Simplifies authentication and authorization for web applications.
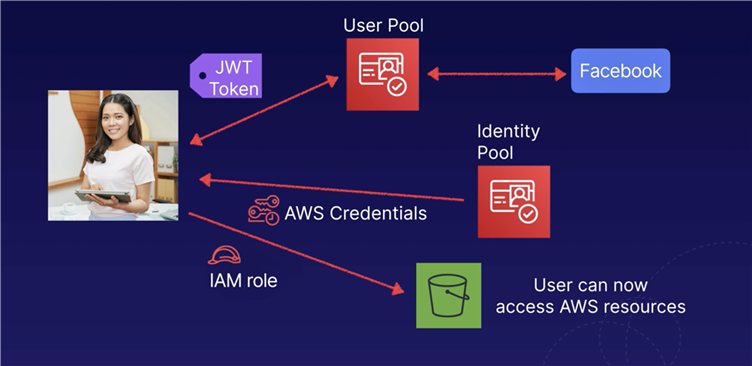
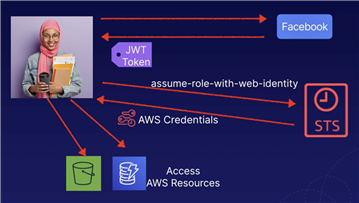
An Authentication token JWT is exchanged for temporary AWS credentials, allowing users to assume an IAM role, with permission to access AWS resources.
Users access AWS resources after successfully authenticating with a web-based identity prvoider like Facebook, Amazon, or Google.
Following successful authentication, users receive an authentication code from the web ID provider.
Users can trade this authentication code for temporary AWS security credentials, authorizing access to AWS resources.
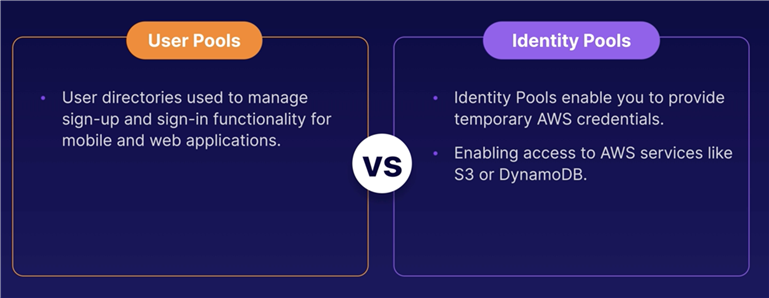
Handle sign-up and sign-in functionality for mobile and web applications.
Users can sign-in-directly to the User Pool, or using Facebook, Google, Amazon.
Identity Pools enable you to provide temporary AWS credentials. Enabling access to AWS service like S3 or DynamoDB.
Cognito Push Synchronization uses SNS to send a slient push notification of user data updates to multiple devices associated with a single user ID.
Lab: Cognito user access DynamoDB for read
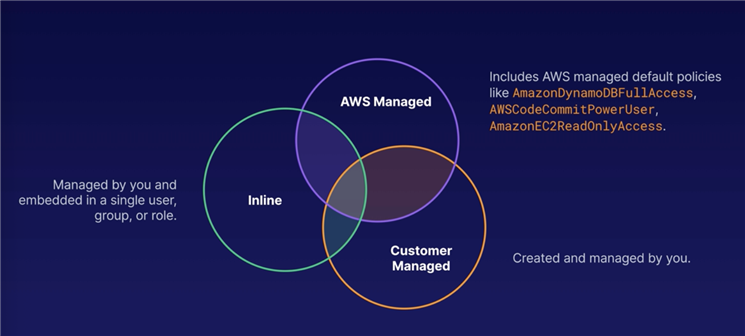
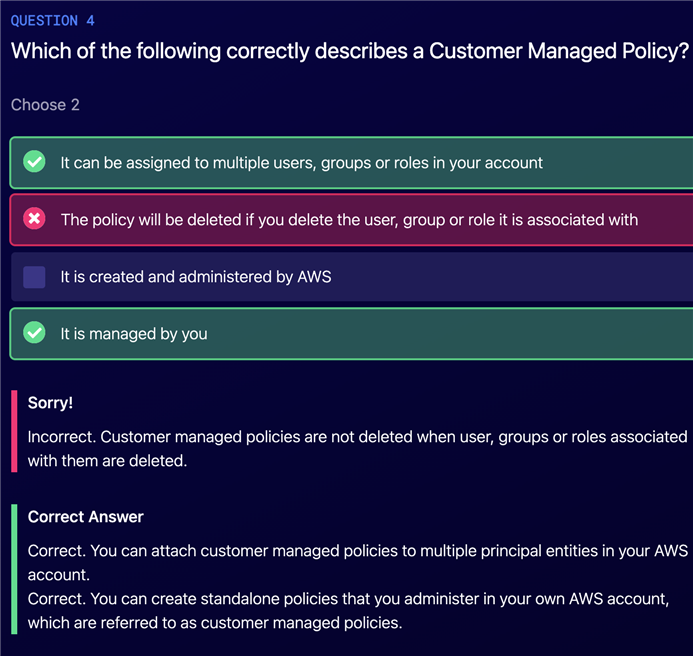
There are three types of IAM policies
An IAM policy created and administered by AWS.
For example:
You can assign appropriate permissions to your users without having to write the policy yourself.
Attach to multiple users, groups, or roles in the same AWS account or across different accounts.
You cannot change the permissions defined in an AWS managed policy.
You cannot find inline policies which created for A user.
In most cases, AWS recommends using manged policies over inline policies.
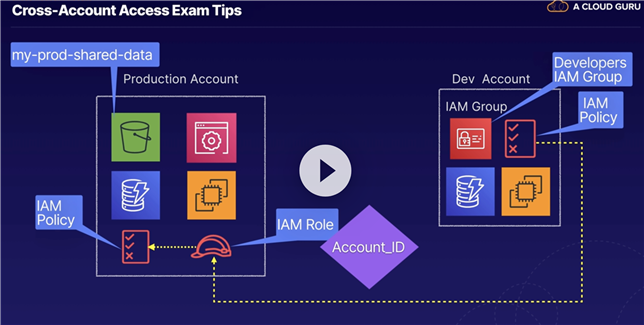
By setting up cross-account access, you can delegate access to resources that are in different AWS accounts, and you don‘t need to create individual IAM users in each account.
Reference: IAM Tutorial: Delegate access across AWS accounts using IAM roles.
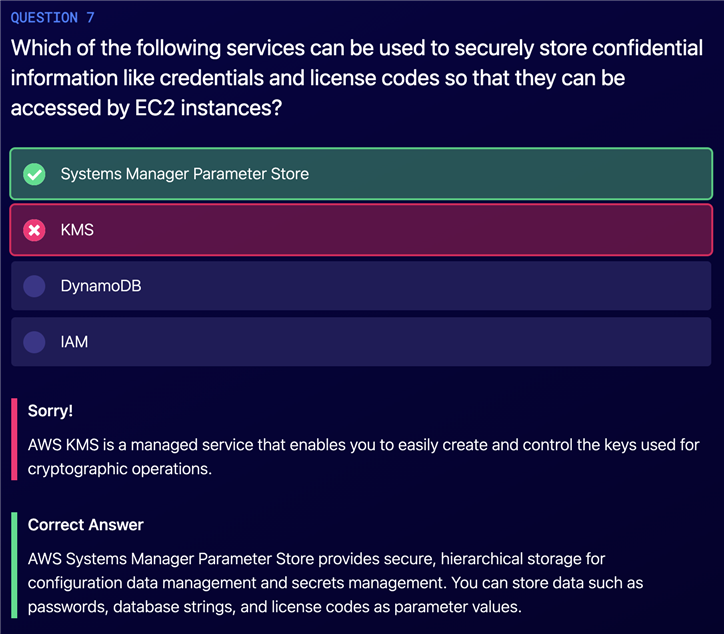

Inline policy will be deleted will the user or group is deleted
原文:https://www.cnblogs.com/Answer1215/p/14692179.html