sysctl -a |grep ‘ip_forward‘
vim /etc/sysctl.conf
[firewall]#sysctl -p
net.ipv4.ip_forward = 1
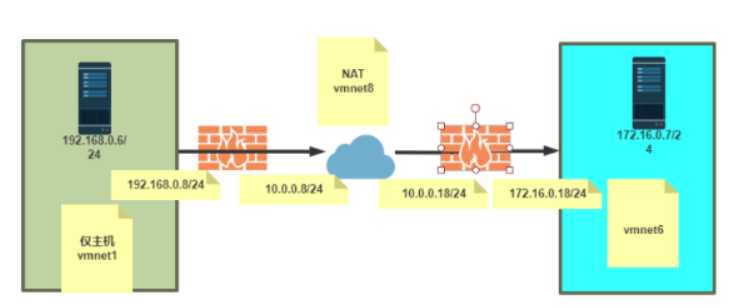
192.168.0.6 gw 182.168.0.8
?
仅主机模式 192.168.0.8
桥接/NAT 模式 10.0.0.8
?
nmcli con delete wired\ connection\ 1
或nmcli con delete "wired connection 1"
nmcli con reload
?
?
?
桥接/NAT模式 10.0.0.18
vmnet 6 172.16.0.18
?
nmcli con delete wired\ connection\ 1
nmcli con reload
?
#开启ip_forward
echo 1 > /proc/sys/net/ipv4/ip_foeward
vmnet6 172.16.0.7 gw 172.16.0.18
?
#开启ip_forward
echo 1 > /proc/sys/net/ipv4/ip_foeward
?
curl 127.0.0.1 #确定自己httpd通
?
?
fire1 ------ SNAT
iptables -t nat -A POSTROUTING -s 192.168.0.0/24 -j MASQUERADE
?
?
fire 2 -----DNAT
iptables -t nat -A PREROUTING -d 10.0.0.18 -p tcp --dport 80 -j DNAT --to-destination 172.16.0.7:80
?
?
centos6# while :;do curl 10.0.0.18 ;sleep 1;done
##centos7
?
查看日志
[root@lan-host ~]#tail -f /var/log/httpd/access_log
[root@firewall-host ~]#tail -f /proc/net/nf_conntrack
fire 2 -----SNAT
iptables -t nat -A POSTROUTING -s 172.16.0.0/24 -j MASQUERADE
?
?
fire1 ------ DNAT
iptables -t nat -A PREROUTING -d 10.0.0.8 -p tcp --dport 80 -j DNAT --to-destination 192.168.0.6:80
?
curl 10.0.0.8
## centos6
原文:https://www.cnblogs.com/weiweirui/p/13687572.html