如何用Microsoft Graph API给应用添加Microsoft Graph Application Permission
|
{ "requiredResourceAccess": [ { "resourceAppId": "00000003-0000-0000-c000-000000000000", "resourceAccess": [ { "id": "e1fe6dd8-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "type": "Scope" },{ "id": "7ab1d382-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "type": "Role" } ] } ] } |
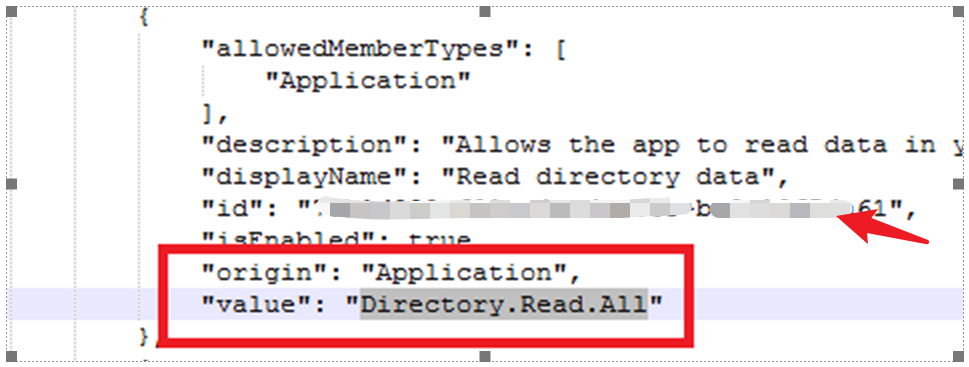
注:给应用添加Microsoft Graph Delegated Permission,需要在第一步中查找oauth2PermissionScopes中对应的权限Directory.Read.All并且找到对应的id,把第二步中的标黄的type的值修改为Scope,并且把id的值替换掉。
https://microsoftgraph.chinacloudapi.cn/v1.0/servicePrincipals?$search="appId:yourclientid"
Update Application:https://docs.microsoft.com/zh-cn/graph/api/application-update?view=graph-rest-1.0&tabs=http
List servicePrincipals:https://docs.microsoft.com/zh-cn/graph/api/serviceprincipal-list?view=graph-rest-1.0&tabs=http
requiredResourceAccess:https://docs.microsoft.com/zh-cn/graph/api/resources/requiredresourceaccess?view=graph-rest-1.0
https://microsoftgraph.chinacloudapi.cn/v1.0/servicePrincipals?$search="displayName:Microsoft Graph"&$count=true
https://microsoftgraph.chinacloudapi.cn/v1.0/servicePrincipals?$search="displayName:Azure Service Management"&$count=true
List servicePrincipals:https://docs.microsoft.com/zh-cn/graph/api/serviceprincipal-list?view=graph-rest-1.0&tabs=http
【Azure Developer】如何用Microsoft Graph API管理AAD Application里面的Permissions
原文:https://www.cnblogs.com/lulight/p/14470271.html