("ha, you won‘t get it!\n"); exit(3); }
第四个参数为h4cky0u
if (strcmp("h4cky0u", argv[3])) {
printf("so close, dude!\n");
exit(4);
}
则最后运行命令a.exe 51966 25 h4cky0u
得到flag : Get your key: c0ffee
题目描述:菜鸡拿到了一个被加壳的二进制文件
在VScode中安装插件hexdump for VScode
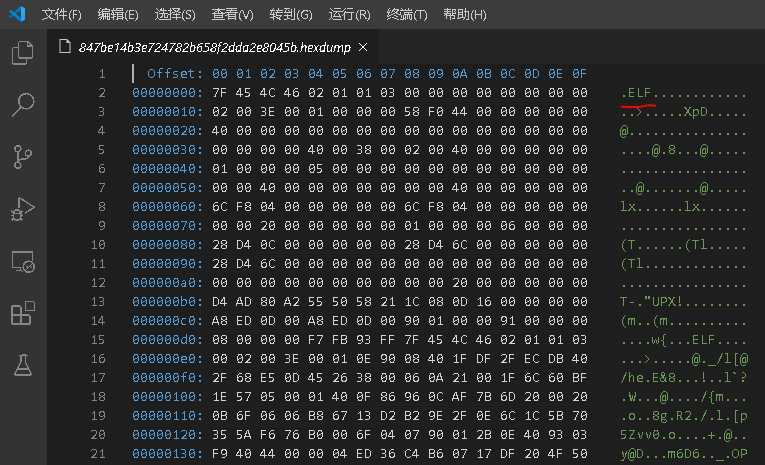
则可以看出为elf文件,即为一个可在Linux下的可执行文件
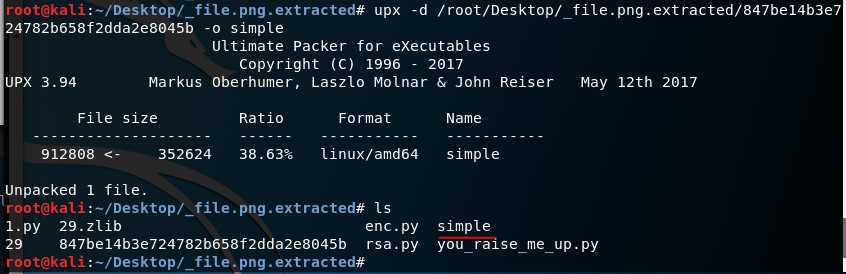
用kali的upx工具对其进行脱壳,命令为upx -d/路径/源文件名 -o 脱壳文件名
用IDA将脱壳后的文件打开
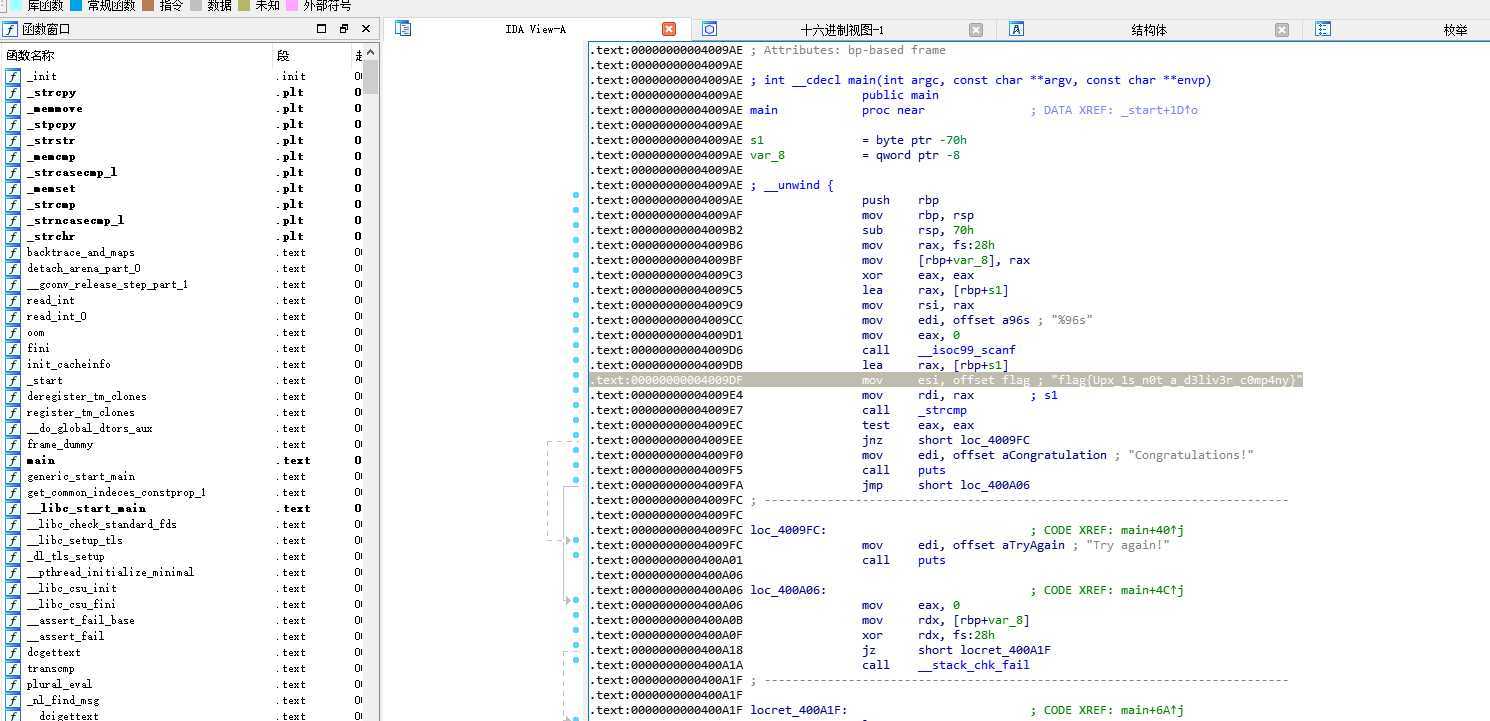
在main函数中往下翻,就看到flag了
flag{Upx_1s_n0t_a_d3liv3r_c0mp4ny}
题目描述:菜鸡开始接触一些基本的算法逆向了
用ida打开后,在main函数中点击f5反编译为c语言
void __fastcall __noreturn main(__int64 a1, char **a2, char **a3) { size_t v3; // rsi int i; // [rsp+3Ch] [rbp-54h] char s[36]; // [rsp+40h] [rbp-50h] int v6; // [rsp+64h] [rbp-2Ch] __int64 v7; // [rsp+68h] [rbp-28h] char v8[8]; // [rsp+70h] [rbp-20h] int v9; // [rsp+8Ch] [rbp-4h] v9 = 0; strcpy(v8, ":\"AL_RT^L*.?+6/46"); v7 = 28537194573619560LL; v6 = 7; printf("Welcome to the RC3 secure password guesser.\n", a2, a3); printf("To continue, you must enter the correct password.\n"); printf("Enter your guess: "); __isoc99_scanf("%32s", s); v3 = strlen(s); if ( v3 < strlen(v8) ) sub_4007C0(v8); for ( i = 0; i < strlen(s); ++i ) { if ( i >= strlen(v8) ) ((void (*)(void))sub_4007C0)(); if ( s[i] != (char)(*((_BYTE *)&v7 + i % v6) ^ v8[i]) ) ((void (*)(void))sub_4007C0)(); } sub_4007F0(); }
进入sub_4007C0(v8),则
void __noreturn sub_4007C0() { printf("Incorrect password!\n"); exit(0); }
进入 ((void ()(void))sub_4007C0)();则
void __noreturn sub_4007C0() { printf("Incorrect password!\n"); exit(0);
}
进入 ((void ()(void))sub_4007C0)();则
void __noreturn sub_4007C0() { printf("Incorrect password!\n"); exit(0); }
那么,获得flag的语句为
if ( s[i] != (char)(*((_BYTE *)&v7 + i % v6) ^ v8[i]) )
sub_4007C0();
则写代码
#include<stdio.h> #include<string.h> #define BYTE unsigned char int main() { int i; // [rsp+3Ch] [rbp-54h] char s[36]=""; // [rsp+40h] [rbp-50h] int v6; // [rsp+64h] [rbp-2Ch] __int64 v7; // [rsp+68h] [rbp-28h] int v9; // [rsp+8Ch] [rbp-4h] v9 = 0; char v8[18]=":\"AL_RT^L*.?+6/46"; v7 = 28537194573619560LL; v6 = 7;//复制题目 for ( i = 0; i < strlen(v8); ++i )//跳过前面的语句 { s[i] = (char)(*((BYTE *)&v7 + i % v6) ^ v8[i]); } printf("%s\n",s); }
运行得flag:RC3-2016-XORISGUD
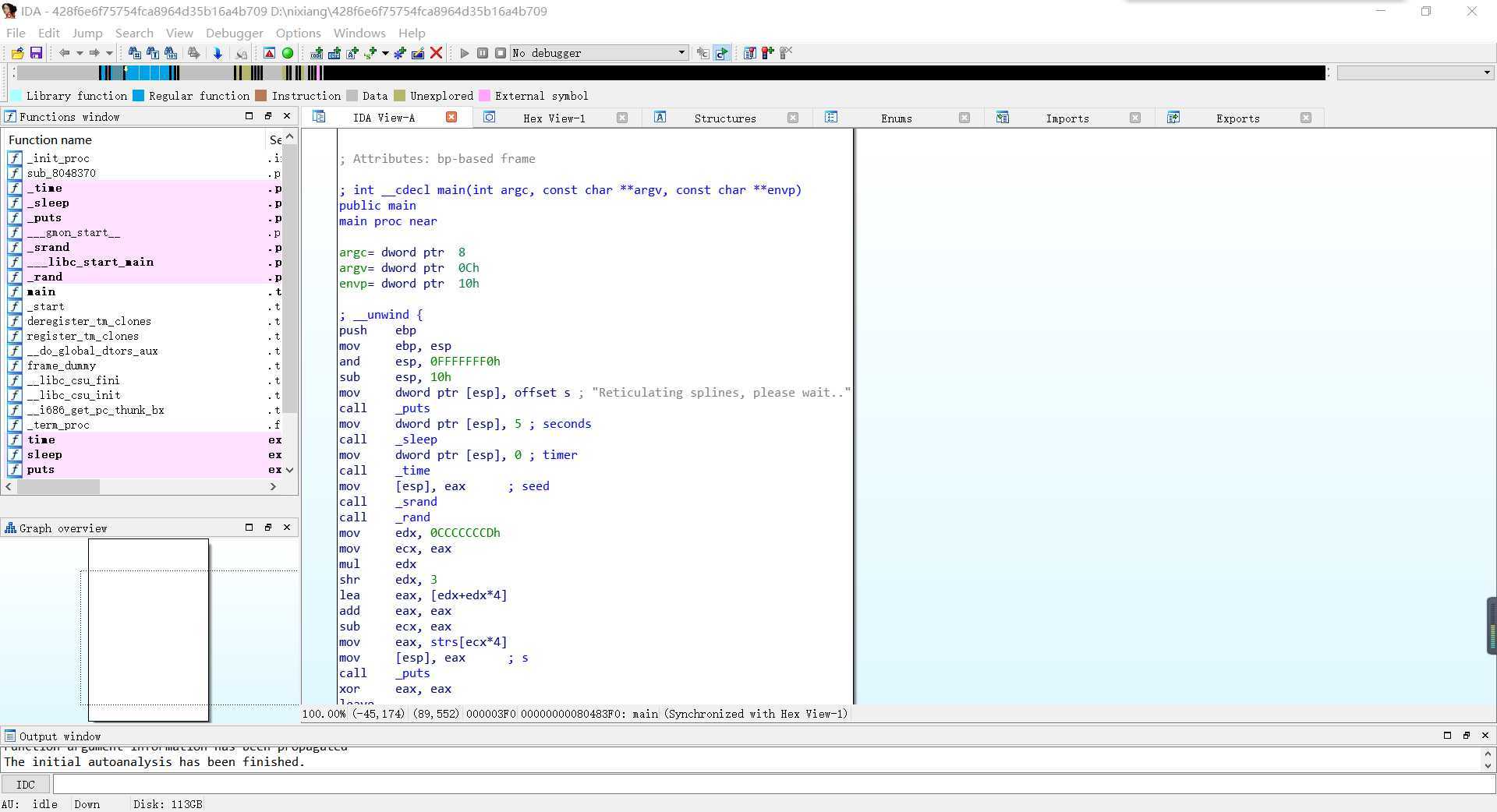
直接alt+t搜索flag
则得到falg:9447{This_is_a_flag}
题目描述:菜鸡和菜猫进行了一场Py交易
文件为pyc文件,则对其进行反编译
import base64 def encode(message): s = ‘‘ for i in message: x = ord(i) ^ 32 x = x + 16 s += chr(x) return base64.b64encode(s) correct = ‘XlNkVmtUI1MgXWBZXCFeKY+AaXNt‘ flag = ‘‘ print ‘Input flag:‘ flag = raw_input() if encode(flag) == correct: print ‘correct‘ else: print ‘wrong‘ import base64 def encode(message): s = ‘‘ for i in message: x = ord(i) ^ 32 x = x + 16 s += chr(x) return base64.b64encode(s) correct = ‘XlNkVmtUI1MgXWBZXCFeKY+AaXNt‘ flag = ‘‘ print ‘Input flag:‘ flag = raw_input() if encode(flag) == correct: print ‘correct‘ else: print ‘wrong‘
分析代码可知,输入flag=correct就会输出correct,则flag经过加密成为了correct
ord(i)返回的是i的ASCLL码,然后异或32,再移位16,再返回对应的ASCLL码的值
import base64 correct = "XlNkVmtUI1MgXWBZXCFeKY+AaXNt" temp = base64.b64decode(correct).decode("ISO-8859-1") flag=‘‘ for i in temp: s = chr((ord(i)-16)^32) flag += s print(flag)
则flag为:nctf{d3c0mpil1n9_PyC}
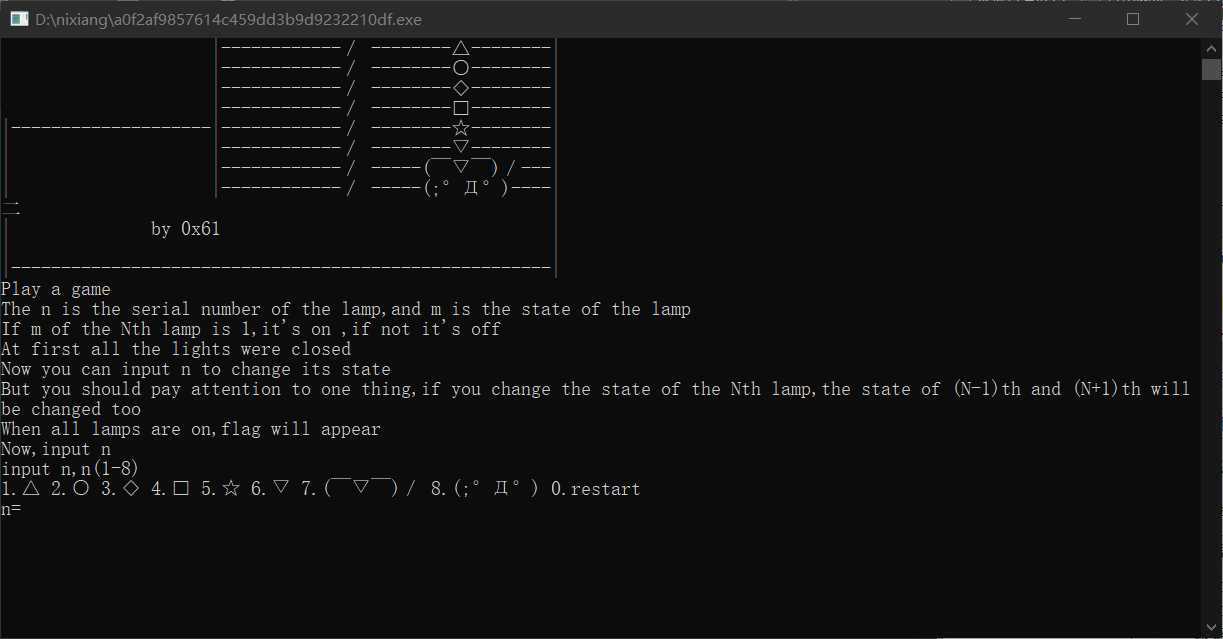
根据题目可知,不同的数字代表不同的形状根据提示依次输入1——8,则flag就出来了
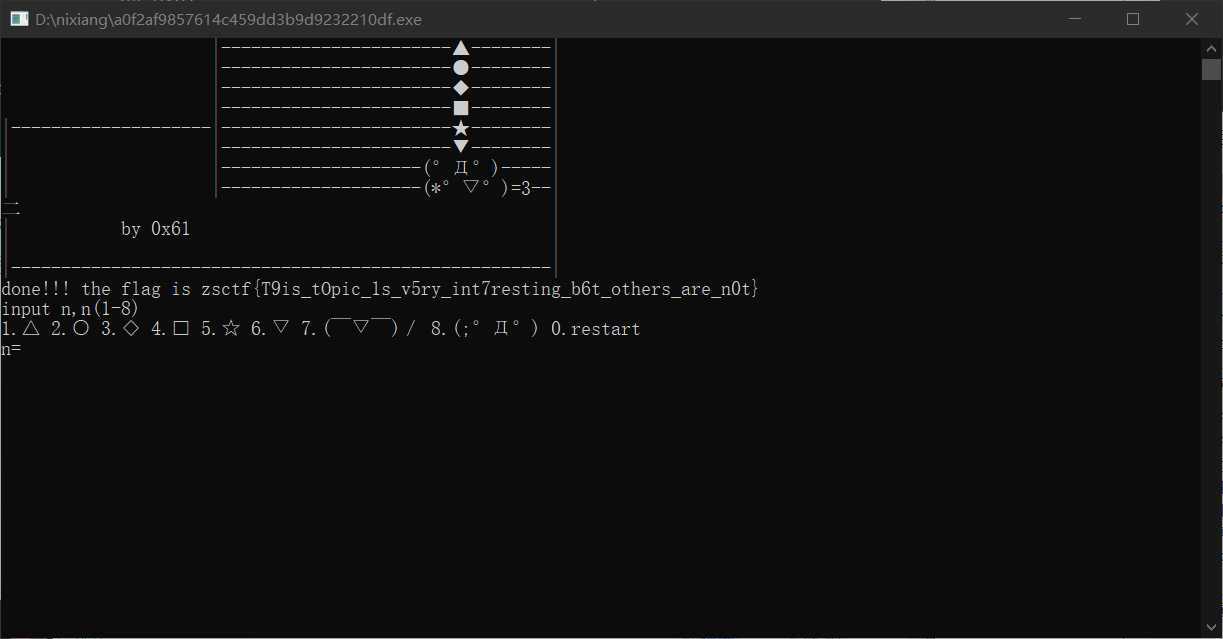
the flag is zsctf{T9is_tOpic_1s_v5ry_int7resting_b6t_others_are_n0t}
软件安装:
vscode下的各插件及配置环境,在vbox虚拟机软件上安装了kali和ubuntu,下载并熟悉使用了IDA软件。
原文:https://www.cnblogs.com/JackeyLov3/p/13059288.html