Vulnerability Scanning
VULNERABILITY SCAN
- Structured approach to examining targets to identify known weaknesses
- Many different types
- Determine if any known weaknesses exist
CREDENTIALED VS. NON-CREDENTIALED
- Credentialed(authenticated) - Accessing resources using valid credentials
- More detailed, accurate information
- Non-credentialed(non-authenticated) - anonymous access to exposed resources
- Fewer details, often used in early phases of attacks/tests
TYPES OF SCANS
- Discovery scan - used to find potential targets
- Identity/info gathering early on
- nmap ping sweep
- Full scan - scans ports, services, and vulnerabilities
- Full scan with fingerprinting
- nmap - A
- perl nikto.pl -h
- OpenVAS
- Open-source version of Nessus
- Port scan
- Stealth scan - attempt to avoid tripping defensive control thresholds
- Compliance - scan for specific known vulnerabilities that would make a system non-compliant
QUICK REVIEW
- Structured approach to discovering target vulnerabilities
- Correlates known vulnerabilities with target characteristics
- Scans can be general (find any weaknesses) or targeted(see if specific weaknesses exist)
- Scans can range from quiet to very noisy
DEMO
Lab Environment:
? Metasploitable - 10.0.0.19,
? DVWA - 10.0.0.20,
? Kali Linux - 10.0.0.1`7
nmap
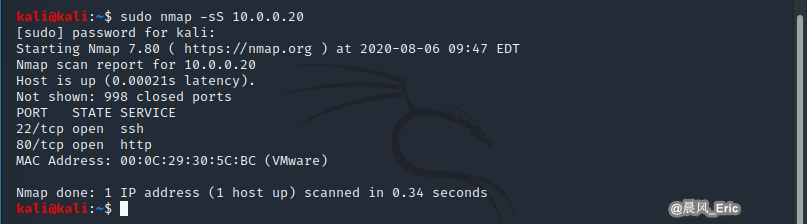
Stealth scan: nmap -sS
nmap -sS 10.0.0.20
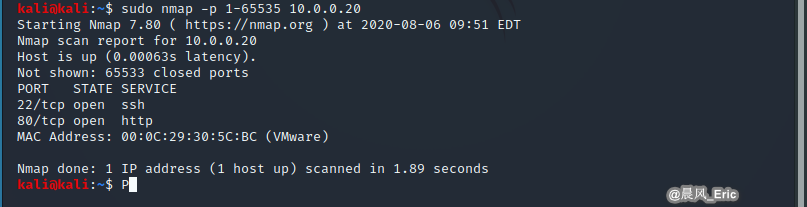
Scan specified ports: nmap -p
nmap -p 1-65535 10.0.0.20
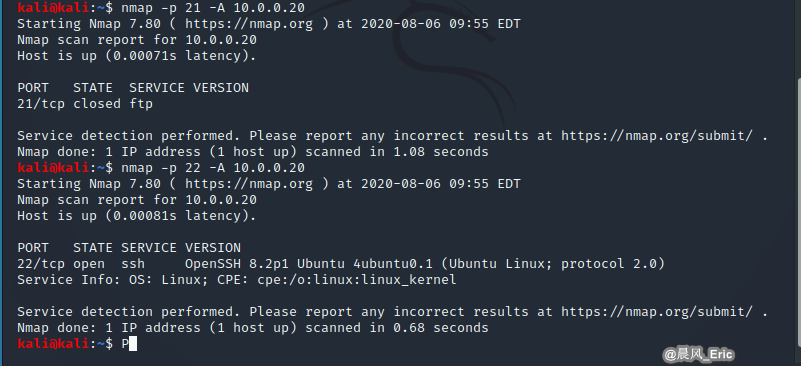
A option includes fingerprinting
nmap -p 22 -A 10.0.0.20
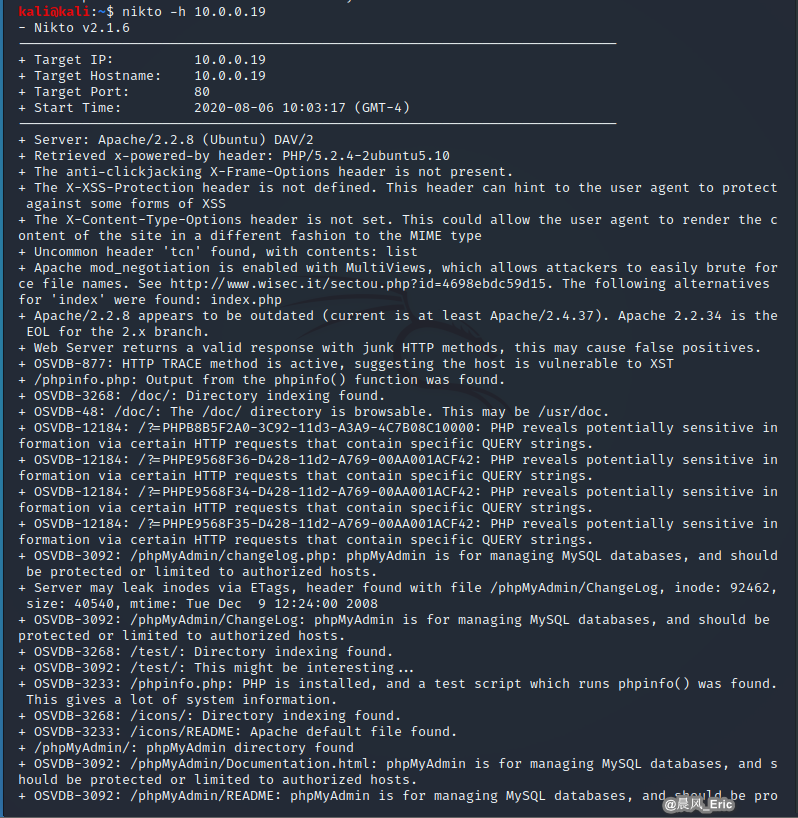
nikto
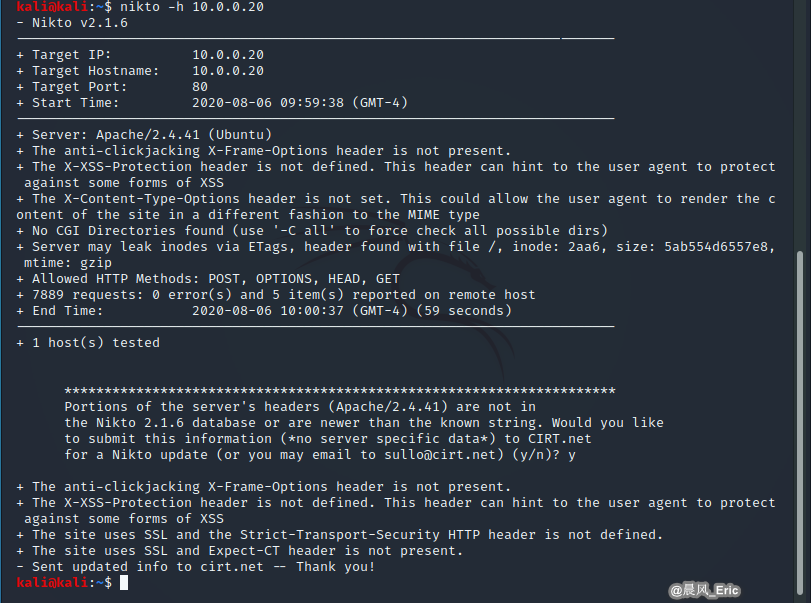
Nikto vulnerability scan: nikto -h
nikto -h 10.0.0.20
OpenVAS
Official site:
https://www.openvas.org/
https://github.com/greenbone/openvas/blob/master/INSTALL.md
Install perquisites on Kali:
https://tools.kali.org/vulnerability-analysis/openvas
apt-get install gcc pkg-config libssh-gcrypt-dev libgnutls28-dev libglib2.0-dev libpcap-dev libgpgme-dev bison libksba-dev libsnmp-dev libgcrypt20-dev redis-server
Continue on the next blog...
Penetration Test - Survey the Target(4)
原文:https://www.cnblogs.com/keepmoving1113/p/13449565.html




