Man in the middle exploits
ADDITIONAL NETWORK EXPLOITS
- Man-in-the-middle
- Family of attacks where the attack intercepts messages between a sender and receiver
- Attack may modify, regenerate, or forward intercepted messages
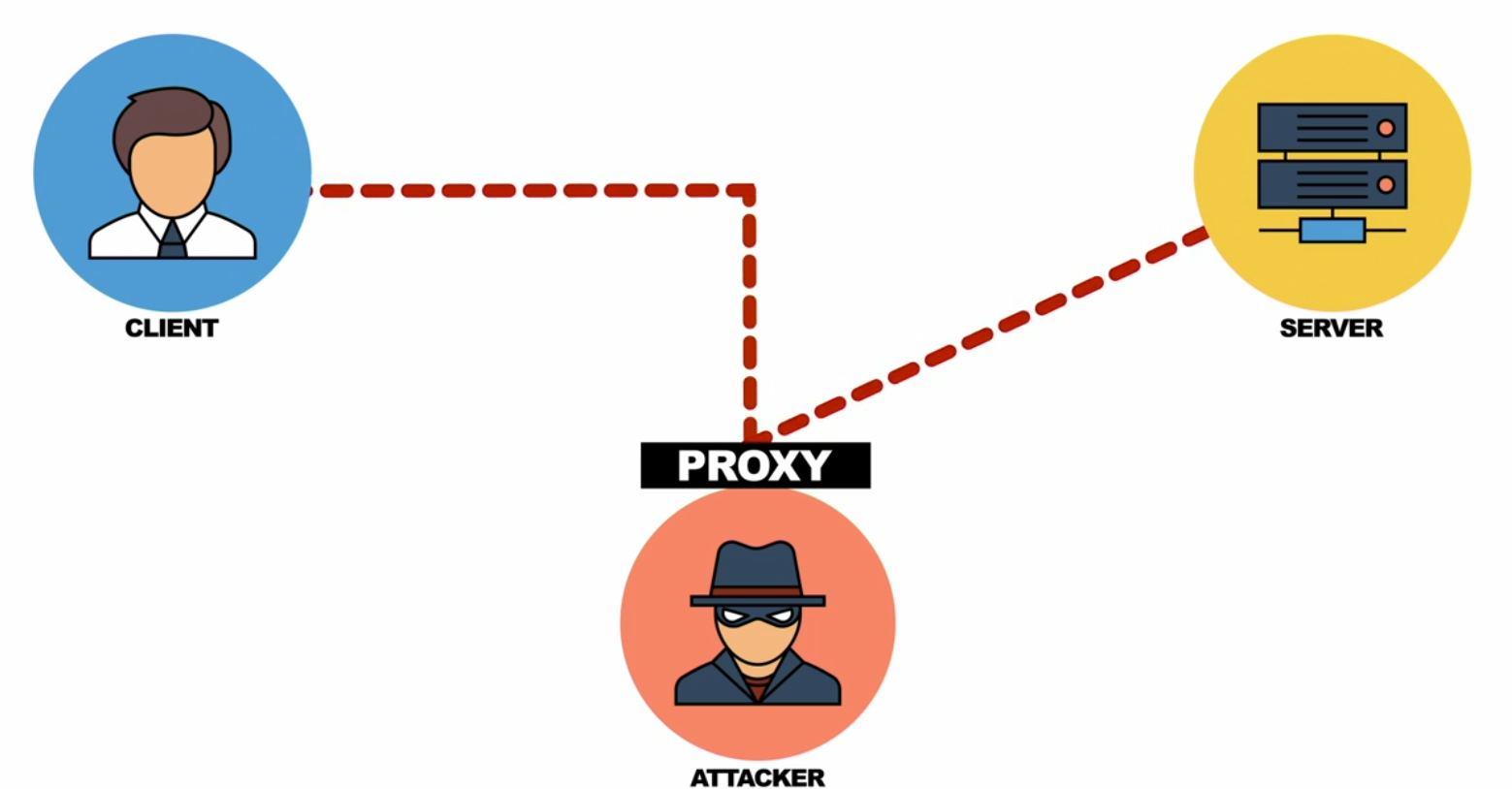
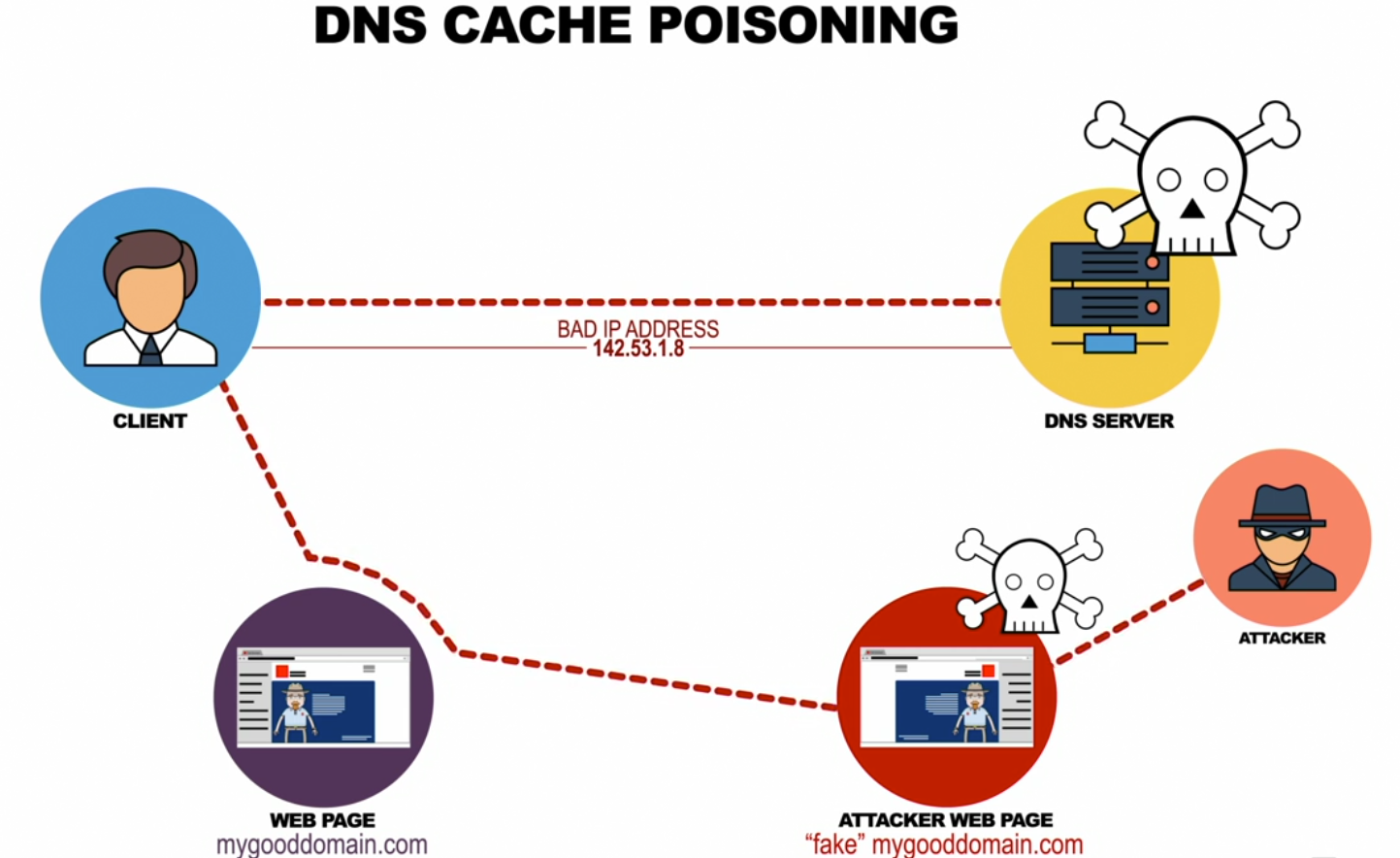
MAN-IN-THE-MIDDLE EXPLOITS
- ARP spoofing
- Similar to DNS poisoning, but with local MAC address
- Pass the hash
- Attacker intercepts an NTLM hash (user credential) and reuses it to appear as an authenticated user to Windows
- Replay
- Relay
- SSL(Secure Sockets Layer) stripping
- Downgrade
- DoS(Denial of Service)/stress test
- NAC(Network Access Control) bypass
- VLAN (Virtual Local Area Network) hopping
QUICK REVIEW
- MITM attacker intercepts all traffic between sender and receiver
- May be part of an attack chain
- Multiple MITM possibilities, including ARP spoofing, pass the hash, replay attack
- Useful to bypass normal network security controls
Penetration Test - Select Your Attacks(5)
原文:https://www.cnblogs.com/keepmoving1113/p/13687710.html

