While network policy designs are out of scope for this reference architecture, it is a core feature of Calico and thus is mentioned here to provide initial guidance.
Calico enforces 3 types of policies:
The Calico CRDs are more capable than the Kubernetes API, however the Kubernetes API policies are portable, should migration to another CNI-plugin happen in the future. Many organizations want to enforce default policy to every namespace. Normally, administrators need to ensure default policy rules are deployed to every namespace. This can be challenging over time as changes to the default policy rules require changes to every namespace. Calico’s GlobalNetworkPolicy enables creating cluster-wide policies that impact every workload based on label selectors. Cluster-wide policy set in GlobalNetworkPolicy can be overwritten by NetworkPolicy (namespace scoped) from both the Kubernetes API and Calico CRD. The example below enforces a global default deny-all policy:
# This GlobalNetworkPolicy uses Calico‘s CRD # (https://docs.projectcalico.org/v3.5/reference/calicoctl/resources/globalnetworkpolicy) apiVersion: projectcalico.org/v3 kind: GlobalNetworkPolicy metadata: name: global-deny-all spec: # order controls the precedence. Calico applies the policy with the lowest value first. # Kubernetes NetworkPolicy does not support order. They are automatically converted to an order # value of 1000 by Calico. Setting this value to 2000, provides flexibility for 999 additional # GlobalNetworkPolicies to be added and ensures Kubernetes namespace-scoped policies always take # precedence. order: 2000 types: - Ingress - Egress # egress network rules egress: # Allow all egress traffic from kube-system. - action: Allow destination: {} source: namespaceSelector: name == ‘kube-system‘ # Allow egress DNS traffic to any destination. - action: Allow protocol: UDP destination: nets: - 0.0.0.0/0 ports: - 53 # ingress network rules ingress: # Allow all ingress traffic for the kube-system namespace. - action: Allow destination: namespaceSelector: name == ‘kube-system‘ source: {}
The policy above denies all pod network traffic by default, except for workloads in kube-system and DNS communications (UDP:53). With this in place, a namespace could open up ingress traffic to port 80 for any workload in it, by adding the following NetworkPolicy:
apiVersion: networking.k8s.io/v1 kind: NetworkPolicy metadata: name: team-netpol namespace: org-1 spec: podSelector: {} policyTypes: - Ingress - Egress ingress: # allow all inbound traffic on port 80 - from: ports: - protocol: TCP port: 80
指定pod标签访问
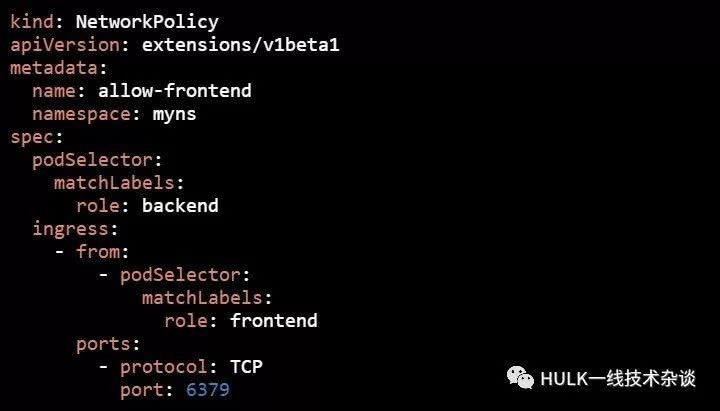
我们要对namespace为myns,带有"role: backend"标签的所有pod进行访问控制:只允许标签为"role: frontend"的Pod,并且TCP端口为6379的数据流入,其他流量都不允许。
指定namespaces标签访问
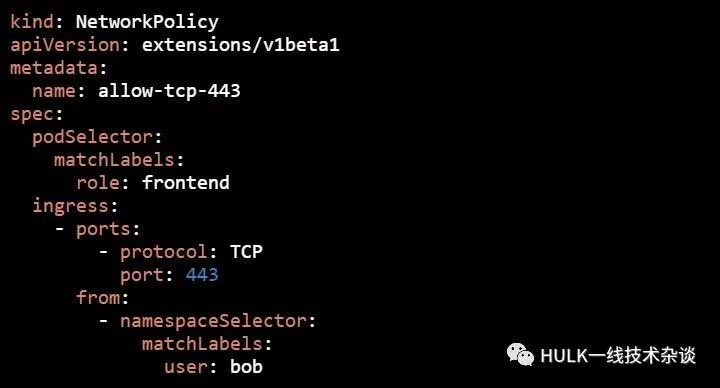
我们要对标签为"role: frontend"的所有Pod进行访问控制:只允许namespace标签为"user: bob"的各Pod,并且TCP端口为443的数据流入,其他流量都不允许。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all-egress
namespace: cs1
#Apply to cs1 namespace, do not write namespace to default
spec:
podSelector: {}
ingress:
egress:
#Define the outbound rule. No policy is written here to deny it all.
policyTypes:
- Egress
- Ingress
#If you have Egress, you will define an outbound rule. If you do not write Egress, you will have the default pass. Ingress is inbound in the same way
#It‘s recommended that you write both and use "podSelector:" to control passage
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all-egress
namespace: cs1
spec:
podSelector: {}
ingress:
- {}
#This means that all traffic is allowed in the "ingress" direction
egress:
- {}
#This means that all traffic is allowed in the "egress" direction
policyTypes:
- Egress
- Ingress
This network policy only works with namespaces and the host is still accessible
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all
namespace: default
#Act only on default namespace
spec:
podSelector:
#Match the pod range if it matches all the POD inputs‘{}‘for that namespace
matchLabels:
access: "true"
#Label with access=true in matching POD
policyTypes:
- Ingress
- Egress
ingress:
egress:
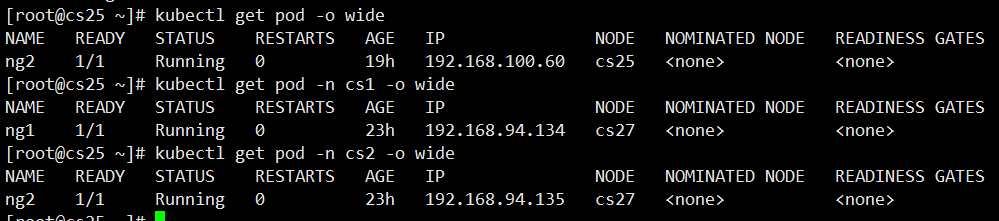
#IP for each cs container shown above
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all
spec:
podSelector: {}
policyTypes:
- Egress
- Ingress
ingress:
egress:
- to:
#Note: egress uses to, ingress uses from
- ipBlock:
cidr: 192.168.0.0/16
#Release 192.168.0.0/16 Network
except:
- 192.168.94.134/32
#But do not include this ip
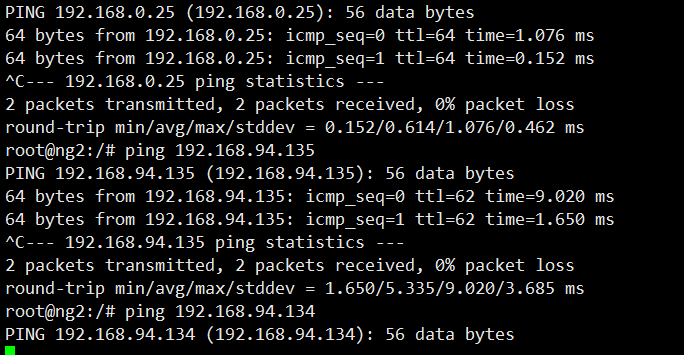
Exc entering pod can see ping192.168.94.134 This IP is not available
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: namespace-allow
namespace: default
spec:
policyTypes: ["Ingress"]
podSelector: {}
ingress:
- from:
- namespaceSelector:
matchLabels:
name: cs1
#Indicates that only namespaces typed "name=cs1" are allowed to enter
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: namespace-allow
namespace: default
spec:
policyTypes: ["Ingress","Egress"]
podSelector: {}
ingress:
- from:
- namespaceSelector:
matchExpressions:
- key: name
operator: In
values: ["cs1","cs2"]
#The default namespace ingress can be communicated within brackets
#Indicates that the namespace has the label name=cs1,name=cs2 to communicate with the default namespace
7 based on pod label
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: namespace-allow
namespace: default
spec:
policyTypes: ["Ingress"]
podSelector: {}
ingress:
- from:
- podSelector:
matchLabels:
access: "true"
#Allow pod notes to have access=true traffic
原文:https://www.cnblogs.com/dream397/p/15015427.html