话不多说,看下文:
影响内容:登录模块
触发条件:通过抓包请求获取用户登录信息
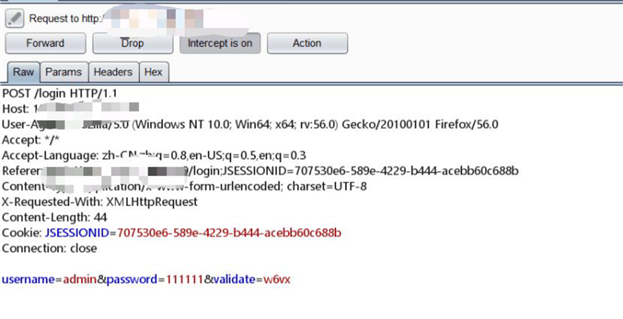
触发后结果:窃取用户信息
修改前内容:直接把用户填写的表单信息明文提交后台
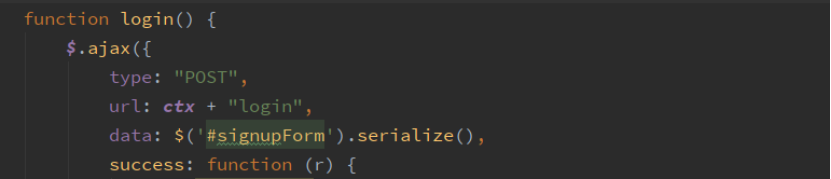
1.5:修改后内容:
把用户密码加密后再进行传输(注:此处用的base64加密,推荐使用rsa加解密更加安全)
此处提供Rsa加解密工具类以及获取公钥私钥的方法
前端rsa加密js
需要引用jsencrypt.js(下载地址:)
function getEncode(message){
let publicKey ="使用工具类获取公钥";
let encrypt = new JSEncrypt();
encrypt.setPublicKey(publicKey);
message= encrypt.encryptLong(message);
return message;
}
前端html
function login() {
var password = $("#password").val();
password = getEncode(password);
}
}
后端解密:
try {
//重中之重,前端传过来的密文值中的+号会被空格替换因此需要还原
password = password.replaceAll(" ","+");
//私钥解密
PrivateKey privateKey = RsaUtil.getPrivateKey(Constant.PRIVATEKEYTWO);
password=RsaUtil.decryptString(privateKey,password);
} catch (Exception e) {
request.getSession().invalidate();
logger.error(LogUtils.errorlog("rsa转码失败"+ e.getMessage()));
}
RsaUtil工具类如下:
import org.apache.commons.codec.binary.Base64;
import sun.misc.BASE64Decoder;
import javax.crypto.Cipher;
import java.io.ByteArrayOutputStream;
import java.math.BigInteger;
import java.security.*;
import java.security.interfaces.RSAPrivateKey;
import java.security.interfaces.RSAPublicKey;
import java.security.spec.*;
/**
* @author xxx
* @date 2020/8/31 11:45
*/
public class RsaUtil {
/**
* 指定加密算法为DESede //MD5withRSA///RSA/ECB/PKCS1Padding
*/
private static String ALGORITHM = "RSA/ECB/PKCS1Padding";
/**
* 指定key的大小(64的整数倍,最小512位)
*/
private static int KEYSIZE = 1024;
/**
* RSA最大加密明文大小
*/
private static final int MAX_ENCRYPT_BLOCK = 117;
/**
* RSA最大解密密文大小
*/
private static final int MAX_DECRYPT_BLOCK = 128;
/**
* 公钥模量
*/
private static String publicModulus = null;
/**
* 公钥指数
*/
private static String publicExponent = null;
/**
* 私钥模量
*/
private static String privateModulus = null;
/**
* 私钥指数
*/
private static String privateExponent = null;
private static KeyFactory keyFactory = null;
static {
try {
keyFactory = KeyFactory.getInstance("RSA");
} catch (NoSuchAlgorithmException ex) {
System.out.println(ex.getMessage());
}
}
public RsaUtil() {
try {
generateKeyPairString(KEYSIZE);
} catch (Exception e) {
}
}
public RsaUtil(int keySize) {
try {
generateKeyPairString(keySize);
} catch (Exception e) {
}
}
/**
* 生成密钥对字符串
*/
private void generateKeyPairString(int keySize) throws Exception {
/** RSA算法要求有一个可信任的随机数源 */
SecureRandom sr = new SecureRandom();
/** 为RSA算法创建一个KeyPairGenerator对象 */
KeyPairGenerator kpg = KeyPairGenerator.getInstance("RSA");
/** 利用上面的随机数据源初始化这个KeyPairGenerator对象 */
kpg.initialize(keySize, sr);
/** 生成密匙对 */
KeyPair kp = kpg.generateKeyPair();
/** 得到公钥 */
Key publicKey = kp.getPublic();
/** 得到私钥 */
Key privateKey = kp.getPrivate();
/** 用字符串将生成的密钥写入文件 */
// 获取算法
String algorithm = publicKey.getAlgorithm();
KeyFactory keyFact = KeyFactory.getInstance(algorithm);
BigInteger prime = null;
BigInteger exponent = null;
RSAPublicKeySpec keySpec = (RSAPublicKeySpec) keyFact.getKeySpec(publicKey, RSAPublicKeySpec.class);
prime = keySpec.getModulus();
exponent = keySpec.getPublicExponent();
RsaUtil.publicModulus = HexUtil.bytes2Hex(prime.toByteArray());
RsaUtil.publicExponent = HexUtil.bytes2Hex(exponent.toByteArray());
RSAPrivateCrtKeySpec privateKeySpec = (RSAPrivateCrtKeySpec) keyFact.getKeySpec(privateKey, RSAPrivateCrtKeySpec.class);
BigInteger privateModulus = privateKeySpec.getModulus();
BigInteger privateExponent = privateKeySpec.getPrivateExponent();
RsaUtil.privateModulus = HexUtil.bytes2Hex(privateModulus.toByteArray());
RsaUtil.privateExponent = HexUtil.bytes2Hex(privateExponent.toByteArray());
}
/**
* 根据给定的16进制系数和专用指数字符串构造一个RSA专用的公钥对象。
*
* @param hexModulus 系数。
* @param hexPublicExponent 专用指数。
* @return RSA专用公钥对象。
*/
public static RSAPublicKey getRsaPublicKey(String hexModulus, String hexPublicExponent) {
if (isBlank(hexModulus) || isBlank(hexPublicExponent)) {
System.out.println("hexModulus and hexPublicExponent cannot be empty. return null(RSAPublicKey).");
return null;
}
byte[] modulus = null;
byte[] publicExponent = null;
try {
modulus = HexUtil.hex2Bytes(hexModulus);
publicExponent = HexUtil.hex2Bytes(hexPublicExponent);
} catch (Exception ex) {
System.out.println("hexModulus or hexPublicExponent value is invalid. return null(RSAPublicKey).");
}
if (modulus != null && publicExponent != null) {
return generateRsaPublicKey(modulus, publicExponent);
}
return null;
}
/**
* 根据给定的系数和专用指数构造一个RSA专用的公钥对象。
*
* @param modulus 系数。
* @param publicExponent 专用指数。
* @return RSA专用公钥对象。
*/
public static RSAPublicKey generateRsaPublicKey(byte[] modulus, byte[] publicExponent) {
RSAPublicKeySpec publicKeySpec = new RSAPublicKeySpec(new BigInteger(modulus),
new BigInteger(publicExponent));
try {
return (RSAPublicKey) keyFactory.generatePublic(publicKeySpec);
} catch (InvalidKeySpecException ex) {
System.out.println("RSAPublicKeySpec is unavailable.");
} catch (NullPointerException ex) {
System.out.println("RSAUtils#KEY_FACTORY is null, can not generate KeyFactory instance.");
}
return null;
}
/**
* 根据给定的16进制系数和专用指数字符串构造一个RSA专用的私钥对象。
*
* @param hexModulus 系数。
* @param hexPrivateExponent 专用指数。
* @return RSA专用私钥对象。
*/
public static RSAPrivateKey getRsaPrivateKey(String hexModulus, String hexPrivateExponent) {
if (isBlank(hexModulus) || isBlank(hexPrivateExponent)) {
System.out.println("hexModulus and hexPrivateExponent cannot be empty. RSAPrivateKey value is null to return.");
return null;
}
byte[] modulus = null;
byte[] privateExponent = null;
try {
modulus = HexUtil.hex2Bytes(hexModulus);
privateExponent = HexUtil.hex2Bytes(hexPrivateExponent);
} catch (Exception ex) {
System.out.println("hexModulus or hexPrivateExponent value is invalid. return null(RSAPrivateKey).");
}
if (modulus != null && privateExponent != null) {
return generateRsaPrivateKey(modulus, privateExponent);
}
return null;
}
/**
* 根据给定的系数和专用指数构造一个RSA专用的私钥对象。
*
* @param modulus 系数。
* @param privateExponent 专用指数。
* @return RSA专用私钥对象。
*/
public static RSAPrivateKey generateRsaPrivateKey(byte[] modulus, byte[] privateExponent) {
RSAPrivateKeySpec privateKeySpec = new RSAPrivateKeySpec(new BigInteger(modulus),
new BigInteger(privateExponent));
try {
return (RSAPrivateKey) keyFactory.generatePrivate(privateKeySpec);
} catch (InvalidKeySpecException ex) {
System.out.println("RSAPrivateKeySpec is unavailable.");
} catch (NullPointerException ex) {
System.out.println("RSAUtils#KEY_FACTORY is null, can not generate KeyFactory instance.");
}
return null;
}
/**
* 使用给定的公钥加密给定的字符串。
*
* @param key 给定的公钥。
* @param plaintext 字符串。
* @return 给定字符串的密文。
*/
public static String encryptString(Key key, String plaintext) {
if (key == null || plaintext == null) {
return null;
}
byte[] data = plaintext.getBytes();
try {
byte[] enData = encrypt(key, data);
return new String(Base64.encodeBase64String(enData));
} catch (Exception ex) {
}
return null;
}
/**
* 使用指定的公钥加密数据。
*
* @param key 给定的公钥。
* @param data 要加密的数据。
* @return 加密后的数据。
*/
public static byte[] encrypt(Key key, byte[] data) throws Exception {
Cipher ci = Cipher.getInstance(ALGORITHM);
ci.init(Cipher.ENCRYPT_MODE, key);
int inputLen = data.length;
ByteArrayOutputStream out = new ByteArrayOutputStream();
int offSet = 0;
byte[] cache;
int i = 0;
// 对数据分段加密
while (inputLen - offSet > 0) {
if (inputLen - offSet > MAX_ENCRYPT_BLOCK) {
cache = ci.doFinal(data, offSet, MAX_ENCRYPT_BLOCK);
} else {
cache = ci.doFinal(data, offSet, inputLen - offSet);
}
out.write(cache, 0, cache.length);
i++;
offSet = i * MAX_ENCRYPT_BLOCK;
}
byte[] encryptedData = out.toByteArray();
out.close();
return encryptedData;
}
/**
* 使用给定的公钥解密给定的字符串。
*
* @param key 给定的公钥
* @param encrypttext 密文
* @return 原文字符串。
*/
public static String decryptString(Key key, String encrypttext) {
if (key == null || isBlank(encrypttext)) {
return null;
}
try {
byte[] enData = Base64.decodeBase64(encrypttext);
byte[] data = decrypt(key, enData);
return new String(data);
} catch (Exception ex) {
System.out.println(String.format("\"%s\" Decryption failed. Cause: %s", encrypttext, ex.getCause().getMessage()));
}
return null;
}
/**
* 使用指定的公钥解密数据。
*
* @param key 指定的公钥
* @param data 要解密的数据
* @return 原数据
* @throws Exception
*/
public static byte[] decrypt(Key key, byte[] data) throws Exception {
Cipher ci = Cipher.getInstance(ALGORITHM);
ci.init(Cipher.DECRYPT_MODE, key);
int inputLen = data.length;
ByteArrayOutputStream out = new ByteArrayOutputStream();
int offSet = 0;
byte[] cache;
int i = 0;
// 对数据分段解密
while (inputLen - offSet > 0) {
if (inputLen - offSet > MAX_DECRYPT_BLOCK) {
cache = ci.doFinal(data, offSet, MAX_DECRYPT_BLOCK);
} else {
cache = ci.doFinal(data, offSet, inputLen - offSet);
}
out.write(cache, 0, cache.length);
i++;
offSet = i * MAX_DECRYPT_BLOCK;
}
byte[] decryptedData = out.toByteArray();
out.close();
return decryptedData;
}
/**
* 判断非空字符串
*
* @param cs 待判断的CharSequence序列
* @return 是否非空
*/
private static boolean isBlank(final CharSequence cs) {
int strLen;
if (cs == null || (strLen = cs.length()) == 0) {
return true;
}
for (int i = 0; i < strLen; i++) {
if (Character.isWhitespace(cs.charAt(i)) == false) {
return false;
}
}
return true;
}
public static PublicKey getPublicKey(String key) throws Exception {
byte[] keyBytes;
keyBytes = (new BASE64Decoder()).decodeBuffer(key);
X509EncodedKeySpec keySpec = new X509EncodedKeySpec(keyBytes);
KeyFactory keyFactory = KeyFactory.getInstance("RSA");
PublicKey publicKey = keyFactory.generatePublic(keySpec);
return publicKey;
}
public static PrivateKey getPrivateKey(String key) throws Exception {
byte[] keyBytes;
keyBytes = (new BASE64Decoder()).decodeBuffer(key);
PKCS8EncodedKeySpec keySpec = new PKCS8EncodedKeySpec(keyBytes);
KeyFactory keyFactory = KeyFactory.getInstance("RSA");
PrivateKey privateKey = keyFactory.generatePrivate(keySpec);
return privateKey;
}
public static void main(String[] args)throws Exception {
// KeyPairGenerator类用于生成公钥和私钥对,基于RSA算法生成对象
KeyPairGenerator keyPairGen = KeyPairGenerator.getInstance("RSA");
// 初始化密钥对生成器,密钥大小为96-1024位
keyPairGen.initialize(1024,new SecureRandom());
// 生成一个密钥对,保存在keyPair中
KeyPair keyPair = keyPairGen.generateKeyPair();
RSAPrivateKey privateKey = (RSAPrivateKey) keyPair.getPrivate(); // 得到私钥
RSAPublicKey publicKey = (RSAPublicKey) keyPair.getPublic(); // 得到公钥
String publicKeyString = new String(Base64.encodeBase64(publicKey.getEncoded()));
// 得到私钥字符串
String privateKeyString = new String(Base64.encodeBase64((privateKey.getEncoded())));
// 将公钥和私钥保存到Map
System.out.println("公钥 "+publicKeyString);
System.out.println("私钥 "+privateKeyString);
}
}
影响内容:所有模块
触发条件:通过slowhttp慢速dos工具包进行请求
效果:
触发原因:
当客户端连接量上升之后,占用住了webserver的所有可用连接,从而导致DOS。
解决办法:
设置tomcat的connection-timeout: xxx(可以通过二分法逼近合适时长来选择最适合的数值)
影响内容:所有模块
触发条件:用户篡改页面、接口请求
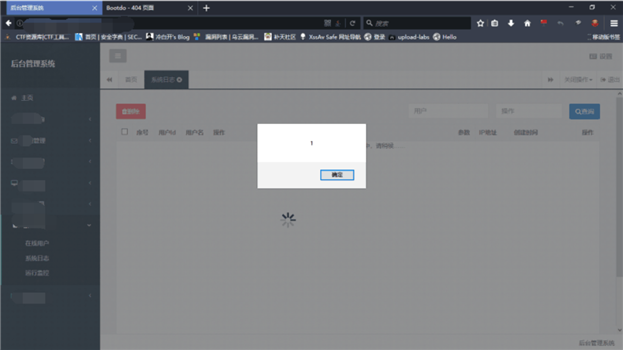
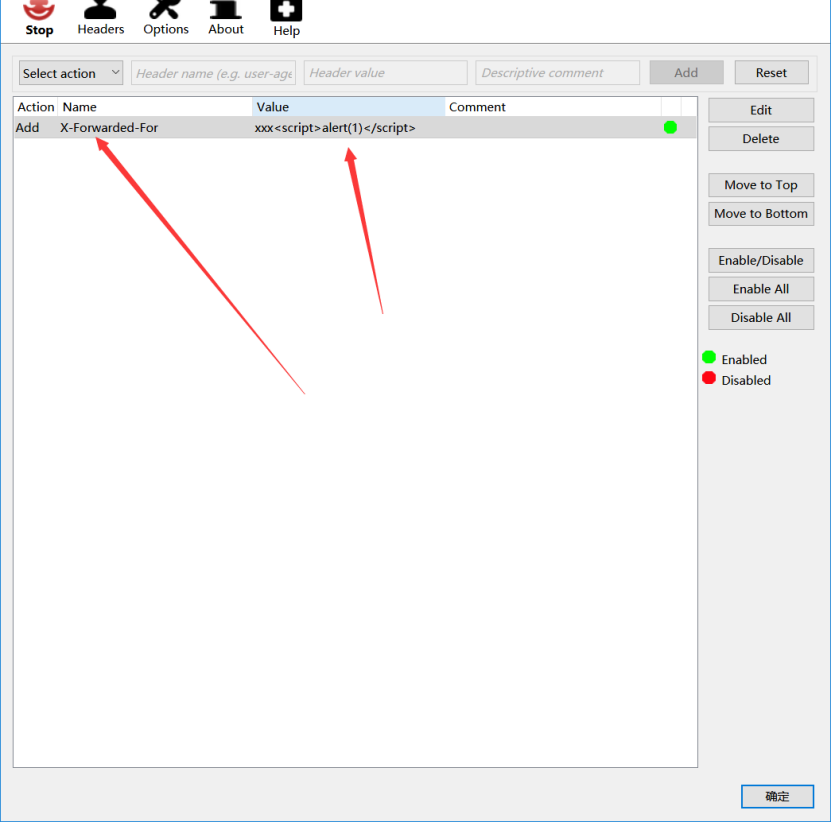
触发后结果:劫持session信息
解决方案:开启XSS过滤
@Configuration
public class XssConfig{
/**
* xss过滤拦截器
*/
@SuppressWarnings({ "rawtypes", "unchecked" })
@Bean
public FilterRegistrationBean xssFilterRegistrationBean() {
FilterRegistrationBean filterRegistrationBean = new FilterRegistrationBean();
filterRegistrationBean.setFilter(new XssFilter());
filterRegistrationBean.setOrder(1);
//开启xss过滤拦截器
filterRegistrationBean.setEnabled(true);
filterRegistrationBean.addUrlPatterns("/*");
Map<String, String> initParameters = new HashMap<String, String>(16);
initParameters.put("excludes", "/favicon.ico,/img/*,/js/*,/css/*");
initParameters.put("isIncludeRichText", "true");//开启xss过滤
filterRegistrationBean.setInitParameters(initParameters);
return filterRegistrationBean;
}
类XssFilter
/**
* 拦截防止xss注入
* 通过Jsoup过滤请求参数内的特定字符
* @author xxx
*/
public class XssFilter implements Filter {
private static Logger logger = LoggerFactory.getLogger(XssFilter.class);
/**
* 是否过滤富文本内容
*/
private static boolean IS_INCLUDE_RICH_TEXT = false;
public List<String> excludes = new ArrayList<>();
@Override
public void doFilter(ServletRequest request, ServletResponse response, FilterChain filterChain) throws IOException,ServletException {
if(logger.isDebugEnabled()){
logger.debug(LogUtils.log("debug","xss filter is open"));
}
HttpServletRequest req = (HttpServletRequest) request;
HttpServletResponse resp = (HttpServletResponse) response;
if(handleExcludeUrl(req, resp)){
filterChain.doFilter(request, response);
return;
}
XssHttpServletRequestWrapper xssRequest = new XssHttpServletRequestWrapper((HttpServletRequest) request,IS_INCLUDE_RICH_TEXT);
filterChain.doFilter(xssRequest, response);
}
private boolean handleExcludeUrl(HttpServletRequest request, HttpServletResponse response) {
if (excludes == null || excludes.isEmpty()) {
return false;
}
String url = request.getServletPath();
for (String pattern : excludes) {
Pattern p = Pattern.compile("^" + pattern);
Matcher m = p.matcher(url);
if (m.find()) {
return true;
}
}
return false;
}
@Override
public void init(FilterConfig filterConfig) throws ServletException {
if(logger.isDebugEnabled()){
logger.debug(LogUtils.log("debug","xss filter init~~~~~~~~~~~~"));
}
String isIncludeRichText = filterConfig.getInitParameter("isIncludeRichText");
if(StringUtils.isNotBlank(isIncludeRichText)){
IS_INCLUDE_RICH_TEXT = BooleanUtils.toBoolean(isIncludeRichText);
}
String temp = filterConfig.getInitParameter("excludes");
if (temp != null) {
String[] url = temp.split(",");
for (int i = 0; url != null && i < url.length; i++) {
excludes.add(url[i]);
}
}
}
@Override
public void destroy() {}
}
}
类XssHttpServletRequestWrapper
public class XssHttpServletRequestWrapper extends HttpServletRequestWrapper {
HttpServletRequest orgRequest = null;
private boolean isIncludeRichText = false;
public XssHttpServletRequestWrapper(HttpServletRequest request, boolean isIncludeRichText) {
super(request);
orgRequest = request;
this.isIncludeRichText = isIncludeRichText;
}
/**
* 覆盖getParameter方法,将参数名和参数值都做xss过滤。<br/>
* 如果需要获得原始的值,则通过super.getParameterValues(name)来获取<br/>
* getParameterNames,getParameterValues和getParameterMap也可能需要覆盖
*/
@Override
public String getParameter(String name) {
Boolean flag = ("content".equals(name) || name.endsWith("WithHtml"));
if( flag && !isIncludeRichText){
return super.getParameter(name);
}
name = JsoupUtil.clean(name);
String value = super.getParameter(name);
if (StringUtils.isNotBlank(value)) {
value = JsoupUtil.clean(value);
}
return value;
}
@Override
public String[] getParameterValues(String name) {
String[] arr = super.getParameterValues(name);
if(arr != null){
for (int i=0;i<arr.length;i++) {
arr[i] = JsoupUtil.clean(arr[i]);
}
}
return arr;
}
/**
* 覆盖getHeader方法,将参数名和参数值都做xss过滤。<br/>
* 如果需要获得原始的值,则通过super.getHeaders(name)来获取<br/>
* getHeaderNames 也可能需要覆盖
*/
@Override
public String getHeader(String name) {
name = JsoupUtil.clean(name);
String value = super.getHeader(name);
if (StringUtils.isNotBlank(value)) {
value = JsoupUtil.clean(value);
}
return value;
}
/**
* 获取最原始的request
*
* @return
*/
public HttpServletRequest getOrgRequest() {
return orgRequest;
}
/**
* 获取最原始的request的静态方法
*
* @return
*/
public static HttpServletRequest getOrgRequest(HttpServletRequest req) {
if (req instanceof XssHttpServletRequestWrapper) {
return ((XssHttpServletRequestWrapper) req).getOrgRequest();
}
return req;
}
}
影响内容:所有模块
触发条件:用户请求
触发后结果:控制整台服务器
解决方案:添加http安全请求类型过滤类
import org.apache.tomcat.util.descriptor.web.SecurityCollection;
import org.apache.tomcat.util.descriptor.web.SecurityConstraint;
import org.springframework.boot.web.embedded.tomcat.TomcatServletWebServerFactory;
import org.springframework.boot.web.servlet.server.ConfigurableServletWebServerFactory;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
@Configuration
public class SecuityConfig {
@Bean
public ConfigurableServletWebServerFactory configurableServletWebServerFactory() {
TomcatServletWebServerFactory factory = new TomcatServletWebServerFactory();
factory.addContextCustomizers(context -> {
SecurityConstraint securityConstraint = new SecurityConstraint();
securityConstraint.setUserConstraint("CONFIDENTIAL");
SecurityCollection collection = new SecurityCollection();
collection.addPattern("/*");
collection.addMethod("PATCH");
collection.addMethod("HEAD");
collection.addMethod("PUT");
collection.addMethod("DELETE");
collection.addMethod("OPTIONS");
collection.addMethod("TRACE");
collection.addMethod("COPY");
collection.addMethod("SEARCH");
collection.addMethod("PROPFIND");
collection.addMethod("LINK");
collection.addMethod("UNLINK");
collection.addMethod("PURGE");
collection.addMethod("LOCK");
collection.addMethod("UNLOCK");
collection.addMethod("VIEW");
securityConstraint.addCollection(collection);
context.addConstraint(securityConstraint);
});
return factory;
}
}
影响内容:所有模块
触发条件:用户请求
触发后结果:获取root用户权限,从而控制整个数据库、表信息。
修改前内容:使用root账户连接数据库
修改方法:使用普通用户连接数据库
影响内容:所有模块
触发条件:用户登陆系统之后,通过直接改变url地址的方式打开不属于本用户权限内的功能模块。
触发后结果:用户可以越权访问,不属于本用户权限内的模块。
修改前内容:未对其他功能模块添加权限认证处理
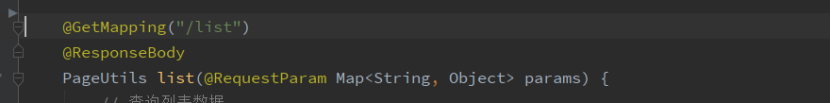
修改方法:针对普通用户不拥有访问权限的地址,新增访问权限配置。
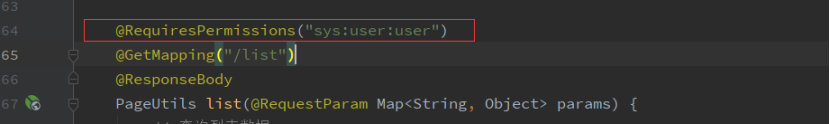
修改触发结果:无访问权限越权的地址,用户访问时跳转至403页面
影响内容:根据URL地址可以随意获取数据
触发条件:通过抓取请求头信息进行篡改内容
触发结果:修改请求头内容影响请求内容和结果
修改方法:写一个拦截器拦截地址判断是否登录,未登录跳转登录界面。
@Component
public class UserLoginInterceptor implements HandlerInterceptor {
private static final Logger LOGGER = LoggerFactory.getLogger(UserLoginInterceptor.class);
@Override
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler)
throws Exception {
//判断用户ID是否存在,不存在就跳转到登录界面
UserDO userDO = ShiroUtils.getUser();
if(userDO == null){
LOGGER.info("用户登录信息:{}",userDO);
response.sendRedirect(request.getContextPath()+"/login");
return false;
}else{
return true;
}
}
}
@Configuration
public class UserLoginConfig implements WebMvcConfigurer {
@Autowired
UserLoginInterceptor loginInterceptor;
final List<String> notLoginInterceptPaths = new ArrayList<String>() {
{ this.add("/login");
add("/index");
add("/css/**");
add("/js/**");
add("/img/**");
add("/docs/**");
add("/fonts/**");
add("/files/**");
add("/logout");
}
};
@Override
public void addInterceptors(InterceptorRegistry registry) {
registry.addInterceptor(loginInterceptor).addPathPatterns("/**").excludePathPatterns(notLoginInterceptPaths);
}
@Override
public void configureDefaultServletHandling(DefaultServletHandlerConfigurer configurer) {
configurer.enable();
}
@Bean
public InternalResourceViewResolver viewResolver() {
InternalResourceViewResolver resolver = new InternalResourceViewResolver();
resolver.setPrefix("/templates/");
resolver.setSuffix(".html");
resolver.setViewClass(JstlView.class);
return resolver;
}
@Override
public void addViewControllers(ViewControllerRegistry registry) {
}
}
跨域问题
解决方法:
第一种:
@Configuration
public class WebConfig implements WebMvcConfigurer {
@Override
public void addCorsMappings(CorsRegistry registry) {
registry.addMapping("/**")
.allowedOrigins("*")
.allowedMethods("POST", "GET", "PUT", "OPTIONS", "DELETE")
.maxAge(3600)
.allowCredentials(true);
}
@Override
public void configureDefaultServletHandling(DefaultServletHandlerConfigurer configurer) {
configurer.enable();
}
@Override
public void addViewControllers(ViewControllerRegistry registry) {
}
}
第二种:
@Configuration
public class CorsConfigration {
@Bean
public CorsFilter corsFilter() {
UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();
CorsConfiguration config = new CorsConfiguration();
// #允许向该服务器提交请求的URI,*表示全部允许,最好不要填写 * 号,除非特定情况
config.setAllowedOrigins(Arrays.asList("允许访问的域名"));
// 允许cookies跨域
config.setAllowCredentials(true);
// #允许访问的头信息,*表示全部
config.setAllowedHeaders(Arrays.asList("Accept","Content-Type","Content-Language","Accept-Language","Last-Event-ID"));
// 允许提交请求的方法,*表示全部允许
config.setAllowedMethods(Arrays.asList("GET","POST","PUT","DELETE"));
config.setMaxAge(3600L);
source.registerCorsConfiguration("/**", config);
return new CorsFilter(source);
}
/**
* 配置过滤器
*/
@Bean
public FilterRegistrationBean someFilterRegistration() {
FilterRegistrationBean<CorsFilter> registration = new FilterRegistrationBean<>();
registration.setFilter(corsFilter());
registration.addUrlPatterns("/*");
registration.setName("corsFilter");
registration.setOrder(Ordered.HIGHEST_PRECEDENCE);
return registration;
}
}
核心原因:通过获取sessionid,对某个用户进行强制退出
解决思路:在页面上对sessionid进行不展示其次在代码中判断当前用户是否是登录用户。
解决方法:
UserDO userDO= ShiroUtils.getUser();
if (userDO!=null){
if (userDO.getUsername().equals(userName)){
//进行逻辑处理
}else{
LOGGER.error(LogUtils.errorlog("登录用户已被篡改"));
}
}
原文:https://www.cnblogs.com/gyz-share-study/p/14448419.html