CA是证书的签发机构,它是公钥基础设施(Public Key Infrastructure,PKI)的核心。CA是负责签发证书、认证证书、管理已颁发证书的机关。
CA 拥有一个证书(内含公钥和私钥)。网上的公众用户通过验证 CA 的签字从而信任 CA ,任何人都可以得到 CA 的证书(含公钥),用以验证它所签发的证书。
如果用户想得到一份属于自己的证书,他应先向 CA 提出申请。在 CA 判明申请者的身份后,便为他分配一个公钥,并且 CA 将该公钥与申请者的身份信息绑在一起,并为之签字后,便形成证书发给申请者。
如果一个用户想鉴别另一个证书的真伪,他就用 CA 的公钥对那个证书上的签字进行验证,一旦验证通过,该证书就被认为是有效的。证书实际是由证书签证机关(CA)签发的对用户的公钥的认证。
math:创建root ca的输入项必须和用户申请时输入的一致才能创建,此为默认值
anything: 无须一致
math 和anything可以进行更改 也可以将默认值改为anything
[root@route1 ~]# yum install -y openssl openssl-libs
[root@route1 ~]# cat /etc/pki/tls/openssl.cnf
[ CA_default ]
dir = /etc/pki/CA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to ‘no‘ to allow creation of
# several ctificates with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
RANDFILE = $dir/private/.rand # private random number file
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
# For the ‘anything‘ policy
# At this point in time, you must list all acceptable ‘object‘
# types.
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[root@route1 ~]# mkdir -pv /etc/pki/CA/{certs,crl,newcerts,private}
[root@route1 ~]#touch /etc/pki/CA/index.txt #生成证书索引数据库文件
[root@route1 ~]# echo 01 > /etc/pki/CA/serial#证书序号文件,不创建无法为用户颁发证书,创建并且给定首次序列号
[root@route1 ~]# (umask 066; openssl genrsa -out private/cakey.pem 2048) #生成不加密的私钥
[root@route1 ~]# echo -e "CN\nsichuan\nchengdu\neast\ndev\ntest.local.com\nadmin@local.com\n\nEOF\n" | openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem#非交互式方式创建rootCA
2.3,创建用户申请证书
[root@route1 ~]#mkdir /data/app1 &> /dev/null
[root@route1 ~]#(umask 066; openssl genrsa -out /data/app1/app1.key 2048)
[root@route1 ~]# echo -e "CN\nsichuan\nchengdu\neast\ndev\napp1.com\nadmin@app1.com\n\n\n\n" | openssl req -new -key /data/app1/app1.key -out /data/app1/app1.csr #非交互式方式创建用户申请证书
2.4,颁发证书和查看
[root@route1 ~]# openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1.crt -days 1000
[root@route1 ~]# cat /etc/pki/CA/certs/app1.crt
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=sichuan, L=chengdu, O=east, OU=dev, CN=test.local.com/emailAddress=admin@local.com
Validity
Not Before: May 1 08:13:21 2021 GMT
Not After : Jan 26 08:13:21 2024 GMT
Subject: C=CN, ST=sichuan, O=east, OU=dev, CN=app1.com/emailAddress=admin@app1.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
[root@route1 ~]# tree /etc/pki/CA/
/etc/pki/CA/
├── cacert.pem
├── certs
│?? └── app1.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│?? └── 01.pem
├── private
│?? └── cakey.pem
├── serial
└── serial.old
4 directories, 9 files
2.5,将证书以及根证书考到本地重命令为crt的
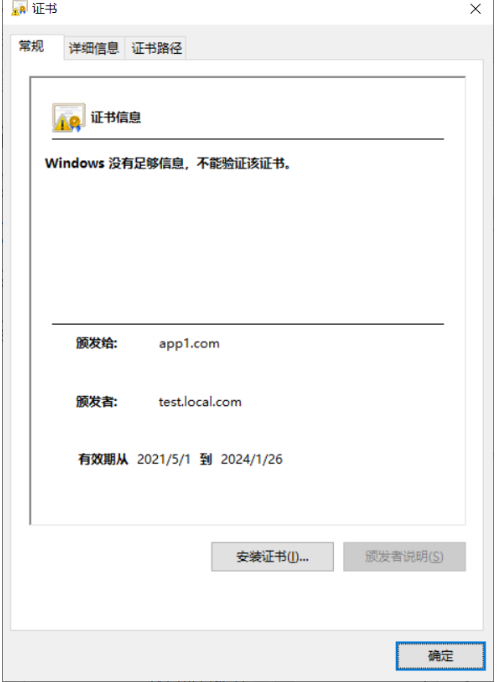
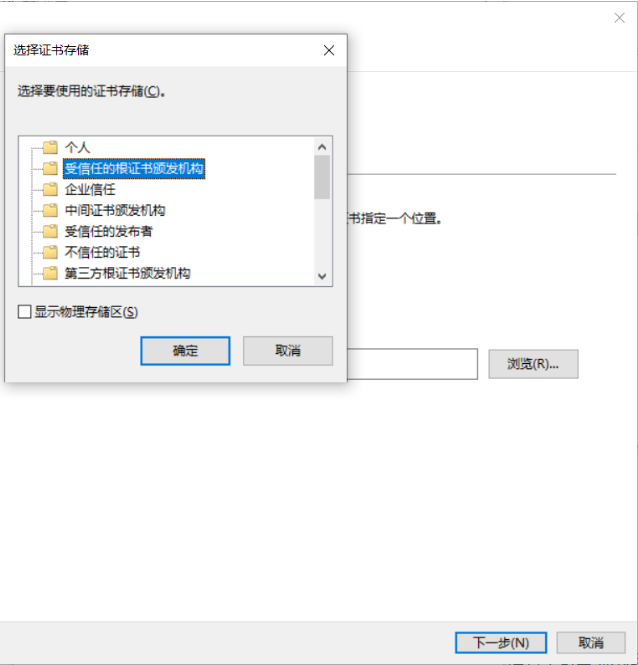
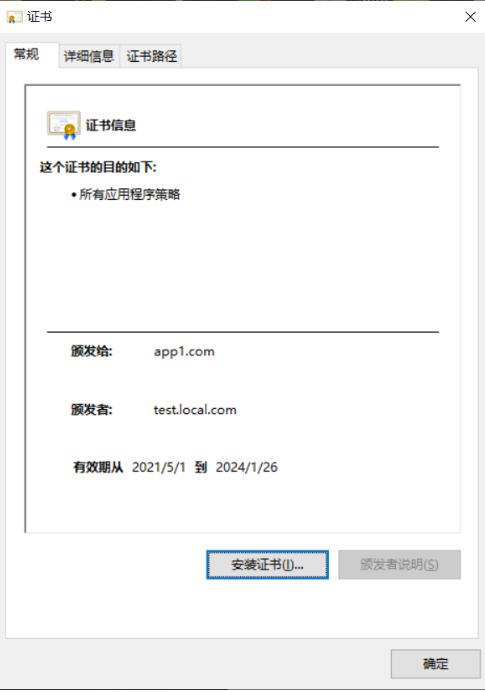
安装根证书后将不会出现无法验证的情况
3,同一个用户申请多个证书 ,将下列值改后可以进行多次申请
编辑cat /etc/pki/CA/index.txt.attr
unique_subject = yes
4,吊销证书,让客户端知道吊销的证书crl下的crl.pem需要进行放在使用客户端公共访问的地方
[root@route1 ~]# openssl x509 -in /etc/pki/CA/certs/app1.crt -noout -serial -subject
serial=01
subject= /C=CN/ST=sichuan/O=east/OU=dev/CN=app1.com/emailAddress=admin@app1.com
[root@route1 ~]# openssl ca -revoke /etc/pki/CA/certs/app1.crt
Using configuration from /etc/pki/tls/openssl.cnf
Revoking Certificate 01.
Data Base Updated
[root@route1 ~]# openssl ca -revoke /etc/pki/CA/certs/app1.crt
Using configuration from /etc/pki/tls/openssl.cnf
Revoking Certificate 01.
Data Base Updated
[root@route1 ~]# echo 01 > /etc/pki/CA/crlnumber
[root@route1 ~]# openssl ca -gencrl -out /etc/pki/CA/crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
[root@route1 ~]# openssl crl -in /etc/pki/CA/crl.pem -noout -text
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: /C=CN/ST=sichuan/L=chengdu/O=east/OU=dev/CN=test.local.com/emailAddress=admin@local.com
Last Update: May 1 09:40:40 2021 GMT
Next Update: May 31 09:40:40 2021 GMT
CRL extensions:
X509v3 CRL Number:
1
Revoked Certificates:
Serial Number: 01
Revocation Date: May 1 09:39:34 2021 GMT
Signature Algorithm: sha256WithRSAEncryption
原文:https://www.cnblogs.com/catastrophe/p/14724512.html