This topic provides information about how to plan, set up, and deploy Dynamics 365 Finance + Operations (on-premises) with Platform update 12-40.
The Local Business Data Yammer group is available. You can post questions or feedback you may have about the on-premises deployment there.
If you have questions or feedback about the content in this topic, please post them in the Comments section at the bottom of this page.
The Finance + Operations application consists of three main components:
These components depend on the following system software:
Microsoft Windows Server 2016 (only English OS installations are supported)
Microsoft SQL Server 2016 SP1 and SP2 (from Platform update 33), which has the following features:
Full-text index search is enabled.
SQL Server Reporting Services (SSRS) - This is deployed on BI virtual machines.
SQL Server Integration Services (SSIS) - This is deployed on AOS virtual machines.
Warning
Full Text Search must be enabled.
SQL Server Management Studio
Standalone Microsoft Azure Service Fabric
Microsoft Windows PowerShell 5.0 or later
Active Directory Federation Services (AD FS) on Windows Server 2016
Domain controller
Warning
The domain controller must be Microsoft Windows Server 2012 R2 or later and must have a domain functional level of 2012 R2 or more. For more information about domain functional levels, see the following topics:
Finance + Operations bits are distributed through Microsoft Dynamics Lifecycle Services (LCS). Before you can deploy, you must purchase license keys through the Enterprise Agreements channel and set up an on-premises project in LCS. Deployments can be initiated only through LCS. For more information about how to set up on-premises projects in LCS, see Set up on-premises projects in Lifecycle Services (LCS).
The on-premises application works with AD FS. To interact with LCS, you must also configure Azure Active Directory (AAD). To complete the deployment and configure the LCS Local agent, you will need AAD. If you do not already have an AAD tenant, you can get one for free by using one of the options provided by AAD. For more information, see How to get an Azure Active Directory tenant.
Finance + Operations uses standalone Service Fabric. For more information, see the Service Fabric documentation.
Setup of Finance + Operations will deploy a set of applications inside Service Fabric (SF). During deployment, each node in the cluster will be defined via configuration to have one of the following node types:
Finance + Operations falls under the standard Microsoft support policy about operation on non-Microsoft virtualization platforms, specifically VMware. For more information, see Support policy for Microsoft software. In short, we support our products in this environment. However, if we are asked to investigate an issue, we might first ask the customer to reproduce the issue without the virtualization platform or on the Microsoft virtualization platform.
If you are using VMWare, you must implement the fixes that are documented on the following web pages:
Important
Dynamics 365 Finance + Operations (on-premises) is not supported on any public cloud infrastructure, including Microsoft Azure Cloud services. However, it is supported to run on Microsoft Azure Stack Hub services.
The hardware configuration includes the following components:
For more information, see System requirements for on-premises deployments.
Plan your infrastructure and Service Fabric cluster based on the recommended sizing in Hardware sizing requirements for on-premises environments. For more information about how to plan the Service Fabric cluster, see Plan and prepare your Service Fabric standalone cluster deployment.
The following table shows an example of a hardware layout. This example is used throughout this topic to illustrate the setup. You will need to replace the machine names and IP addresses given in the following instructions with the names and IP addresses for the machines in your environment.
Note
The Primary node of the Service Fabric cluster must have at least three nodes. In this example, OrchestratorTypeis designated as the Primary node type.
| Machine purpose | SF Node type | Machine name | IP address |
|---|---|---|---|
| Domain controller | DAX7SQLAODC1 | 10.179.108.2 | |
| AD FS | DAX7SQLAOADFS1 | 10.179.108.3 | |
| File server | DAX7SQLAOFILE1 | 10.179.108.4 | |
| SQL Always-On cluster | DAX7SQLAOSQLA01 | 10.179.108.5 | |
| DAX7SQLAOSQLA02 | 10.179.108.6 | ||
| DAX7SQLAOSQLA | 10.179.108.9 | ||
| Client | SQLAOCLIENT1 | 10.179.108.11 | |
| AOS 1 | AOSNodeType | SQLAOSF1AOS1 | 10.179.108.12 |
| AOS 2 | AOSNodeType | SQLAOSF1AOS2 | 10.179.108.13 |
| AOS 3 | AOSNodeType | SQLAOSF1AOS3 | 10.179.108.14 |
| Orchestrator 1 | OrchestratorType | SQLAOSF1ORCH1 | 10.179.108.15 |
| Orchestrator 2 | OrchestratorType | SQLAOSF1ORCH2 | 10.179.108.16 |
| Orchestrator 3 | OrchestratorType | SQLAOSF1ORCH3 | 10.179.108.17 |
| Management Reporter node | MRType | SQLAOSMR1 | 10.179.108.18 |
| SSRS node | ReportServerType | SQLAOSFBIN1 | 10.179.108.10 |
Before you start the setup, the following prerequisites must be in place. The setup of these prerequisites is out of scope for this document.
The following prerequisite software is installed on the VMs by the infrastructure setup scripts downloaded from LCS.
| Node type | Component | Details |
|---|---|---|
| AOS | SNAC – ODBC driver 13 | /sql/connect/odbc/windows/release-notes-odbc-sql-server-windows#131 |
| AOS | SNAC – ODBC driver 17 | This driver is needed for upgrading to PU15 or higher: https://aka.ms/downloadmsodbcsql |
| AOS | The Microsoft .NET Framework version 2.0–3.5 (CLR 2.0) | Windows features: NET-Framework-Features, NET-Framework-Core, NET-HTTP-Activation, NET-Non-HTTP-Activ |
| AOS | The Microsoft .NET Framework version 4.0–4.6 (CLR 4.0) | Windows features: NET-Framework-45-Features, NET-Framework-45-Core, NET-Framework-45-ASPNET, NET-WCF-Services45, NET-WCF-TCP-PortSharing45 |
| AOS | The Microsoft .NET Framework version 4.7.2 (CLR 4.0) | https://dotnet.microsoft.com/download/thank-you/net472-offline |
| AOS | Internet Information Services (IIS) | Windows features: WAS, WAS-Process-Model, WAS-NET-Environment, WAS-Config-APIs, Web-Server, Web-WebServer, Web-Security, Web-Filtering, Web-App-Dev, Web-Net-Ext, Web-Mgmt-Tools, Web-Mgmt-Console |
| AOS | SQL Server Management Studio 17.2 | https://go.microsoft.com/fwlink/?linkid=854085 |
| AOS | Microsoft Visual C++ Redistributable Packages for Microsoft Visual Studio 2013 | https://support.microsoft.com/help/3179560 |
| AOS | Microsoft Visual C++ Redistributable Packages for Microsoft Visual Studio 2017 | https://lcs.dynamics.com/V2/SharedAssetLibrary > Models > "VC++ 17 Redistributables" |
| AOS | Microsoft Access Database Engine 2010 Redistributable | https://www.microsoft.com/download/details.aspx?id=13255 |
| BI | .NET Framework version 2.0–3.5 (CLR 2.0) | Windows features: NET-Framework-Features, NET-Framework-Core, NET-HTTP-Activation, NET-Non-HTTP-Activ |
| BI | .NET Framework version 4.0–4.6 (CLR 4.0) | Windows features: NET-Framework-45-Features, NET-Framework-45-Core, NET-Framework-45-ASPNET, NET-WCF-Services45, NET-WCF-TCP-PortSharing45 |
| BI | The Microsoft .NET Framework version 4.7.2 (CLR 4.0) | https://dotnet.microsoft.com/download/thank-you/net472-offline |
| BI | SQL Server Management Studio 17.2 | https://go.microsoft.com/fwlink/?linkid=854085 |
| MR | .NET Framework version 2.0–3.5 (CLR 2.0) | Windows features: NET-Framework-Features, NET-Framework-Core, NET-HTTP-Activation, NET-Non-HTTP-Activ |
| MR | .NET Framework version 4.0–4.6 (CLR 4.0) | Windows features: NET-Framework-45-Features, NET-Framework-45-Core, NET-Framework-45-ASPNET, NET-WCF-Services45, NET-WCF-TCP-PortSharing45 |
| MR | The Microsoft .NET Framework version 4.7.2 (CLR 4.0) | https://dotnet.microsoft.com/download/thank-you/net472-offline |
| MR | Visual C++ Redistributable Packages for Visual Studio 2013 | https://support.microsoft.com/help/3179560 |
| ORCH | The Microsoft .NET Framework version 4.0–4.8 (CLR 4.0) | https://dotnet.microsoft.com/download/thank-you/net48-offline |
The following steps must be completed to set up the infrastructure for Finance + Operations. Reading all the steps before you begin will make it easier to plan your setup.
We recommend that you use a publicly registered domain name for your production installation of AOS. In that way, the installation can be accessed outside the network, if outside access is required.
For example, if your company‘s domain is contoso.com, your zone for Finance + Operations might be d365ffo.onprem.contoso.com, and the host names might be as follows:
Secure Sockets Layer (SSL) certificates are required in order to secure a Service Fabric cluster and all the applications that are deployed. For your production and sandbox workloads, we recommend that you acquire certificates from a certificate authority (CA) such as DigiCert, Comodo, Symantec, GoDaddy, or GlobalSign. If your domain is set up with Active Directory Certificate Services (AD CS), you can create the certificates through AD CS. Each certificate must contain a private key that was created for key exchange, and it must be exportable to a Personal Information Exchange (.pfx) file.
Self-signed certificates can be used only for testing purposes. For convenience, the setup scripts provided in LCS include scripts that generate and export self-signed certificates. If you are using self-signed scripts, you will be instructed to run the creation scripts in later steps. As we‘ve mentioned, these certificates can be used for testing purposes only.
Recommended settings for certificates are:
| Purpose | Explanation | Additional requirements |
|---|---|---|
| SQL Server SSL certificate | This certificate is used to encrypt data that is transmitted across a network between an instance of SQL Server and a client application. |
The domain name of the certificate should match the fully qualified domain name (FQDN) of the SQL Server instance or listener. For example, if the SQL listener is hosted on the machine DAX7SQLAOSQLA, the certificate‘s DNS name is DAX7SQLAOSQLA.contoso.com. CN: DAX7SQLAOSQLA.contoso.com |
| Service Fabric Server certificate |
This certificate is used to help secure the node-to-node communication between the Service Fabric nodes. This certificate is also used as the Server certificate that is presented to the client that connects to the cluster. |
For this certificate you can also use SSL wild card certificate of your domain. For example, *.contoso.com. This is explained in more details below the table. Otherwise, use the following values: CN: sf.d365ffo.onprem.contoso.com |
| Service Fabric Client certificate | This certificate is used by clients to view and manage the Service Fabric cluster. | CN: client.d365ffo.onprem.contoso.com DNS Name: client.d365ffo.onprem.contoso.com |
| Encipherment Certificate | This certificate is used to encrypt sensitive information such as the SQL Server password and user account passwords. |
The certificate must be created by using the provider Microsoft Enhanced Cryptographic Provider v1.0. The certificate key usage must include Data Encipherment (10) and should not include Server authentication or Client authentication. For more information, see Managing secrets in Service Fabric applications. CN: axdataenciphermentcert |
| AOS SSL Certificate |
This certificate is used as the Server certificate that is presented to the client for the AOS website. It‘s also used to enable Windows Communication Foundation (WCF)/Simple Object Access Protocol (SOAP) certificates. |
You can use the same wild card certificate that you used as the Service Fabric Server certificate. Otherwise, use the following values: CN: ax.d365ffo.onprem.contoso.com |
| Session Authentication certificate | This certificate is used by AOS to help secure a user‘s session information. |
This certificate is also the File Share certificate that will be used at the time of deployment from LCS. CN: SessionAuthentication |
| Data Encryption certificate | This certificate is used by the AOS to encrypt sensitive information. |
This must be created using the provider Microsoft Enhanced RSA and AES Cryptographic Provider. CN: DataEncryption |
| Data Signing certificate | This certificate is used by the AOS to encrypt sensitive information. |
This is separate from the Data Encryption certificate and must be created using the provider Microsoft Enhanced RSA and AES Cryptographic Provider. CN: DataSigning |
| Financial Reporting client certificate | This certificate is used to help secure the communication between the Financial Reporting services and the AOS. |
CN: FinancialReporting |
| Reporting certificate | This certificate is used to help secure the communication between SSRS and the AOS. |
Do not reuse the Financial Reporting Client certificate. CN: ReportingService |
| On-Premises local agent certificate |
This certificate is used to help secure the communication between a local agent that is hosted on-premises and on LCS. This certificate enables the local agent to act on behalf of your Azure AD tenant, and to communicate with LCS to orchestrate and monitor deployments. Note: Only 1 on-premises local agent certificate is needed for a tenant. |
CN: OnPremLocalAgent |
SSL wild card certificate of your domain can be used to combine Service Fabric Server certificate and AOS SSL certificate.
The following is an example of a Service Fabric Server certificate combined with an AOS SSL certificate.
CN = *.d365ffo.onprem.contoso.com
DNS Name=ax.d365ffo.onprem.contoso.com
DNS Name=sf.d365ffo.onprem.contoso.com
DNS Name=*.d365ffo.onprem.contoso.com
Note
The wild card certificate allows you to secure only the first-level subdomain of the domain to which it is issued.
You must create several user or service accounts for Finance + Operations to work. You must create a combination of group managed service accounts (gMSAs), domain accounts, and SQL accounts. The following table shows the user accounts, their purpose, and example names that will be used in this topic.
| User account | Type | Purpose | User name |
|---|---|---|---|
| Financial Reporting Application Service Account | gMSA | Contoso\svc-FRAS$ | |
| Financial Reporting Process Service Account | gMSA | Contoso\svc-FRPS$ | |
| Financial Reporting Click Once Designer Service Account | gMSA | Contoso\svc-FRCO$ | |
| AOS Service Account | gMSA | This user should be created for future proofing. We plan to enable AOS to work with the gMSA in upcoming releases. By creating this user at the time of setup, you will help to ensure a seamless transition to the gMSA. | Contoso\svc-AXSF$ |
| AOS Service Account | Domain account | AOS uses this user in the general availability (GA) release. | Contoso\AXServiceUser |
| AOS SQL DB Admin user | SQL user | Finance + Operations uses this user to authenticate with SQL*. This user will also be replaced by the gMSA user in upcoming releases**. | AXDBAdmin |
| Local Deployment Agent Service Account | gMSA | This account is used by the local agent to orchestrate the deployment on various nodes. | Contoso\Svc-LocalAgent$ |
* If the password of the SQL user contains special characters, this could cause problems during deployment.
** The SQL user name and password for SQL authentication are secured because they are encrypted and stored in the file share.
DNS is integrated with AD DS, and lets you organize, manage, and find resources in a network. The following instructions provide steps to create a DNS forward lookup zone and A records for the AOS host name and Service Fabric cluster. In this example setup, the DNS zone name is d365ffo.onprem.contoso.com, and the A records/host names are as follows:
Use the following procedure to add a DNS zone.
In the new DNS zone, create one A record that is named ax.d365ffo.onprem.contoso.com for each Service Fabric cluster node of the AOSNodeType type. Don‘t create A records for the other node types.
In the new DNS zone, create an A record that is named sf.d365ffo.onprem.contoso.com for each Service Fabric cluster node of the OrchestratorType type. Don‘t create A records for the other node types.
Join each VM to the domain by completing the steps in the Join a Computer to a Domain document. Alternatively, use the following Windows PowerShell script.
$domainName = Read-Host -Prompt ‘Specify domain name (ex: contoso.com)‘
Add-Computer -DomainName $domainName -Credential (Get-Credential -Message ‘Enter domain credential‘)
Important
You must restart the VMs after you join them to the domain.
We have provided several scripts to help improve the setup experience. Follow these steps to download the setup scripts from LCS.
Important
The scripts must be executed from a computer in the same domain that the on-premises infrastructure is in.
Note
If you need the older version for Platform update 8 or Platform update 11, download version 1.
Important
Ensure all edits are made to the ConfigTemplate.xml file in this folder.
The infrastructure setup scripts use the following configuration files to drive the setup.
Note
Configuration files must be updated based on your environment for the setup scripts to work correctly. Be sure to update these files with the proper computer names, IP addresses, service accounts, and domain based on your setup.
infrastructure\ConfigTemplate.xml describes:
Service Accounts that are needed for the application to operate
Certificates necessary for securing communications
Database configuration
Service Fabric cluster configuration
Important
Make sure that there are three fault domains for OrchestratorType when you configure Service Fabric cluster. Make sure that no more than one type of node is deployed in a single machine when you configure Service Fabric cluster.
For each Service Fabric node type, infrastructure\D365FO-OP\NodeTopologyDefinition.xml describes:
For each database, infrastructure\D365FO-OP\DatabaseTopologyDefinition.xml describes:
Navigate to the machine that has the unzipped infrastructure scripts in the infrastructure folder.
Copy the infrastructure folder to the domain controller machine.
Start Windows PowerShell in elevated mode, change the directory to the infrastructure folder, and run the following commands.
Important
The following script doesn‘t create a domain user AxServiceUser for you. You must create it yourself.
Import-Module .\D365FO-OP\D365FO-OP.psd1
New-D365FOGMSAAccounts -ConfigurationFilePath .\ConfigTemplate.xml
Add the AOS Service Accounts, Contoso\svc-AXSF$ and Contoso\AXServiceUser to the local administrators group for all AOS machines. For more information, see Add a member to local group.
If you must make changes to accounts or machines, update the ConfigTemplate.xml file in the original infrastructure folder, copy it to this machine and then run the following script.
Update-D365FOGMSAAccounts -ConfigurationFilePath .\ConfigTemplate.xml
Navigate to the machine that has the infrastructure folder.
Generate certificates:
If you must generate self-signed certificates:
# Create self-signed certs
.\New-SelfSignedCertificates.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
If you want to generate Active Directory Certificate Services (AD CS) certificates:
.\New-ADCSCertificates.ps1 -ConfigurationFilePath .\ConfigTemplate.xml -CreateTemplates
.\New-ADCSCertificates.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
Note
The AD CS scripts need to run on a Domain Controller, or a Windows Server with Remote Server Admin Tools installed.
If you‘re using SSL certificates that were already generated, skip the certificate generation and update the thumbprints in the configTemplate.xml file. The certificates need to be installed in the CurrentUser\My store and their private keys must be exportable.
Warning
Because of a leading not-printable special character, which is difficult to determine when present, the cert manager should not be used to copy thumbprints. If the not-printable special character is present, you will get the error, X509 certificate not valid. To retrieve the thumbprints, see results from PowerShell commands or run the following commands in PowerShell.
dir cert:\CurrentUser\My
dir cert:\LocalMachine\My
dir cert:\LocalMachine\Root
Specify a semi-colon separated list of users or groups in the ProtectTo tag for each certificate. Only Active directory users and groups specified in the ProtectTo tag will have permissions to import the certificates that are exported using the scripts. Passwords are not supported by the script to protect the exported certificates
Export the certificates into .pfx files. As part of the export, this script will check that your certificates have the correct cryptographic provider set.
# Exports Pfx files into a directory VMs\<VMName>, all the certs will be written to infrastructure\Certs folder.
.\Export-PfxFiles.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
Export the scripts that must be run on each VM.
# Exports the script files to be execute on each VM into a directory VMs\<VMName>.
.\Export-Scripts.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
Download the following Microsoft Windows Installers (MSIs) into a file share that is accessible by all VMs.
| Component | Download link | Expected file name |
|---|---|---|
| SNAC – ODBC driver 13 | /sql/connect/odbc/windows/release-notes-odbc-sql-server-windows#131 | msodbcsql.msi |
| SNAC – ODBC driver 17 | https://aka.ms/downloadmsodbcsql | msodbcsql_17.msi |
| Microsoft SQL Server Management Studio 17.5 | /sql/ssms/download-sql-server-management-studio-ssms | SSMS-Setup-*.exe |
| Microsoft Visual C++ Redistributable Packages for Microsoft Visual Studio 2013 | https://support.microsoft.com/help/3179560 | vcredist_x64.exe |
| Microsoft Visual C++ Redistributable Packages for Microsoft Visual Studio 2017 | Go to https://lcs.dynamics.com/V2/SharedAssetLibrary, select Model as the asset type, and then select VC++ 17 Redistributables. | vc_redist.x64_14_16_27024.exe |
| Microsoft Access Database Engine 2010 Redistributable | https://www.microsoft.com/download/details.aspx?id=13255 | AccessDatabaseEngine_x64.exe |
| The Microsoft .NET Framework version 4.8 (CLR 4.0) | https://dotnet.microsoft.com/download/thank-you/net48-offline | ndp48-x86-x64-allos-enu.exe |
| The Microsoft .NET Framework version 4.7.2 (CLR 4.0) | https://dotnet.microsoft.com/download/thank-you/net472-offline | ndp472-x86-x64-allos-enu.exe |
Important
Note
The following section requires execution on multiple VMs. This process can be eased by using the supplied remoting scripts, which provide the option of running the necessary scripts from a single machine, such as the same machine used to execute .\Export-Scripts.ps1. The remoting scripts, when available, are declared after a "# If Remoting" comment in the PowerShell sections. When the remoting scripts are used, you may not need to execute the remaining scripts in a section, please see the section text for cases such as that. Remoting uses WinRM and requires CredSSP to be enabled in certain cases. The enabling and disabling of CredSSP is handled by the remoting module on a per-execution basis. Keeping CredSSP enabled when it is not in use is not advised, as it introduces security risks in the shape of credential theft. See the Tear down CredSSP section when you are finished setting up.
Copy the contents of each infrastructure\VMs<VMName> folder into the corresponding VM (if remoting scripts are used, they will automatically copy the content to the target VMs), and then run the following scripts as an Administrator.
# Install pre-req software on the VMs.
# If Remoting, execute
# .\Configure-PreReqs-AllVMs.ps1 -MSIFilePath <share folder path of the MSIs> -ConfigurationFilePath .\ConfigTemplate.xml
.\Configure-PreReqs.ps1 -MSIFilePath <path of the MSIs>
Important
.\Configure-PreReqs.ps1 script after each restart until all of the prerequisites are installed. In the case of remoting, rerun the AllVMs script when all of the machines are back online.Run the following scripts, if they exist, to complete the VM setup.
# If Remoting, only execute
# .\Complete-PreReqs-AllVMs.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
# Note: Script "Add-GMSAOnVM.ps1" is not present on BI node
.\Add-GMSAOnVM.ps1
.\Import-PfxFiles.ps1
.\Set-CertificateAcls.ps1
Run the following script to validate the VM setup.
# If Remoting, execute
# .\Test-D365FOConfiguration-AllVMs.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
.\Test-D365FOConfiguration.ps1
Important
If remoting was used, be sure to execute the clean up steps when the setup is complete. See the 20. Tear down CredSSP section.
Download the Service Fabric standalone installation package onto one of your Service Fabric nodes. After the zip file is downloaded, unblock it by right-clicking the zip file and then selecting Properties. In the dialog box, select the Unblock check box in the lower right.
Copy the zip file to one of the nodes in the Service Fabric cluster, and unzip it. Ensure the infrastructure folder has access to this folder.
Navigate to the infrastructure folder and execute the following command to generate the Service Fabric ClusterConfig.json file.
.\New-SFClusterConfig.ps1 -ConfigurationFilePath .\ConfigTemplate.xml -TemplateConfig <ServiceFabricStandaloneInstallerPath>\ClusterConfig.X509.MultiMachine.json
Additional modifications to your cluster configuration may be necessary based on your environment. For more information, see, Step 1B: Create a multi-machine cluster, Secure a standalone cluster on Windows using X.509 certificates, and Create a standalone cluster running on Windows Server.
Copy the generated ClusterConfig.json file to the <ServiceFabricStandaloneInstallerPath>.
Navigate to the <ServiceFabricStandaloneInstallerPath> in Windows PowerShell by using elevated privileges. Run the following command to test ClusterConfig.
.\TestConfiguration.ps1 -ClusterConfigFilePath .\clusterConfig.json
If the test is successful, run the following command to deploy the cluster.
# If using offline (internet-disconnected) install
# .\CreateServiceFabricCluster.ps1 -ClusterConfigFilePath .\ClusterConfig.json -FabricRuntimePackagePath <Path to MicrosoftAzureServiceFabric.cab download>
.\CreateServiceFabricCluster.ps1 -ClusterConfigFilePath .\ClusterConfig.json
After the cluster is created, open the Service Fabric explorer on any client machine to validate the installation.
https://sf.d365ffo.onprem.contoso.com:19080, where sf.d365ffo.onprem.contoso.com is the host name of the Service Fabric cluster that is specified in the zone. If DNS name resolution isn‘t configured, use the IP address of the machine.Important
If your client machine is a server machine like Windows Server 2016, you must turn off the IE Enhanced Security Configuration when you access the Service Fabric explorer page. If any antivirus software is installed, ensure you set exclusion following the guidance in the Service Fabric documentation.
Deployment and servicing of Finance + Operations is orchestrated through LCS by using an on-premises local agent. To establish connectivity from LCS to the Finance + Operations tenant, you must configure a certificate that enables the local agent to act on behalf on your Azure AD tenant (for example, Contoso.onmicrosoft.com).
Use the on-premises agent certificate that you acquired from a certificate authority or the self-signed certificate that you generated by using scripts.
The on-premises agent certificate can be reused across multiple sandbox and production environments per tenant.
Only user accounts that have the Global Administrator directory role can add certificates to authorize LCS. By default, the person who signs up for Microsoft 365 for your organization is the global administrator for the directory.
Important
Sign in to the customer‘s Azure portal to verify that you have the Global Administrator directory role.
Determine whether the certificate is already registered by running the following script from the Infrastructurefolder.
# If you have issues downloading the Azure PowerShell Az module, run the following:
# [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
Install-Module Az
Import-Module Az
.\Add-CertToServicePrincipal.ps1 -CertificateThumbprint ‘OnPremLocalAgent Certificate Thumbprint‘ -Test
Important
If you previously installed AzureRM, please remove it as it may not be compatible with any existing AzureRM installs in PowerShell 5.1 for Windows. For more information, Migrate Azure PowerShell from AzureRM to Az.
If the script indicates that the certificate isn‘t registered, run the following command.
.\Add-CertToServicePrincipal.ps1 -CertificateThumbprint ‘OnPremLocalAgent Certificate Thumbprint‘
Note
If you have multiple tenants associated with the login account, you can pass the tenant ID as a parameter to ensure that the context is set to the correct tenant.
PowerShell.\Add-CertToServicePrincipal.ps1 -CertificateThumbprint ‘OnPremLocalAgent Certificate Thumbprint‘ -TenantId ‘xxxx-xxxx-xxxx-xxxx‘
You must set up the following SMB 3.0 file shares:
A file share that stores user documents that are uploaded to AOS (for example, \\DAX7SQLAOFILE1\aos-storage).
A file share that stores the latest build and configuration files to orchestrate the deployment (for example, \\DAX7SQLAOFILE1\agent).
Warning
Keep this file share path as short as possible to avoid exceeding the maximum path length on the files that will be put in the share.
For information about how to enable SMB 3.0, see SMB Security Enhancements.
Important
On the file share machine, run the following command.
Install-WindowsFeature -Name FS-FileServer -IncludeAllSubFeature -IncludeManagementTools
Follow these steps to set up the \\DAX7SQLAOFILE1\aos-storage file share:
In Server Manager, select File and Storage Services > Shares.
Select Tasks > New Share to create a new share. Name the share aos-storage.
Leave Allow caching of share selected.
Check Encrypt data access.
Grant Modify permissions for every machine in the Service Fabric cluster except OrchestratorType.
Grant Modify permissions for the user AOS domain user (contoso\AXServiceUser) and the gMSA user (contoso\svc-AXSF$).
Note
You may need to enable Computers under Object Types to add machines or enable Service Accountsunder Object Types to add service accounts.
Follow these steps to set up the \\DAX7SQLAOFILE1\agent file share:
# Specify user names
$AOSDomainUser = ‘Contoso\AXServiceUser‘;
$LocalDeploymentAgent = ‘contoso\svc-LocalAgent$‘;
# Specify the path
$AosStorageFolderPath = ‘D:\aos-storage‘;
$AgentFolderPath = ‘D:\agent‘;
# Create new directory
$AosStorageFolder = New-Item -type directory -path $AosStorageFolderPath;
$AgentFolder = New-Item -type directory -path $AgentFolderPath;
# Create new SMB share
New-SmbShare –Name aos-storage -Path $AosStorageFolderPath -EncryptData $True
New-SmbShare –Name agent -Path $AgentFolderPath
# Set ACL for AOS storage folder
$Acl = Get-Acl $AosStorageFolder.FullName;
$Ar = New-Object system.security.accesscontrol.filesystemaccessrule($AOSDomainUser,‘Modify‘,‘Allow‘);
$Acl.SetAccessRule($Ar);
Set-Acl $AosStorageFolder.FullName $Acl;
# Set ACL for AgentFolder
$Acl = Get-Acl $AgentFolder.FullName;
$Ar = New-Object system.security.accesscontrol.filesystemaccessrule($LocalDeploymentAgent,‘FullControl‘,‘Allow‘);
$Acl.SetAccessRule($Ar);
Set-Acl $AgentFolder.FullName $Acl;
Install SQL Server 2016 SP2 with high availability. (Unless you‘re deploying in a sandbox environment, where one instance of SQL Server is sufficient. You may want to install SQL Server with high availability in sandbox environments to test high-availability scenarios.)
Important
You must enable the SQL Server and Windows Authentication mode.
You can install SQL Server with high availability either as SQL clusters that include a Storage Area Network (SAN) or in an Always-On configuration. Verify that the Database Engine, SSRS, Full-Text Search, and Management Tools are already installed.
Note
Make sure that Always-On is set up as described in Select Initial Data Synchronization Page (Always On Availability Group Wizards), and follow the instructions in To Prepare Secondary Databases Manually.
Run the SQL service as a domain user or a group-managed service account.
Get an SSL certificate from a certificate authority to configure SQL Server for Finance + Operations. For testing purposes, you can create and use a self-signed certificate or an AD CS certificate. You will need to replace the computer name and domain name in the following examples.
Certificates for an Always-On SQL instance
If you are setting up testing certificates for Always-On, use the following remoting script. This will perform the same as the following manual script and steps a-e.
Self-signed certificate
.\New-SelfSigned-SQLCert-AllVMs.ps1 -SqlMachineNames SQL1,SQL2 -SqlListenerName SQL-LS -ProtectTo CONTOSO\dynuser
AD CS certificate
.\New-ADCS-SQLCert-AllVMs.ps1 -SqlMachineNames SQL1,SQL2 -SqlListenerName SQL-LS -ProtectTo CONTOSO\dynuser
Manual self-signed steps for an Always-On SQL instance or Windows Server Failover Clustering with SQL Server
For each node of the SQL cluster, follow these steps.
# Manually create certificate for each SQL Node (i.e. 2 nodes = 2 certificates)
# Run script on each node
$computerName = $env:COMPUTERNAME.ToLower()
$domain = $env:USERDNSDOMAIN.ToLower()
$listenerName = ‘dax7sqlaosqla‘
$cert = New-SelfSignedCertificate -Subject "$computerName.$domain" -DnsName "$listenerName.$domain", $listenerName, $computerName -Provider ‘Microsoft Enhanced RSA and AES Cryptographic Provider‘ -CertStoreLocation "cert:\LocalMachine\My" -KeyAlgorithm "RSA" -HashAlgorithm "sha256" -KeyLength 2048
Note
For more information, see How to enable SSL encryption for an instance of SQL Server by using Microsoft Management Console.
Important
If remoting was used, be sure to execute the clean up steps when the setup is complete. See the 20. Tear down CredSSP section for more information.
Sign in to LCS.
On the dashboard, select the Shared asset library tile.
On the Model tab, select the demo data for the release that you want and download the zip file.
| Release | Demo data |
|---|---|
| On-premises General Availability (GA) release | Dynamics 365 for Operations on-premises - Demo data |
| On-premises Platform Update 11 Nov 2017 release | Dynamics 365 for Operations on-premises, Enterprise edition - Update 11 Demo data |
| On-premises Platform Update 12 Mar 2018 release | Dynamics 365 for Operations on-premises, Enterprise edition - Update 12 Demo data |
The zip file contains empty and demo data .bak files. Select the .bak file, based on your requirements. For example, if you require demo data, download the AxBootstrapDB_Demodata.bak file.
Ensure the database section in the infrastructure\ConfigTempate.xml is configured correctly with the following:
Warning
The user running the SQL service and the user running the scripts should have READ access on the folder or share where the backup file is located.
If a database with the same name exists, the database will be reused.
Copy the infrastructure folder to the SQL Server machine and navigate to it in a PowerShell window with elevate privileges.
Execute the following script.
.\Initialize-Database.ps1 -ConfigurationFilePath .\ConfigTemplate.xml -ComponentName Orchestrator
The script will do the following:
Execute the following scripts.
.\Initialize-Database.ps1 -ConfigurationFilePath .\ConfigTemplate.xml -ComponentName AOS
.\Configure-Database.ps1 -ConfigurationFilePath .\ConfigTemplate.xml -ComponentName AOS
The Initialize-Database.ps1 script will do the following:
Restore the database from the specified backup file.
Create a new user that has SQL authentication enabled (axdbadmin).
Map users to database roles based on the following table for AXDB.
| User | Type | Database role |
|---|---|---|
| svc-AXSF$ | gMSA | db_owner |
| svc-LocalAgent$ | gMSA | db_owner |
| svc-FRPS$ | gMSA | db_owner |
| svc-FRAS$ | gMSA | db_owner |
| axdbadmin | SqlUser | db_owner |
Map users to database roles based on the following table for TempDB.
| User | Type | Database role |
|---|---|---|
| svc-AXSF$ | gMSA | db_datareader, db_datawriter, db_ddladmin |
| axdbadmin | SqlUser | db_datareader, db_datawriter, db_ddladmin |
The Configure-Database.ps1 script will do the following:
Run the following command to reset the database users.
.\Reset-DatabaseUsers.ps1 -DatabaseServer ‘<FQDN of the SQL server>‘ -DatabaseName ‘<AX database name>‘
Execute the following script.
.\Initialize-Database.ps1 -ConfigurationFilePath .\ConfigTemplate.xml -ComponentName MR
The script will do the following:
Create an empty database named FinancialReporting.
Map the users to database roles based on the following table.
| User | Type | Database role |
|---|---|---|
| svc-LocalAgent$ | gMSA | db_owner |
| svc-FRPS$ | gMSA | db_owner |
| svc-FRAS$ | gMSA | db_owner |
On any client machine, install the encipherment certificate in the LocalMachine\My certificate store.
Grant the current user read access to the private key of this certificate.
Create the Credentials.json file, as shown here.
{
"AosPrincipal": {
"AccountPassword": "<encryptedDomainUserPassword>"
},
"AosSqlAuth": {
"SqlUser": "<encryptedSqlUser>",
"SqlPwd": "<encryptedSqlPassword>"
}
}
Copy the .json file to the SMB file share, \\AX7SQLAOFILE1\agent\Credentials\Credentials.json.
Update the Credentials.json file with encrypted values.
# Service fabric API to encrypt text and copy it to the clipboard.
Invoke-ServiceFabricEncryptText -Text ‘<textToEncrypt>‘ -CertThumbprint ‘<DataEncipherment Thumbprint>‘ -CertStore -StoreLocation LocalMachine -StoreName My | Set-Clipboard
Important
Before you can invoke Invoke-ServiceFabricEncryptText, you need to install Microsoft Azure Service Fabric SDK. If you encounter the following error, "Invoke-ServiceFabricEncryptText is not recognized command" after you install the Azure Service Fabric SDK, restart the computer and retry.
Warning
After you‘ve finished invoking all Invoke-ServiceFabricEncryptText commands, remember to delete the Windows PowerShell history. Otherwise, your non-encrypted credentials will be visible.
To enable Data management and Integration workloads, SSIS must be installed on each of the AOS virtual machines. Complete the following steps on each AOS virtual machine.
For more information, see Install integration services.
Important
You must install then database engine when you install SSRS.
Before you can complete this procedure, AD FS must be deployed on Windows Server 2016. For information about how to deploy AD FS, see Deployment Guide Windows Server 2016 and 2012 R2 AD FS Deployment Guide.
Finance + Operations requires additional configuration beyond the default out-of-box configuration of AD FS. The following Windows PowerShell commands must be run on the machine where the AD FS role service is installed. The user account must have enough permissions to administer AD FS. For example, the user must have a domain administrator account. For complex AD FS scenarios, consult your domain administrator.
Configure the AD FS identifier so that it matches the AD FS token issuer.
This command is related to adding new users using the Import users option on the Users page (System administration > Users > Users) in the Finance + Operations client.
$adfsProperties = Get-AdfsProperties
Set-AdfsProperties -Identifier $adfsProperties.IdTokenIssuer
You should disable Windows Integrated Authentication (WIA) for intranet authentication connections, unless you‘ve configured AD FS for mixed environments. For more information about how to configure WIA so that it can be used with AD FS, see Configure browsers to use Windows Integrated Authentication (WIA) with AD FS.
This command is related to using forms authentication upon signing into the Finance + Operations client. Other options, such as single sign-on, may be available which require additional setup.
Set-AdfsGlobalAuthenticationPolicy -PrimaryIntranetAuthenticationProvider FormsAuthentication, MicrosoftPassportAuthentication
For sign-in, the user‘s email address must be an acceptable authentication input.
This command is related to setting up email claims. Other options, such as transformation rules, may be available which require additional setup.
Add-Type -AssemblyName System.Net
$fqdn = ([System.Net.Dns]::GetHostEntry(‘localhost‘).HostName).ToLower()
$domainName = $fqdn.Substring($fqdn.IndexOf(‘.‘)+1)
Set-AdfsClaimsProviderTrust -TargetIdentifier ‘AD AUTHORITY‘ -AlternateLoginID mail -LookupForests $domainName
In order for AD FS to trust Finance + Operations for the exchange of authentication, various application entries must be registered in AD FS under an AD FS application group. To speed up the setup process and help reduce errors, you can use the following script for registration. Copy the Publish-ADFSApplicationGroup.ps1 script and D365FO-OP directory to a machine where the AD FS role service is installed. Then run the script by using a user account that has enough permissions to administer AD FS. (For example, use an administrator account.)
For more information about how to use the script, see the documentation that is listed in the script. Make a note of the client IDs that are specified in the output, because you will need this information in LCS in a later step. Should you lose the client IDs, log in to the machine which has AD FS installed, open Server Manager > Tools > AD FS Management > Application Groups > Microsoft Dynamics 365 for Operations On-premises and find the client IDs under the native applications.
Note
If you want to reuse your previously configured AD FS server for additional environments, see Reuse the same AD FS instance for multiple environments.
# Host URL is your DNS record\host name for accessing the AOS
.\Publish-ADFSApplicationGroup.ps1 -HostUrl ‘https://ax.d365ffo.onprem.contoso.com‘

Finally, make sure that you can access the AD FS OpenID Configuration URL on a Service Fabric node of the AOSNodeType type. To perform this check, try to open https://<adfs-dns-name>/adfs/.well-known/openid-configuration in a web browser. If you receive a message that states that the site isn‘t secure, you haven‘t added your AD FS SSL certificate to the Trusted Root Certification Authorities store. This step is described in the AD FS deployment guide, and if you are using remoting, you can use the following script to install the certificate on all nodes in the Service Fabric cluster:
# If remoting, execute
.\Install-ADFSCert-AllVMs.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
If you successfully access the URL, a JavaScript Object Notation (JSON) file is returned that contains your AD FS configuration, and you will see that your AD FS URL is trusted.
You‘ve now completed the setup of the infrastructure. The following sections describe how to navigate to LCS to set up your connector and deploy your Finance + Operations environment.
Sign in to LCS, and open the on-premises implementation project.
On the hamburger menu, select Project settings.

Select On-premises connectors.
Select Add to create a new connector.
On the Setup host infrastructure tab, download the agent installer.
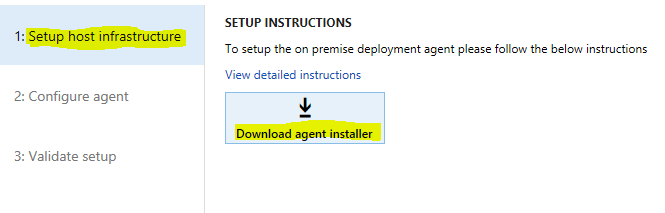
Verify that the zip file is unblocked. Right-click the file, and then select Properties. In the dialog box, select Unblock.
Unzip the agent installer on one of the Service Fabric nodes of the OrchestratorType type.
On the Configure agent tab, enter the configuration settings. Execute the following script on any machine with access to it and the configuration file, to get the needed values.
.\Get-AgentConfiguration.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
Save the configuration, and then select Download configurations to download the localagent-config.json configuration file.
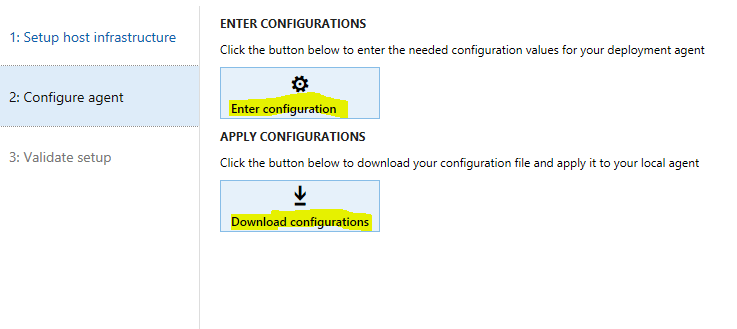
Copy the localagent-config.json file to the machine where the agent installer package is located.
In a Command Prompt window, run the following command by navigating to the folder that contains the agent installer.
LocalAgentCLI.exe Install <path of config.json>
Note
The user who runs this command must have db_owner permissions on the OrchestratorData database.
After the local agent is successfully installed, navigate back to your on-premises connector in LCS.
On the Validate setup tab, select Message agent to test for LCS connectivity to your local agent. When a connection is successfully established, the page will resemble the following illustration.

If any of the remoting scripts were used during setup, be sure to execute the following script when there are breaks in the setup process, or the setup has finished.
.\Disable-CredSSP-AllVMs.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
If the previous remoting PowerShell window was accidentally closed and CredSSP was left enabled, the script will disable it on all the machines specified in the configuration file.
In LCS, navigate to your on-premises project, go to Environment > Sandbox, and then select Configure. Execute the following script on the primary domain controller VM, which must have access to ADFS and the DNS server settings, to get the needed values.
.\Get-DeploymentSettings.ps1 -ConfigurationFilePath .\ConfigTemplate.xml
For new deployments, select your environment topology, and then complete the wizard to start your deployment.
If you have an existing Platform update 8 or Platform update 11 deployment:
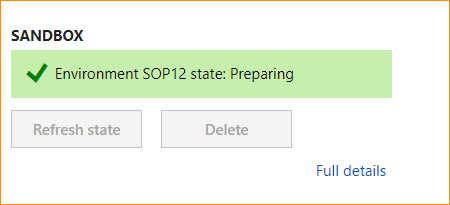
LCS will assemble the Service Fabric application packages for your environment during the preparation phase. It then sends a message to the local agent to start deployment. You will notice the Preparing status as below.
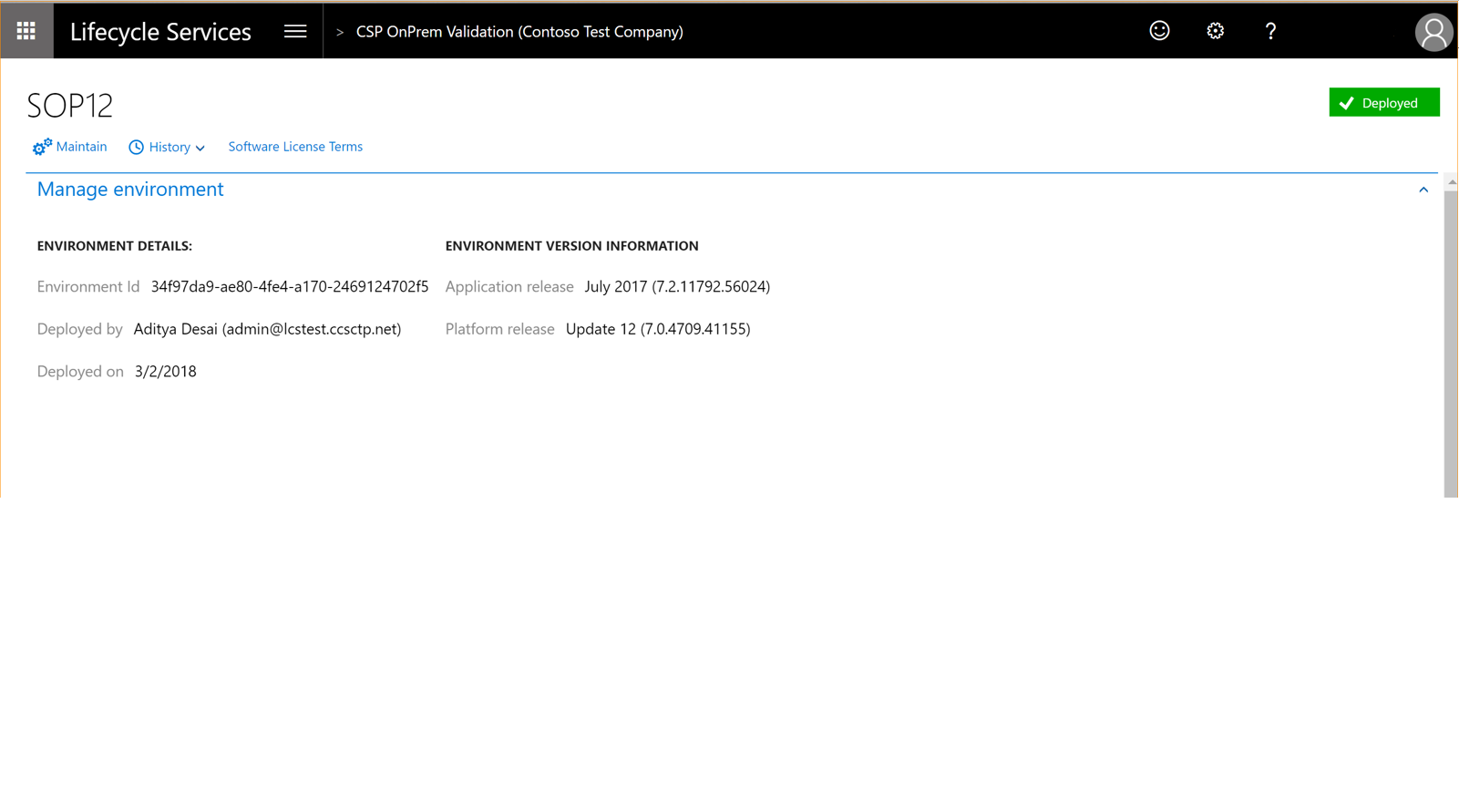
Click Full details to take you to the environment details page, as shown below.
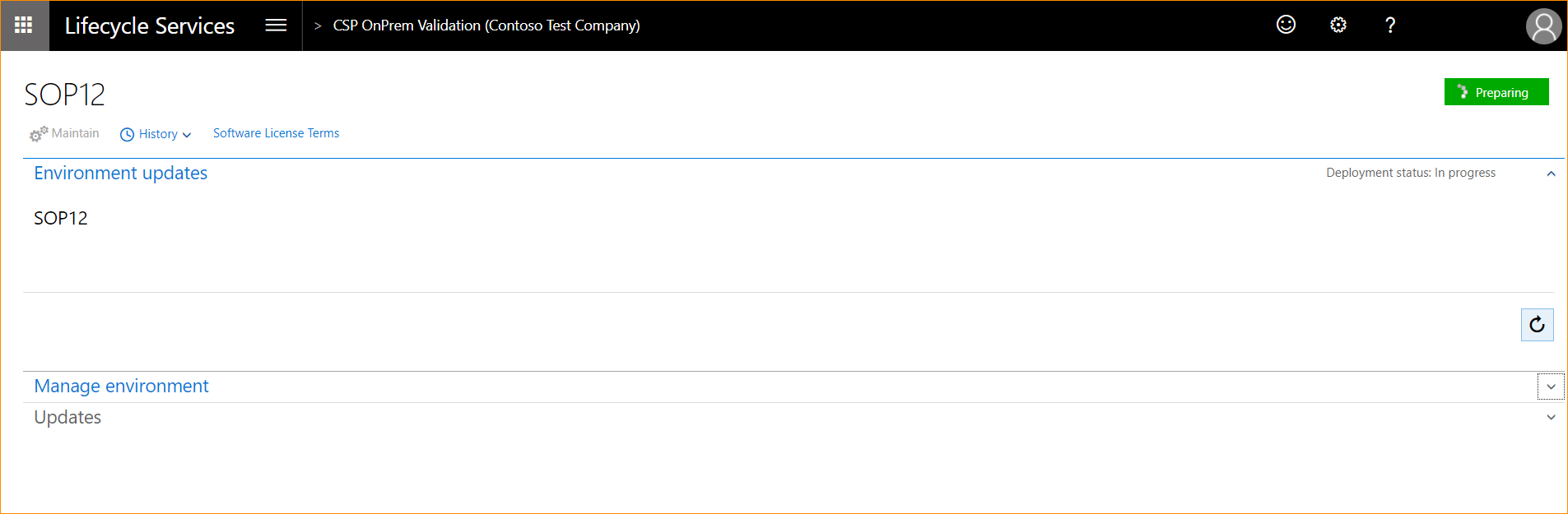
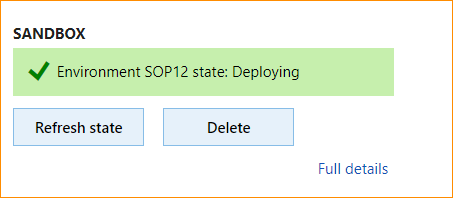
The local agent will now pick up the deployment request, start the deployment, and communicate back to LCS when the environment is ready. When deployment starts, the status will change to Deploying, as shown.
If the deployment fails, the Reconfigure button will become available for your environment in LCS, as shown below. Fix the underlying issue, click Reconfigure, update any configuration changes, and click Deploy to retry the deployment.
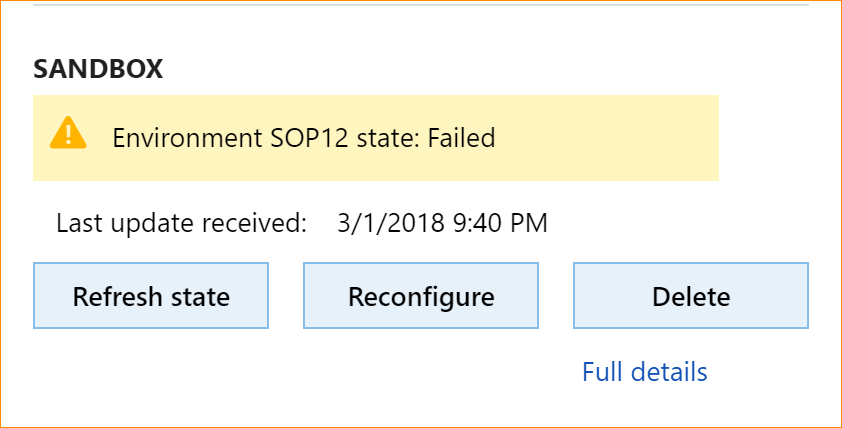
See the Reconfigure environments to take a new platform or topology topic for details about how to reconfigure. The following graphic shows a successful deployment.

In your browser, navigate to https://[yourD365FOdomain]/namespaces/AXSF, where yourD365FOdomain is the domain name that you defined in the Plan your domain name and DNS zones section of this topic.
Set up and deploy on-premises environments - Dynamics 365 FO
原文:https://www.cnblogs.com/lingdanglfw/p/14610854.html