证书生成网站:
https://csr.chinassl.net/index.html
证书会包含一个服务器的域名,或者包含多个域名( 多域名证书,SAN certificater == SubjectAltName Certificater)
自签名证书:服务器生成一个服务器私钥,然后通过私钥生成证书请求文件,正常情况是把 “ 证书请求文件 ” 发给 CA 让其用 CA 私钥生成证书;如果 “ 证书请求文件 ” 用服务器私钥而非CA私钥生成证书,就叫做自签名证书。服务器使用自签名证书就不需要导入 CA 证书。
openssl req 命令主要的功能有,生成证书请求文件, 查看验证证书请求文件,还有就是生成自签名证书。
以下就主要记录一下openssl命令选项的意义,并记录一下简单的命令示例。
openssl req -x509 -newkey rsa:1024 -out client.crt -keyout client.key -batch -nodes
openssl req -new -x509 -newkey rsa:1024 -out client.crt -keyout client.key -batch -nodes
openssl req -new -x509 -key ./rsa_private_key.pem -out client.crt -nodes -batch
openssl req -x509 -key ./rsa_private_key.pem -out client.crt -nodes -batch
openssl req -new -key pri_key.pem -out req.csr
openssl req -in req1.csr -text
openssl req -in req1.csr -noout -pubkey
openssl 有一个默认的配置文件 openssl.cnf,路径:
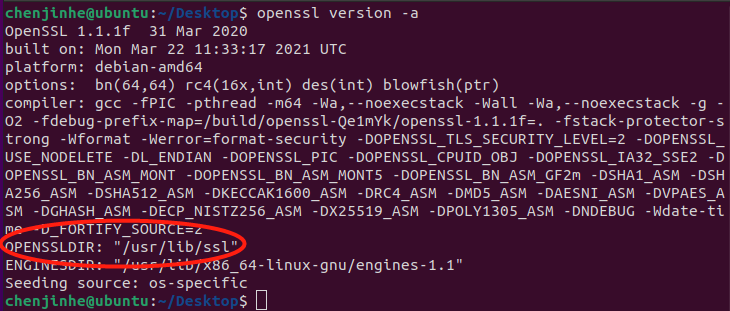
可参考 openssl.cnf 创建自己的配置文件
新建文件 san.conf,内容如下:
[ req ]
default_bits = 2048
default_keyfile = server_privateKey.pem
distinguished_name = req_distinguished_name
req_extensions = req_ext
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Fujian
localityName = Locality Name (eg, city)
localityName_default = Xiamen
organizationName = Organization Name (eg, company)
organizationName_default = none_company
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = IT
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64
commonName_default = localhost
[ req_ext ]
subjectAltName = @alt_names
[alt_names]
DNS.1 = god1
DNS.2 = god2
DNS.3 = 192.168.0.1
DNS.4 = 127.0.0.1
运行以下命令:
openssl req -new -nodes -out myreq.csr -config san.conf -batch
或者
openssl genrsa -out server_privateKey.pem 2048 openssl req -new -out myreq.csr -key server_privateKey.pem -config san.conf -batch
查看证书请求文件
openssl req -text -noout -in myreq.csr
生成带有 SAN 域名的证书
openssl x509 -req -days 365 -in myreq.csr -signkey server_privateKey.pem -out server.crt -extensions req_ext -extfile san.conf
生成不带 SAN 域名的证书
openssl x509 -req -days 365 -in myreq.csr -signkey server_privateKey.pem -out server.crt
原文:https://www.cnblogs.com/god-of-death/p/14934351.html