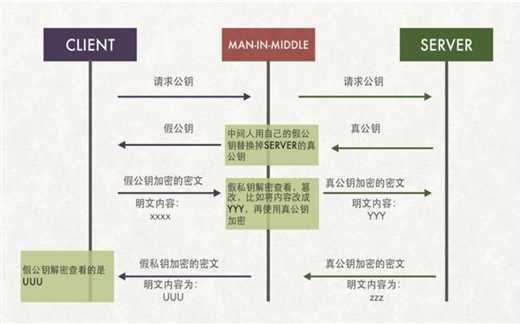
预防中间人攻击
[ CA_default ] dir = /etc/pki/CA # Where everything is kept certs = $dir/certs # Where the issued certs are kept crl_dir = $dir/crl # Where the issued crl are kept database = $dir/index.txt # database index file. # several ctificates with same subject. new_certs_dir = $dir/newcerts # default place for new certs. certificate = $dir/cacert.pem # The CA certificate CA自签证书存放位置 serial = $dir/serial # The current serial number crlnumber = $dir/crlnumber # the current crl number # must be commented out to leave a V1 CRL crl = $dir/crl.pem # The current CRL private_key = $dir/private/cakey.pem# The private key CA的私钥存放位置。 RANDFILE = $dir/private/.rand # private random number file x509_extensions = usr_cert # The extentions to add to the cert name_opt = ca_default # Subject Name options cert_opt = ca_default # Certificate field options default_days = 365 # how long to certify for default_crl_days= 30 # how long before next CRL default_md = sha256 # use SHA-256 by default preserve = no # keep passed DN ordering policy = policy_match
[ policy_match ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional
optional:可有可无,跟CA设置信息可不一致
touch /etc/pki/CA/index.txt #生成证书索引数据库文件 echo 01 > /etc/pki/CA/serial #指定第一个颁发证书的序列号
第二步: CA自签证书
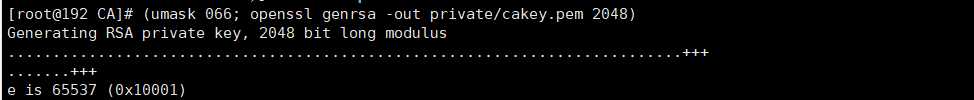
cd /etc/pki/CA/ (umask 066; openssl genrsa -out private/cakey.pem 2048)
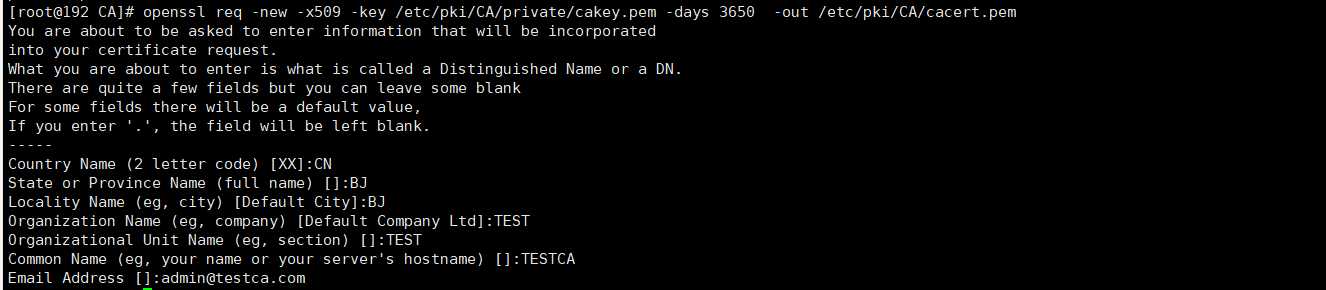
openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
(umask 066; openssl genrsa –out /data/test.key 2048)
openssl req -new -key /data/test.key -out /data/test.csr
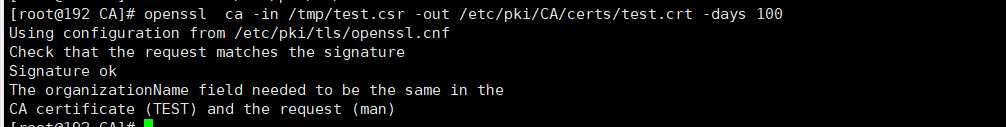
openssl ca -in /tmp/test.csr –out /etc/pki/CA/certs/test.crt -days 100 注意:默认要求 国家,省,公司名称三项必须和CA一致
将证书发送给申请者后,在申请者的主机上看到.cst文件。
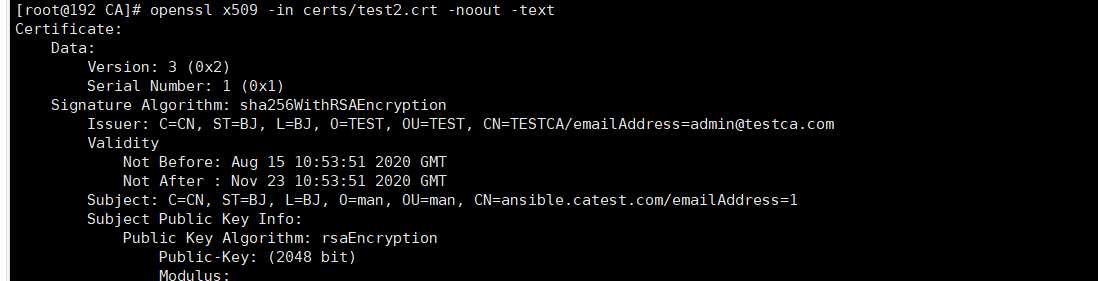
查看证书内容
openssl x509 -in /PATH/FROM/CERT_FILE -noout -text|issuer|subject|serial|dates
原文:https://www.cnblogs.com/wxxjianchi/p/13509911.html