//关闭防火墙
[root@zabbix ~]# systemctl stop firewalld
[root@mf1 ~]# systemctl stop firewalld
//创建脚本
[root@mf1 ~]# mkdir /scripts
[root@mf1 ~]# cd /scripts/
[root@mf1 scripts]# ls
[root@mf1 scripts]# vim check_process.sh
#!/bin/bash
count=$(ps -ef | grep -Ev "grep|$0" | grep -c "$1")
if [ $count -eq 0 ];then
echo "1"
else
echo "0"
fi
[root@mf1 scripts]# chmod +x check_process.sh
//用绝对路径执行脚本
[root@mf1 scripts]# ./check_process.sh /usr/local/apache/bin/httpd
0
输出为0,说明进程没问题
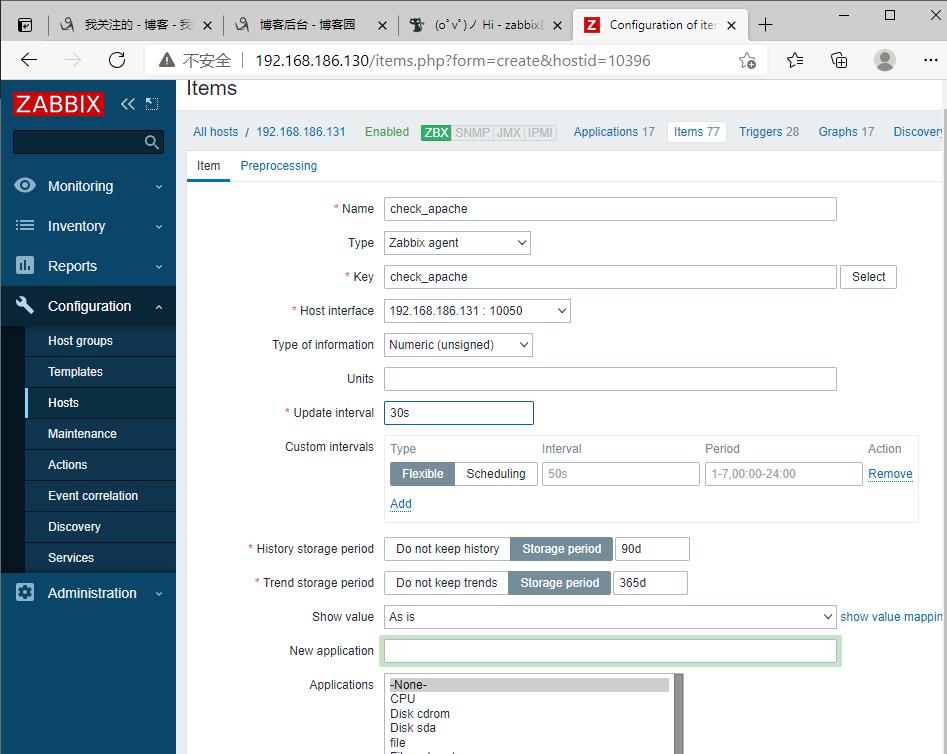
//进入zabbix_agentd.conf文件里,再最后面加入这两行
[root@mf1 scripts]# vim /usr/local/etc/zabbix_agentd.conf
。。。。。。
UnsafeUserParameters=1
UserParameter=check_apache,/scripts/check_process.sh /usr/local/apache/bin/httpd
[root@mf1 scripts]# pkill zabbix
[root@mf1 scripts]# zabbix_agentd
//在服务端上查看能否取到刚才配置脚本的值
[root@zabbix ~]# zabbix_get -s 192.168.186.131 -k check_apache
0
//手动触发报警
[root@mf1 scripts]# apachectl stop
[root@mf1 scripts]# yum -y install python36 //log.py作用:检查日志文件中是否有指定的关键字 第一个参数为日志文件名(必须有,相对路径、绝对路径均可) 第二个参数为seek position文件的路径(可选项,若不设置则默认为/tmp/logseek文件。相对路径、绝对路径均可) 第三个参数为搜索关键字,默认为 Error [root@mf1 scripts]# vim log.py #!/usr/bin/env python3 import sys import re def prePos(seekfile): global curpos try: cf = open(seekfile) except IOError: curpos = 0 return curpos except FileNotFoundError: curpos = 0 return curpos else: try: curpos = int(cf.readline().strip()) except ValueError: curpos = 0 cf.close() return curpos cf.close() return curpos def lastPos(filename): with open(filename) as lfile: if lfile.readline(): lfile.seek(0,2) else: return 0 lastPos = lfile.tell() return lastPos def getSeekFile(): try: seekfile = sys.argv[2] except IndexError: seekfile = ‘/tmp/logseek‘ return seekfile def getKey(): try: tagKey = str(sys.argv[3]) except IndexError: tagKey = ‘Error‘ return tagKey def getResult(filename,seekfile,tagkey): destPos = prePos(seekfile) curPos = lastPos(filename) if curPos < destPos: curpos = 0 try: f = open(filename) except IOError: print(‘Could not open file: %s‘ % filename) except FileNotFoundError: print(‘Could not open file: %s‘ % filename) else: f.seek(destPos) while curPos != 0 and f.tell() < curPos: rresult = f.readline().strip() global result if re.search(tagkey, rresult): result = 1 break else: result = 0 with open(seekfile,‘w‘) as sf: sf.write(str(curPos)) finally: f.close() return result if __name__ == "__main__": result = 0 curpos = 0 tagkey = getKey() seekfile = getSeekFile() result = getResult(sys.argv[1],seekfile,tagkey) print(result) [root@mf1 scripts]# chmod +x log.py [root@mf1 scripts]# ll total 28 -rwxr-xr-x 1 root root 142 Apr 28 20:26 check_process.sh -rwxr-xr-x 1 root root 21374 Apr 28 20:57 log.py [root@mf1 scripts]# touch /usr/local/apache/logs/error.log [root@mf1 scripts]# vim /usr/local/etc/zabbix_agentd.conf UnsafeUserParameters=check_logs[*],/scripts/log.py $1 $2 $3 [root@mf1 scripts]# pkill zabbix [root@mf1 scripts]# zabbix_agentd //在服务端上查看能否取到刚才配置py脚本的值
[root@zabbix ~]# zabbix_get -s 192.168.186.131 -k check_logs["/usr/local/apache/logs/error.log","/tmp/seek","Error"]
0
//手动触发报警
[root@mf1 scripts]# echo ‘Error‘ >> /usr/local/apache/logs/error.log
[root@mf1 scripts]#
//输出1表示主从有问题,0表示没问题() [root@mf1 scripts]# vim check_mysql_repl.sh #!/bin/bash count=$(mysql -uroot -e ‘show slave status\G‘|grep ‘ Running:‘|awk ‘{print $2}‘|grep -c ‘Yes‘) if [ $count -ne 2 ];then echo ‘1‘ else echo ‘0‘ fi [root@mf1 scripts]# chmod +x check_mysql_repl.sh //在文件最后面加入下面这行代码 [root@mf1 scripts]# vim /usr/local/etc/zabbix_agentd.conf UserParameter=check_mysql_repl,/scripts/check_mysql_repl.sh [root@mf1 scripts]# pkill zabbix [root@mf1 scripts]# zabbix_agentd //在服务端上查看能否取到刚才配置脚本的值
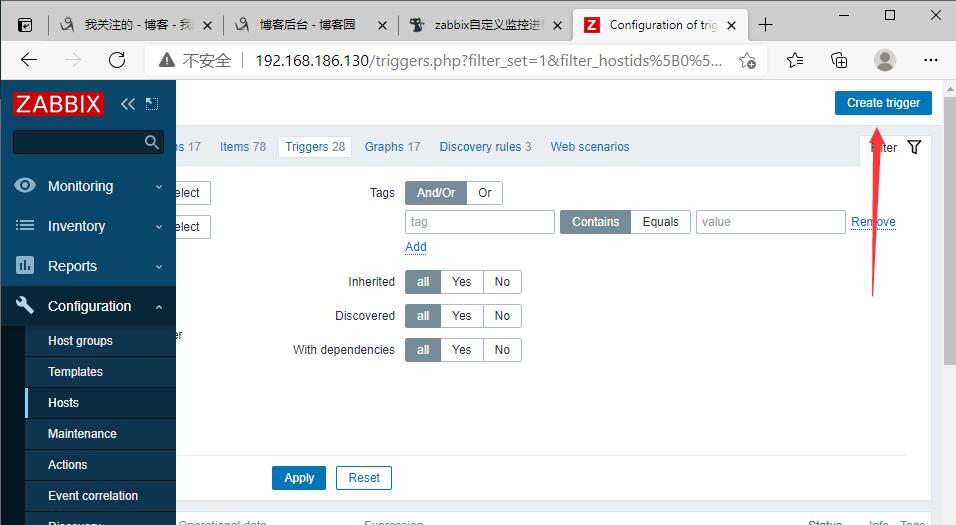
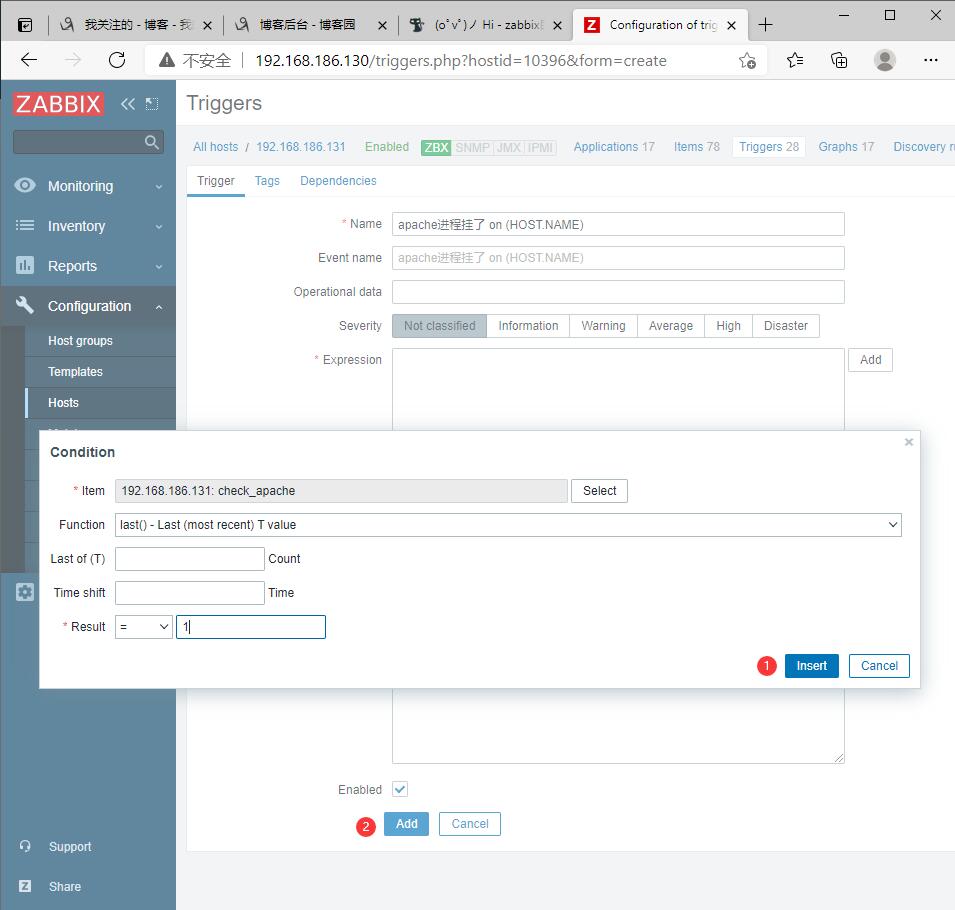
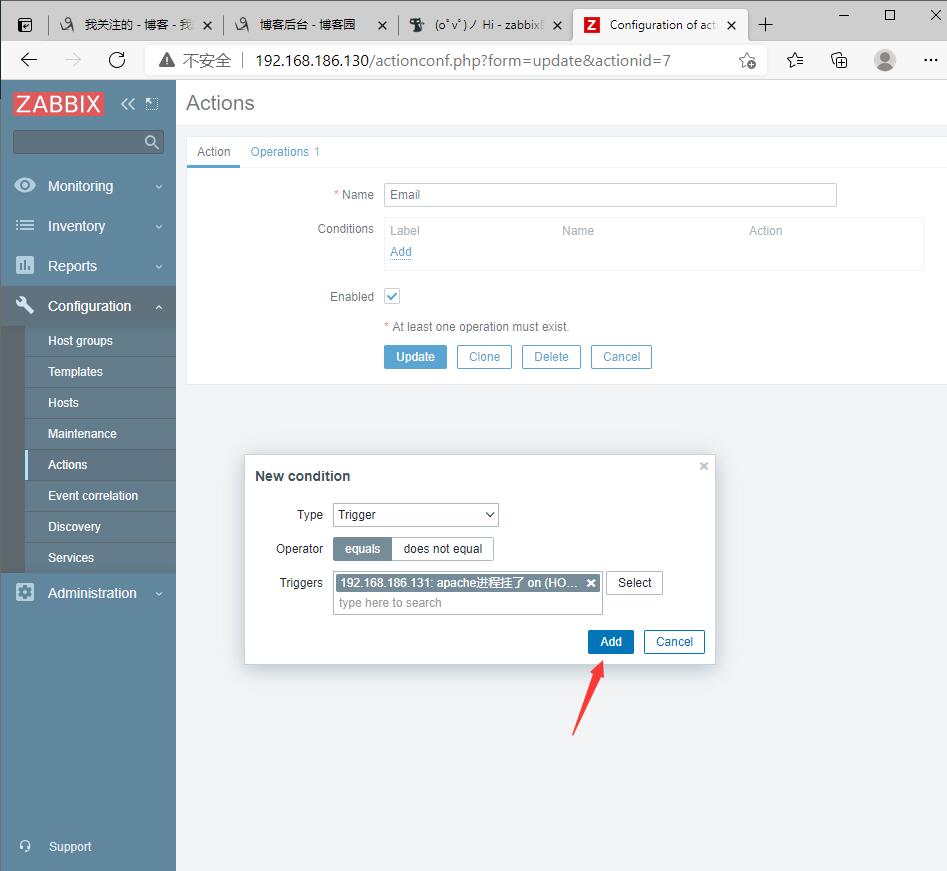
原文:https://www.cnblogs.com/mfdsg/p/14716279.html